- Instantly identify infected hosts
- Uncover data exfiltration channels
- Threat hunt with high fidelity alerts
Accurately identify security threats
Hundreds of security teams around the world rely on AlphaSOC to uncover malware, data exfiltration, and policy violations within their networks. Our cloud and on-premise analytics tools instantly provide actionable alerts.
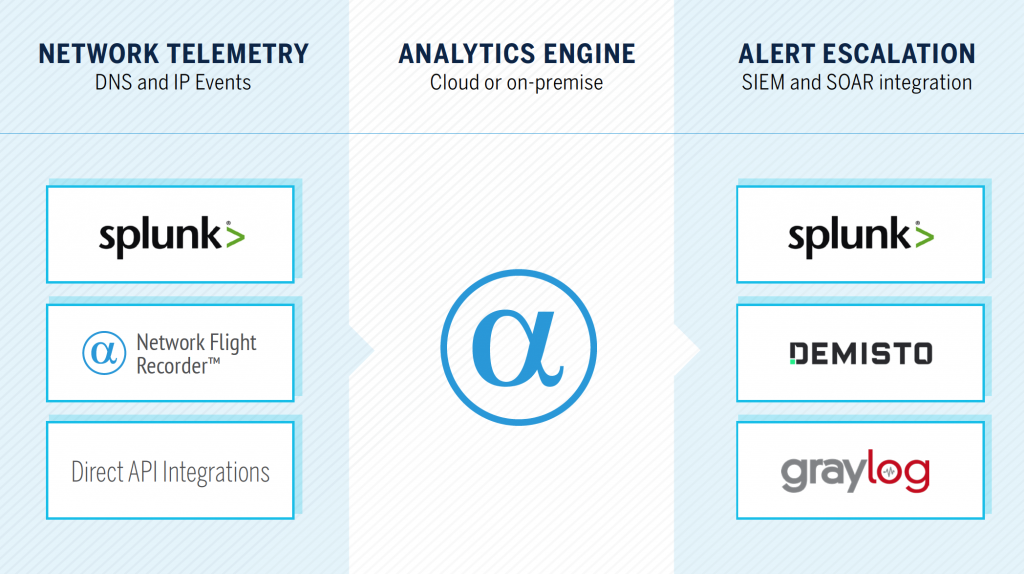
Analytics tools
Our Splunk applications instantly score network logs to identify emerging threats and anomalies within networks. Non-Splunk users can access our API directly and create custom integrations with our SDK.
In brief
 The AlphaSOC Analytics Engine performs deep investigation of the material, such as:
The AlphaSOC Analytics Engine performs deep investigation of the material, such as:
- Volumetric and quantitative analysis (counting events, identifying patterns)
- Resolving FQDNs and domains to gather context (identifying sinkholes and ASN values)
- Breakdown and analysis of each FQDN label (i.e. hostname, domain, TLD)
- Gathering of reputation data (e.g. WHOIS and associated malware samples)
- Categorization of traffic based on known patterns (e.g. C2, P2P, VPN, cryptomining)
- Uncovering C2 callbacks and traffic to known sinkholes
- Tor, I2P, and Freenet anonymized circuit identification
- Cryptomining and JavaScript cryptojacking detection
- Flagging traffic to known phishing domains
- Brand impersonation detection via Unicode homoglyphs and transpositions
- Flagging multiple requests for DGA domains, indicating infection
- DNS and ICMP tunneling and exfiltration detection
- Alerting of lateral movement and active network scanning
- Policy violation flagging (e.g. third-party VPN and P2P use)
We also keep your data secure
The people at AlphaSOC take security very seriously and understand how important the responsibility of safeguarding data is to customers.- Data encryption at-rest using AES256
- Transport encryption using TLS 1.2+ and AEAD ciphers
- Strong authentication via Yubico hardware and an internal CA
- System architecture and source code audited annually by a third-party
Telemetry used by SOC analysts to identify compromised hosts stems from IDS sensors, EDR and antivirus running on endpoints, and SIEM platforms which aggregate and process logs from firewalls and other security apparatus.
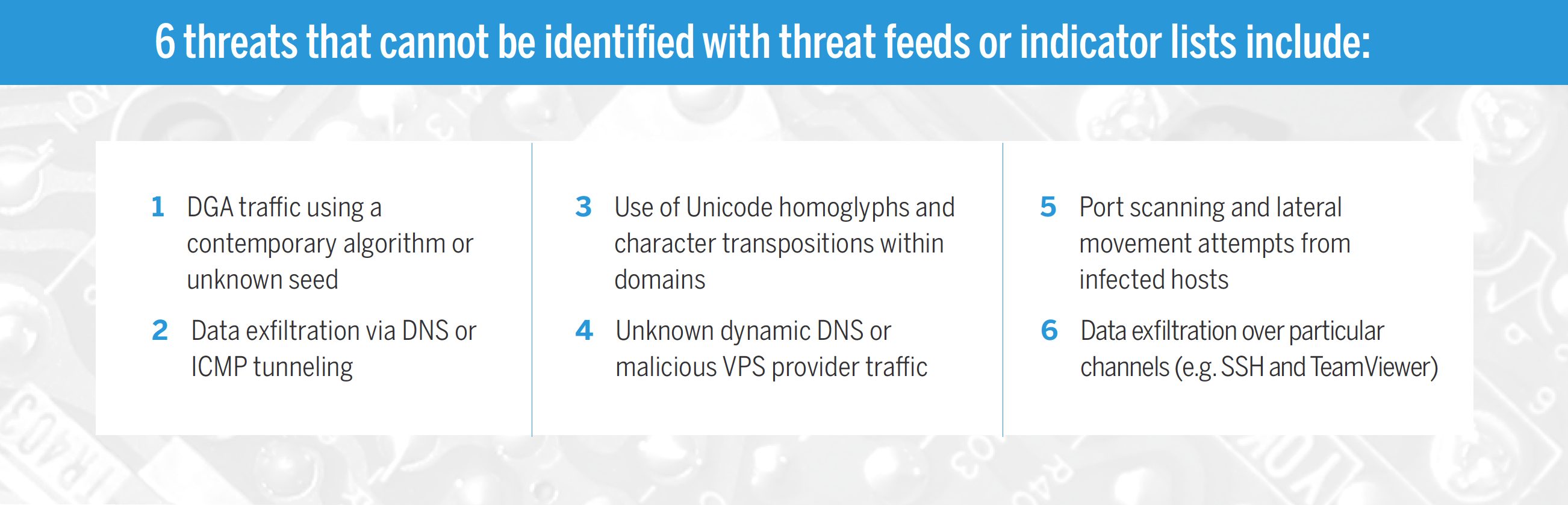
An entire industry exists to serve customers with threat feeds to identify infected systems, and help security teams to identify malicious actors and campaigns using known signatures (e.g. IP addresses, domain names, and hashes).
Indicator lists are commonly used in a one-dimensional fashion:
- Raw data is correlated with a feed, and an alert is generated if there’s a hit
Many adversaries are aware of this level of maturity within enterprise SOCs. To bypass detection they simply avoid re-use of IP addresses, domain names, executables, and other materials between campaigns. There are a plethora of threats that cannot be identified through one-dimensional correlation alone.
Introducing the Analytics Engine
To defend against unknown malware campaigns and determined attackers, security teams are turning to security analytics to dig deeper into their data. Building a robust analytics stack and performing such heavy lifting in-house is often cost prohibitive, and so hundreds of security teams turn to our Analytics Engine (AE) to uncover anomalies within large environments.
AlphaSOC AE performs fast multi-dimensional analysis of raw DNS, IP and HTTP network events via an on-premise or cloud analytics instance. Individual classifiers and features that we have built and refined include:
- Volumetric and quantitative analysis (identifying patterns and spikes)
- Resolving FQDNs and domains to gather context (e.g. sinkhole traffic)
- Breakdown and analysis of each FQDN label (i.e. hostname, domain, TLD)
- Gathering of reputation data (e.g. WHOIS and sandboxing engine scores)
- Categorization of traffic based on known patterns (e.g. C2, P2P, VPN)
- Tracking of state and traffic patterns (uncovering lateral movement)
Data Ingest
DNS, IP, and HTTP events can be gathered and sent to the Analytics Engine via:
- Network Behavior Analytics for Splunk (native integration)
- Network Flight Recorder (NFR — our lightweight open source agent)
- Direct API integration with our cloud service or on-premise instance
- Telemetry stored within Amazon S3 (e.g. Cisco Umbrella, CrowdStrike, VPC flow logs, and so on)
- Elastic Packetbeat and Logstash
Alert Escalation
Upon processing, AlphaSOC AE generates alerts describing anomalies (e.g. beaconing to a young domain, or a spike in ICMP traffic indicating tunneling) and known threats (e.g. C2 callbacks or Tor circuit setup). NFR retrieves alerts in JSON format and send them via Syslog into any SIEM or SOAR platform.
Our native integration for Splunk provides multiple dashboards to support threat hunting and investigation of anomalies. Policy Violations (e.g. P2P activity, third-party VPN use, and potentially unwanted programs) can be quickly escalated via ticketing (e.g. ServiceNow), freeing SOC analyst cycles to focus on hunting and triage of compromised hosts.
Use Cases
Multi-dimensional analytics solves many difficult use cases and addresses blind spots that security teams face. We are able to instantly flag the following threats via the analytics engine:
- DNS and ICMP tunneling and exfiltration of data
Phishing attacks using new permutations and homoglyphs of brands - C2 callbacks, IRC traffic, and anonymized circuits (e.g. Tor, I2P, Freenet)
- Lateral movement and odd egress traffic patterns indicative of infection
- Cryptomining and cryptojacking attacks
Traffic to unknown / new dynamic DNS and hosting provider domains - Policy violations (e.g. unwanted programs, third-party VPN, and P2P use)
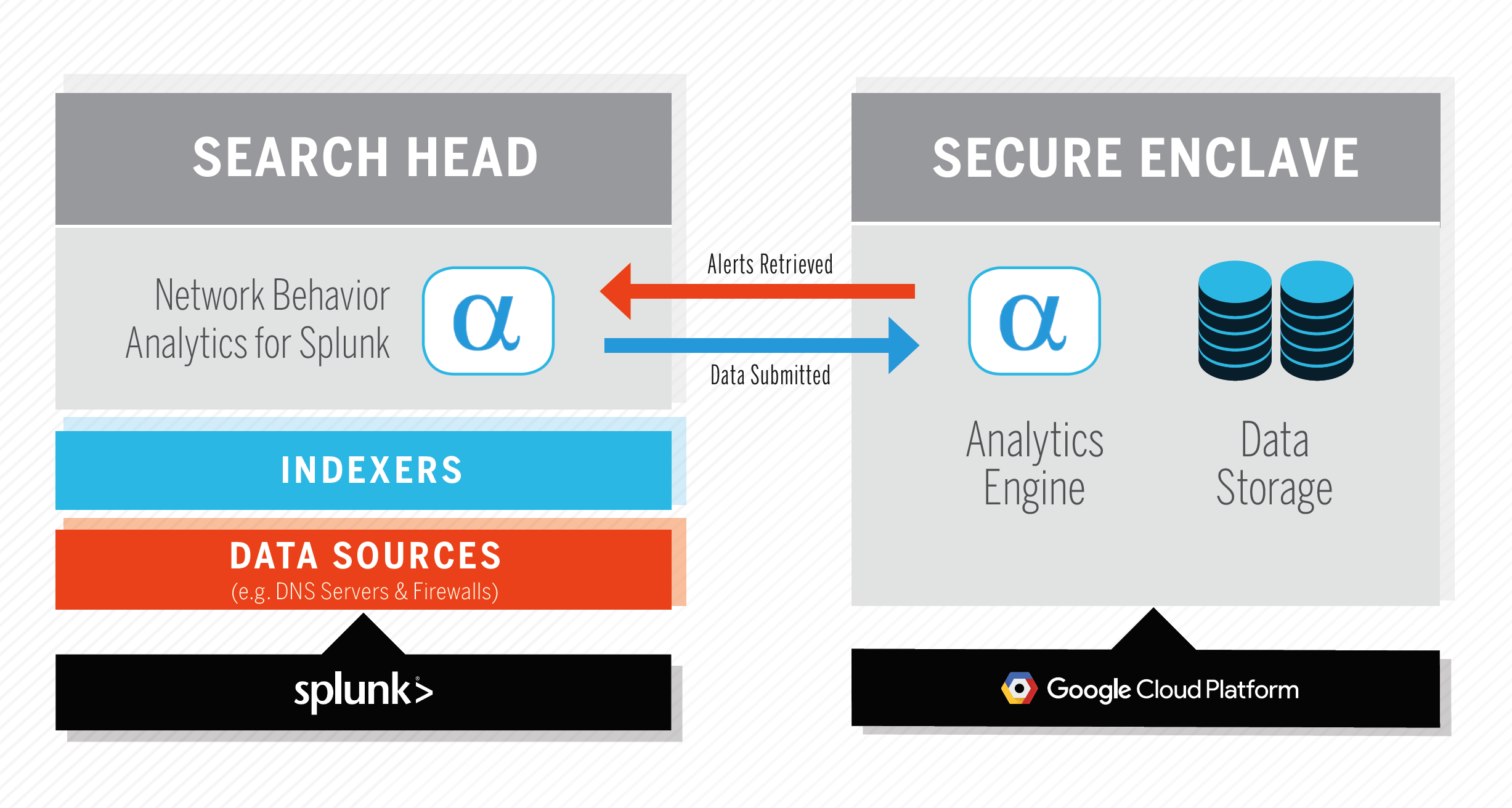
Use Network Behavior Analytics for Splunk to quickly uncover infected hosts and threats to your environment. The Splunk app processes and submits network telemetry (CIM-compliant DNS, IP, and HTTP events) to the AlphaSOC Analytics Engine for scoring, and retrieves security alerts and data for investigation. The system architecture is shown below.
Want to try?
Download the app from Splunkbase. An activated AlphaSOC API key provides 30 days of unrestricted access to alerts while you evaluate the product. For assistance or a longer trial, contact us.
What data do I need?
The more data you have, the better the results will be. We can leverage the following
- Firewall logs
- Netflow data
- DNS logs
- Http outbound proxy logs
For AlphaSOC to work, you need at least one of the above. AlphaSOC uses the CIM model, hence logs that are properly tagged will automatically be used.
How to install and configure
Please refer to the up to date manuals: https://www.alphasoc.com/docs/nba-introduction
What about my data?
We do processing in the cloud. But do not fear, you can have an on-premises analytics engine.
Professional Services
Mint Security provides you with assistance and professional services.
- Onboarding necessary logs to run AlphaSOC
- Creating custom alerts and integrations – JIRA, Alert Manager, Slack, ….
- Installing on-premises engine
- Analysing results and assessing threats
- First line all round support in Finnish, English and Swedish – in a time zone that suits your needs
Sales and licensing
We sell licenses, In Euros.
AlphaSOC users submit telemetry from network sources including firewalls, web proxies, DNS servers, and intrusion detection systems.
The Analytics Engine performs multi-dimensional processing of network telemetry to highlight anomalies and bring them to your attention.
Security teams use our integrations for SIEM and SOAR platforms to escalate high fidelity, actionable alerts for triage and threat hunting purposes.
Featured blogs

Uncover Detection Blindspots with Network Flight Simulator
Today at AlphaSOC we released Network Flight Simulator (flightsim) 2.2.1, which is our free, open source adversary simulation tool. This latest release includes a number of new modules that security teams can use to instantly evaluate detection and response coverage within SIEM and SOAR tools.
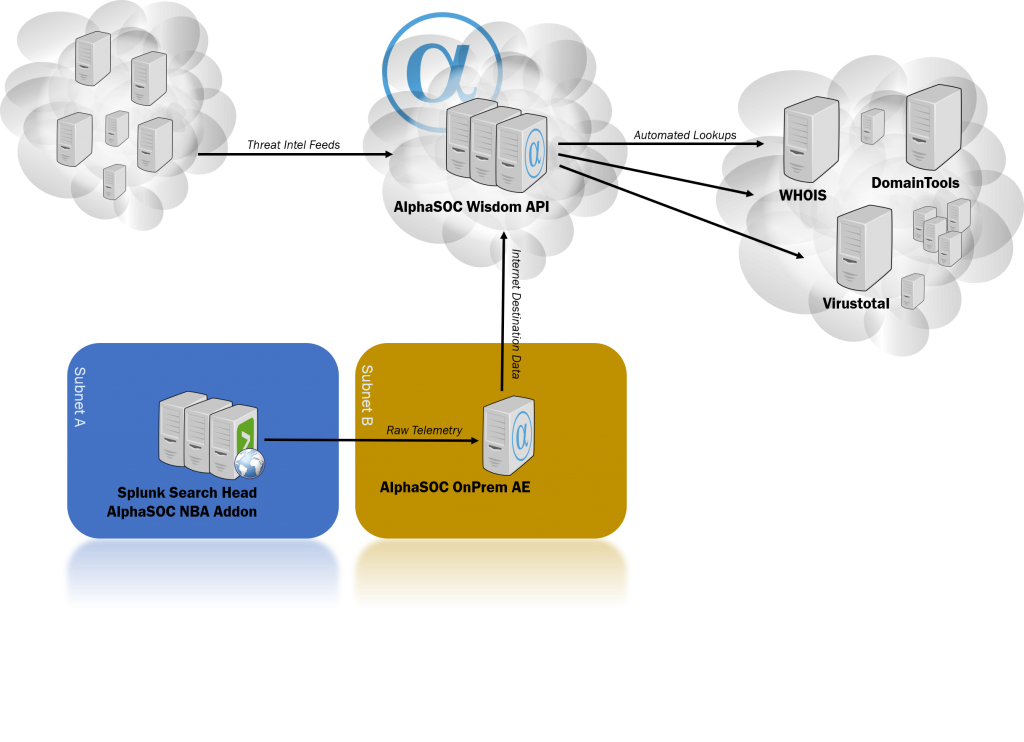
Different AlphaSOC deployment options
“The cloud!” somebody shouts out loud. “This means my data is sent to the cloud – my precious telemetry data that in the hands of the bad guys could reveal too much about myself!”. This is correct. And for the sake of transparency, let’s have a look at what actually goes on behind the scenes.
Mint Security to resell AlphaSOC solutions
Mint Security will start to resell and support the AlphaSOC product line in Finland and Europe.
Automating the Hunt
Through Network Behavior Analytics for Splunk and our native integrations for Demisto and Graylog, we instantly enrich network indicators (FQDNs, URLs, and IP addresses) to provide security teams with hunting material.
