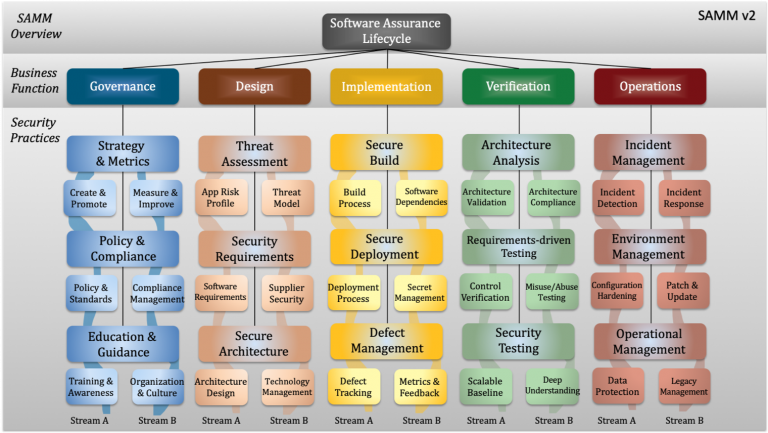
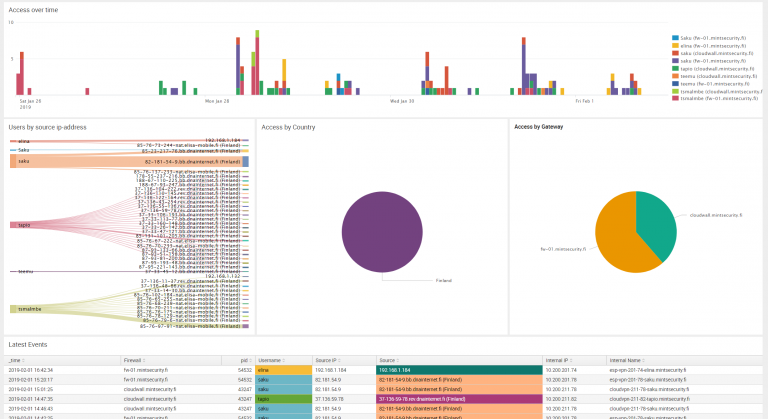
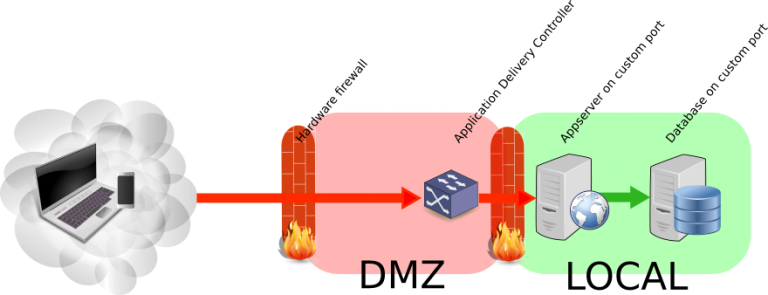
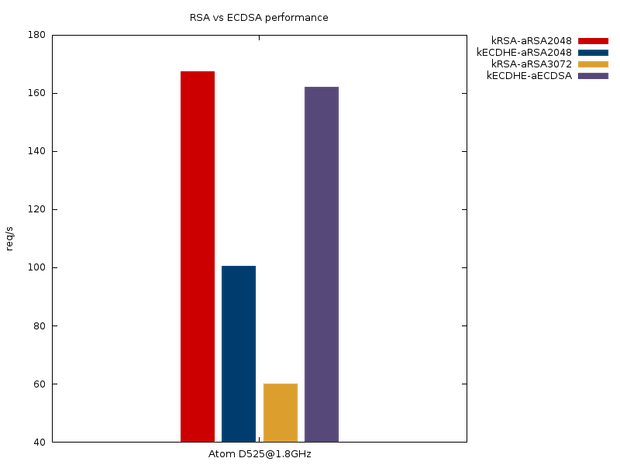
Nyt on oikea hetki rakentaa “inhimillinen palomuuri”
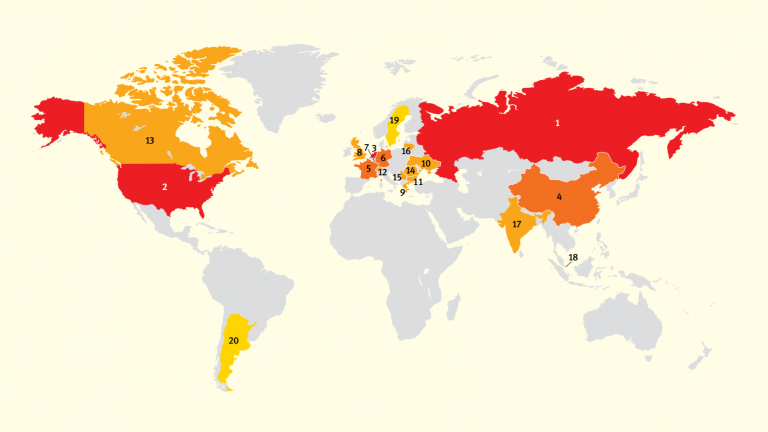
Kun tarkastellaan yrityksen tai organisaation kyberturvallisuustrategiaa, on siihen nykyään myös sisällytettävä yrityksen työntekijät, jotka ovat kyberpuolustuksen ns “inhimillinen osatekijä” (human element). Voidaan varmaan olettaa, että