SWIFT CSP assessments
Auditing & IT-Risk Management
SWIFT CSP assessments in brief
What we deliver
In the SWIFT CSP context, Mint Security Ltd is an independent external organization with required experience in cyber-security assessments and capability to conduct independent CSP assessments. Our skilled personnel hold multiple security industry certifications and have extensive experience of working with financial institutions and other industries as well. We keep our SWIFT-training up to date on a yearly basis. You may rest assured that our CSP knowledge and level of awareness is more than adequate.
Customers' needs and challenges to be solved
An independent assessment can be conducted internally — by the second or third line of defense (compliance, risk management, or internal audit functions) — or an effective equivalent that is totally independent of the first line of defense (such as the CISO office).
However, to truly get a high-quality, consummately free-of-conflict outlook of the status of your organization’s SWIFT CSP controls and procedures, consider an external company (like us!) to perform the independent assessment.
Our methods and tools
We strive to comply with the official SWIFT guidelines for the independent assessment process.
To prepare to conduct a well-organised, comprehensive, and smooth assessment, we begin by identifying the objectives and the scope of work.
The scope of work generally states at least:
- Points of contact
- Assessment methodology
- Testing methods
- Expected deliverables and format
- The advisory controls that will be assessed
- Responsibilities of each party
- Policy for reusing existing and relevant assessments, as well as any other user specific requirements
- Specific retention constraints of evidence
We establish a draft schedule listing the activities, duration, and required resources per task. A dedicated project manager will be assigned for each assessment, who will monitor the progress of the assessment.
We conduct interviews with the SWIFT user’s stakeholders and collect necessary information to understand the SWIFT environment. User documentation is analysed to identify the level of adherence to control objectives and mitigating risk drivers. We then review the provided documents and categorise them based on their relevance to the CSP controls. At this point, additional documents are requested for — if required.
We use a risk-based approach to assess the user’s compliance with the CSP controls, regardless of the control implementation method.
After the review and interviews, we produce a draft assessment report and the necessary spreadsheets and discuss and agree on their contents with the SWIFT user. It is mutually important to ensure the accuracy of conclusions made, and to get inputs from the user on any missing/incorrect information.
To conclude, we produce the Independent Assessment final report.
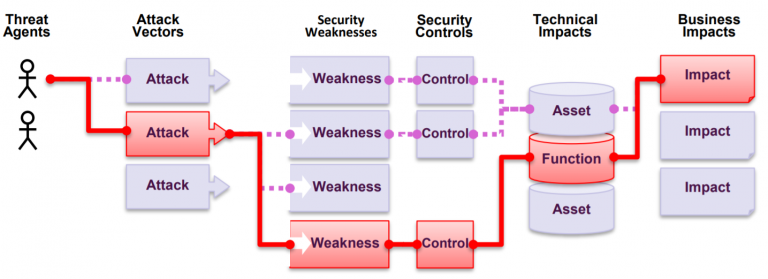
What is pentesting?
A common tool used to assess the security of a web application is penetration testing. Known also as pentest. Pentest is a “legal” simulated attack that seeks to use an application in a way that could be harmful to either the system, the data in the system, or the people who use the system.
