OSINT
Auditing & IT-Risk Management
OSINT in brief
OSINT stands for Open Source Intelligence. The purpose of intelligence is to form context and entity of non-confidential information — a snapshot that often reveals more than the company actually wants to. Combining data and thereby drawing conclusions can directly lead to exposure of weak points and technical or non-technical vulnerabilities.
What we deliver
At the base level of our service, we utilize widely available public information sources and databases, keeping an eye on our customer’s assets. We can track the company from many different starting points; we can start from the company’s website or the CEO’s email address. Together with our client, we agree on the correct angle of approach, collect data and produce standard reports on a monthly basis. The service develops on a customer-by-customer basis depending on the customer’s public visibility, business development, the services offered, the competitive situation and various threat models.
In-depth services allow us to monitor more closely the attack methods and campaigns known around the world. We model the company’s assets with necessary level and accuracy, and build a continuous snapshot and situational database from which we can create reports and continuously monitor the situation.
If necessary, we also combine our customers’ existing paid and commercial tools and data sources with our services, or we license the commercial data sources to be agreed upon together in the service package.
We can also conduct one-time OSINT audits.
Customer needs and challenges to be solved
Open source intelligence is also used by many hostile parties. The goal of potentially hostile OSINT organizations should be to be one step ahead — to know for themselves what others may already know. Open data sources contain a huge amount of information. The challenge is who collects this information, where to find it and how reliable it is, and how it affects the company’s security and risk management.
The purpose of our service is to find unknown vulnerabilities in a company’s defense that enables abuse, scams and attacks.
Our methods and tools
We keep an eye on the company’s publicly visible assets. The assets will not be actively scanned, so tracking does not create a significant burden on the network. Most of the data collection is done from publicly available data sources. Visibility is achieved in areas where visibility is normally poor or non-existent, or requires unreasonable human labor.
As part of our service we examine the results and strive to find and report anomalies and correlations. Together with the customer, we also remove false or misleading findings. Over time, misconceptions diminish.
It is difficult to predict in advance exactly what we will find. Here are some common examples:
- Registered but forgotten domains
- Abandoned and forgotten services
- Domain registrations and registrants
- Domains that try to trick users into appearing as a corporate domain
- Social media accounts set up in the company name
- DNS information such as SPF / DKIM validity
- WHOIS information
- Publicly known and exploitable vulnerabilities
- Shared public resources (and with whom they are shared)
- Servers used to send email (MX records)
- Externally downloadable Javascript files
- Services that accept password login
- Services that allow you to download files
- Hacked email addresses
- Open ports
- AS information
- PGP keys
- Public code repositories
- SSL certificates (also expired)
- Storage services (such as buckets)
- Apps in the app stores
Spiderfoot is a search engine – or scanner – that takes advantage of dozens of different sources of information. Not all data sources are free.
The strength and weakness of Spiderfoot lies in the massive amount of data it holds.
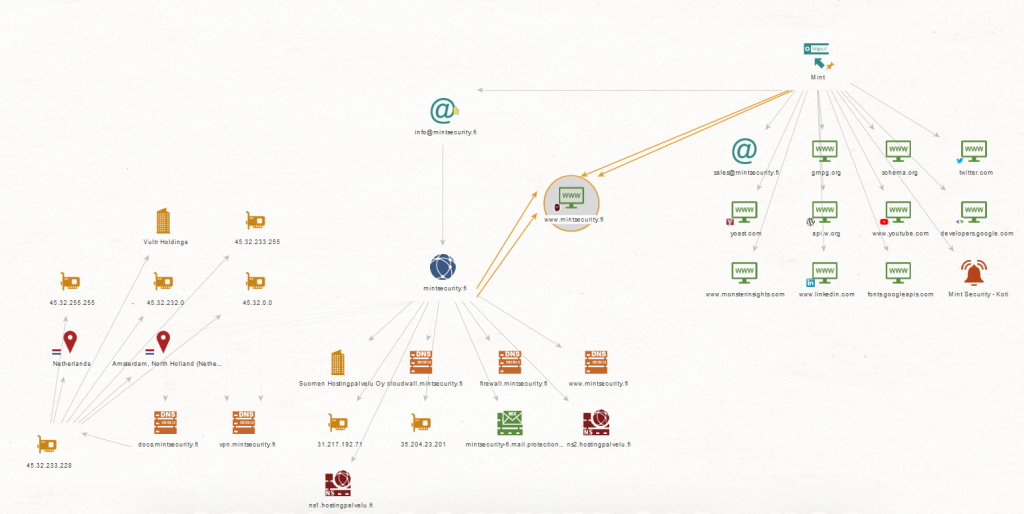
Maltego is a tool for collecting, analyzing and visualizing information found in open data sources. Maltego provides both continuous monitoring and case-by-case analysis.
Maltego’s strength is in the analysis of data and information pathways from different perspectives – as well as data enrichment.
OpenCTI is a database that combines organization’s assets with, among other things, vulnerabilities, malware, malware campaigns, malicious tools, and various hacker groups.
OpenCTI is a tool for mapping the total threat surface of a company and for the continuous maintenance of this entity in the long run.
Red Teaming and Recon
Recon and red teaming can be done separately, but they also work hand in hand. It may be a good idea for a company to do a thorough recon to understand the adversaries view on the organization – and this not only in the technical sense.
