Vulnerability management
Cyber, SecOps & Architectures
Vulnerability management in brief
Vulnerability management is an area of IT risk management that searches for vulnerabilities in information systems and assess the related business risk.
Dozens or even hundreds of vulnerabilities are often found in vulnerability scans, even in small environments. Such a situation can be crippling, and no vulnerabilities will never end up actually being fixed.
With our help, you can build an easy-to-adopt process to take control of the scanning, prioritizing, action-planning and implementation cycle.
You may have already adopted a certain vulnerability scanner, or then not – it doesn’t matter. Our process approach is not associated to using a particular scanner.
What Mint Security delivers
Remove the burden that managing vulnerabilities in your infrastructure can cause. Our experienced team of experts can help you:
- Define a systematic and continuous approach and processes to finding and managing vulnerabilities
- Get complete visibility of assets and weak spots in your systems and network
- Create prioritized mitigation task lists that you can put into action right away
- Adapt your vulnerability scanning and patch management practices to changes in your environment
- Generate reports that are optimised for your environment, are made to the desired audience and meet compliance requirements
Vulnerability management is twofold – a vulnerability scanner is a technical tool, whereas vulnerability management is a process.
Customer needs and challenges to be solved
Devices, services and other assets connected into your network may contain serious vulnerabilities that put the confidentiality of your data at risk. There are constantly more and more vulnerabilities found and trying to keep up with them can be an overwhelming task that requires resources, time and money wasted.
We help you create policies to scan your network environment without disrupting the daily work, to find vulnerabilities in network devices, servers, applications, and databases. We review scan results, identify false positives and prioritize corrective actions based on your business environment. We’ll create a report that prioritizes the necessary corrective actions and provide you with useful metrics so you can report back to those who need to know.
We employ professionals with required skills and experience to help you flesh out your goals and help reduce identified risks. With our help, you can transfer your own resources to other critical tasks and focus on the essentials.
Standards and best practices
Here is a brief reference to various standards we are able to help you comply with our services.ISO27001 on vulnerability management
- A.12.6.1 Management of technical vulnerabilities
- A.12.6.2 Restrictions on software installation
ISO27001 on managing updates
- A.8.1.1 Inventory of assets
- A.12.5.1 Installation of software on operational systems
- A.14.2.2 System change control procedures
- A.14.2.4 Restrictions on changes to software packages
PSD2
The European Banking Authority has mandated the need for vulnerability management and vulnerability scanning in their guideline 7 as follows: “include vulnerability scans and penetration tests adequate to the level of risk identified with the payment services.”PCI-DSS
Requirement 6 states that the organization should ”Establish a process to identify security vulnerabilities, using reputable outside sources for security vulnerability information, and assign a risk ranking to newly discovered security vulnerabilities.”OWASP TOP-10
For web applications, OWASP Top-10 is being commonly referred to.More details about our methods and tools
Vulnerability management process development begins with a brief initial analysis of your situation. We’re hands-on type of people, but also familiar with reading heavy and fragmented documentation. Anything that gets us into your situation.
Current state analysis
Steps involved:
- Identify the amount of assets involved
- Identify the overall complexity of the network
- Identify the frequency of scanning (=how often are you able to process new findings)
- Define the scope (if not the whole organization)
- Define whether the target is workstations, servers & infra or all assets in the network
- Define if the process will be (partially) outsourced
- Contractually relevant issues
Next steps
If you’re not quite sure what you need, or don’t know what you’re capable of, more thorough analysis is needed. The best way to approach vulnerability management is to create an assessment of the status quo, as well as the target status according to an industry standard CMMI maturity model. We can do that for you.
Once maturity and needs are known, budgeting will be considered. Not the other way around. What you get with the money given, how do you get most value out of it and how you should implement the security controls.
We offer our services in two stages. The first part consists of surveying, process design and implementation of policies and practices. The second part is a continuous service, where we monitor the situation, assess vulnerability-related security risks and produce detailed analysis where required and ICT risk management.
Mint Security is successfully using Holm Security VMP for vulnerability scanning. We have built and implemented the process experience and this tool.
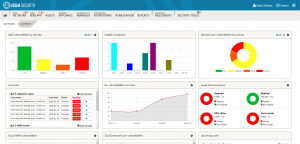
Holm Security VMP
Network Scanning Web App Scanning Human Behaviour Scanning Holm Security Vulnerability Management Platform Protects your organisation by detecting vulnerabilities before any malicious person or organisation
- ISO27001 & ISO27002
- PSD2
- PCI-DSS
- OWASP TOP-10

Secure Your Cloud with Holm Security
Cloud Scanning -toiminto on Holm Securityn haavoittuvuuksienhallinnan uusi ominaisuus, joka automatisoi riskien tunnistamisen pilvi-infrastruktuureissa. Uusi toiminto kattaa Infrastructure as a Service (IaaS), Software as a Service (SaaS) ja Platform as a Service (PaaS) -palvelumallit.
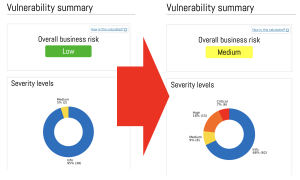
Boost vulnerability scans using authentication
When vulnerabilities are scanned from the perspective of an outside attacker and without actually logging in to the target system(s), only a limited and narrow picture of exposure to threats can be found. For a better picture, it is a good idea to log in with the right kind of credentials.
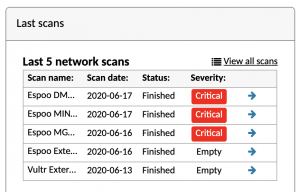
Holm Security VMP and ISO 27001
How much common ground is shared between technical vulnerability scanners and the de facto global information security standard? Quite a lot, actually. In this blog post we examine how Holm Security VMP platform meets ISO 27001 requirements for detecting vulnerabilities in an organization’s information systems, assessing the involved risks and taking corrective actions.