- Löydä saastuneet työasemat
- Havaitse vuodot ja muu luvaton käyttö
- Vastaanota korkealaatuisia uhkahälytyksiä
Löydä tietoturvauhkat tarkasti ja täsmällisesti
Sadat tietoturvatiimit ympäri maailmaa luottavat AlphaSOC:iin havaitakseen haittaohjelmia, tietovuotoja ja luvatonta toimintaa tietoverkoissaan. Pilvipalvelumme ja paikallisten analytiikkatyökalujemme avulla voit vastaanottaa hyödyllisiä ja käytännöllisiä hälytyksiä, jotka auttavat reagoimaan tilanteisiin kulloinkin oikealla ja tehokkaimmalla tavalla.Analytiikkatyökalut
Splunk-sovelluksemme pisteyttävät verkkoliikennelokeja reaaliajassa uusien uhkien ja poikkeavuuksien tunnistamiseksi. Muut kuin Splunk-käyttäjät voivat käyttää rajapintaamme suoraan ja luoda mukautettuja integraatioita SDK:n kanssa.
Tietoja tuotteesta
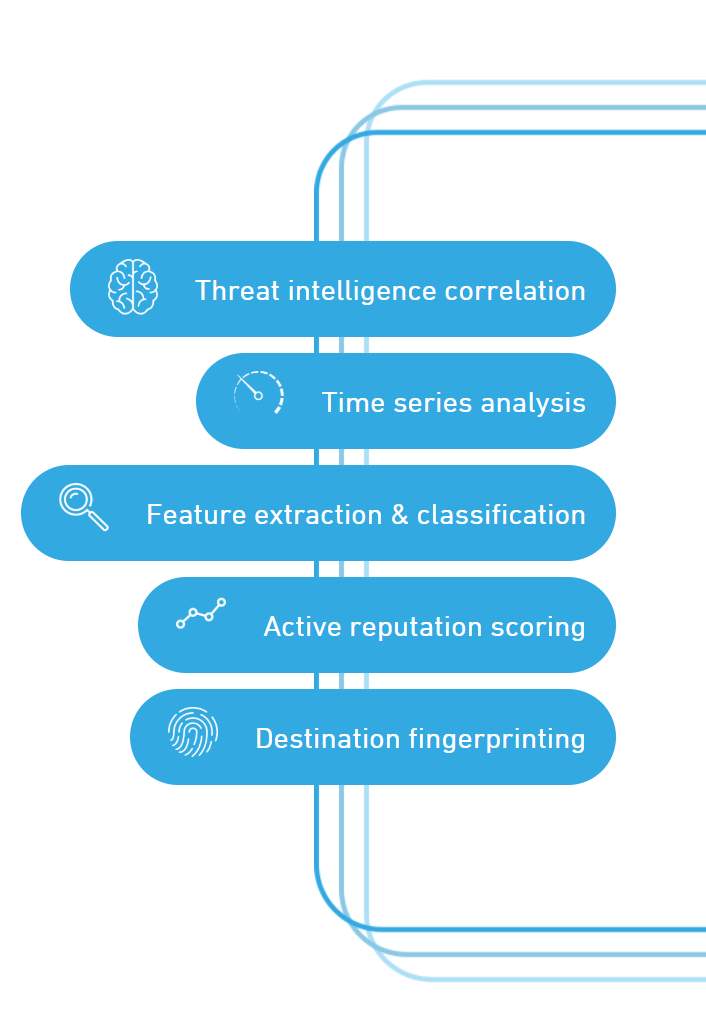 Alphasoc Analytics Engine (AE) tekee syvällistä tutkimusta lähdemateriaaliin, kuten:
Alphasoc Analytics Engine (AE) tekee syvällistä tutkimusta lähdemateriaaliin, kuten:
- Määrällinen ja laadullinen analyysi (tapahtumien laskenta, kaavojen tunnistus)
- FQDN:ien ja domainien tunnistus kontekstin keräämiseksi (sinkhole-tunnistus ja ASN-arvot)
- FQDN-tunnisteiden jakautuminen ja analyysi (ts. hostit, verkkotunnukset, TLD)
- Mainetietojen kerääminen (esim. whois-tiedot ja niihin liittyvät haittaohjelmanäytteet)
- Liikenteeen luokittelu perustuen tunnettuihin kaavoihin ja kuvioihin (esim. C2, P2P, VPN, cryptomining)
Nimenomaisia käyttötapauksia, jotka Network Behavior Analytics ratkaisee:
- C2-takaisinsoittojen ja tunnettuihin sinkholeihin liikennöinnin paljastaminen
- Tor, I2P ja Freenet -liikenteen tunnistaminen
- Cryptomining ja JavaScript-cryptojacking -havainnointi
- Tunnettuihin phishing-domaineihin menevän liikenteen merkitseminen
- Brändiväärennösten havainnointi Unicode-homoglyfien ja transpositioiden avulla
- DGA-domaineihin menevien useiden kutsujen merkintä, tartunnan indikointi
- DNS- ja ICMP-tunnelointien sekä vuotojen havainnointi
- Lateraalisen liikenteen sekä verkkoskannausten havainnointi
- Sääntörikkomusten merkitseminen (esim. kolmannen osapuolen VPN ja P2P)
Pidämme myös tietosi turvassa
Me AlphaSOC:lla suhtaudumme tietoturvallisuuteen erittäin vakavasti ja ymmärrämme, kuinka tärkeää tietojen suojaus on asiakkaillemme.
- Tietojen salaus (at-rest) AES256:aa käyttäen
- Tietojen salaus (in-transit) käyttäen TLS1.2+ ja AEAD-ciphereitä
- Vahva tunnistautuminen Yubico-avaimilla ja sisäisellä CA:lla
- Järjestelmäarkkitehtuuri ja lähdekoodi auditoidaan vuosittain kolmannen osapuolen toimesta
Telemetriatiedot, joita SOC-analyytikot käyttävät vaarantuneiden järjestelmien tunnistamiseen, tulevat päätepisteissä toimivista IDS-antureista, EDR:stä ja virustorjuntaohjelmista sekä SIEM-alustoista, jotka yhdistävät ja käsittelevät palomuurien ja muiden turvalaitteiden lokeja.
On olemassa kokonainen toimiala, joka palvelee asiakkaitaan uhkasyötteiden välityksellä tartunnan saaneiden järjestelmien tunnistamiseksi ja auttaa tietoturvatiimejä tunnistamaan haitalliset toimijat ja kampanjat tunnettujen jälkien (esimerkiksi IP-osoitteiden, verkkotunnusten ja hashien) avulla.
Indikaattorilistoja käytetään yleisesti yksiulotteisella tavalla:
- Raakadata korreloidaan syötteen kanssa ja generoidaan hälytys, kun yhteys löytyy
Monet pahantahtoiset tahot ovat tietoisia tästä kypsyystasosta yritysten SOCeissa. Tunnistuksen ohittamiseksi he yksinkertaisesti välttävät IP-osoitteiden, verkkotunnusten, suoritettavien tiedostojen ja muiden materiaalien uudelleenkäyttöä kampanjoidensa välillä. On olemassa lukuisia uhkia, joita ei voida tunnistaa pelkästään yhden ulottuvuuden korrelaatiolla.
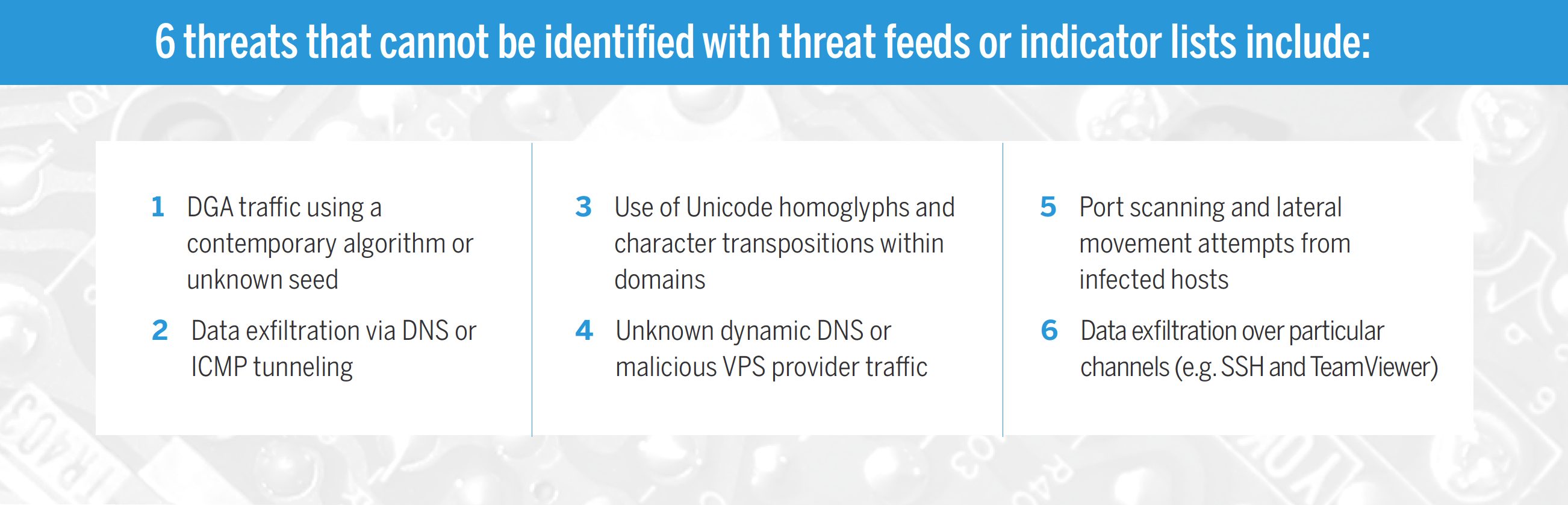
Esittelyssä Analytics Engine
Puolustautuakseen tuntemattomilta haittaohjelmakampanjoilta ja määrätietoisilta hyökkääjiltä tietoturvatiimit käyttävät aikaa tietoturva-analyysien tutkimiseen syventääkseen tietojaan. Vankan analyysipinkan rakentaminen ja tällaisen raskaan manuaalisen työn suorittaminen käsin on usein kustannuksiltaan kohtuutonta, joten sadat tiimit ovat ottaneet käyttöönsä AlphaSOC Analytics Engine:n (AE) selvittämään poikkeavuuksia suurissa ympäristöissä.
AlphaSOC AE suorittaa nopeita moniulotteisia analyyseja raaoista DNS-, IP- ja HTTP-verkkotapahtumista paikan päällä tai pilvessä tapahtuvan analytiikan kautta. Yksilöityjä luokittelijoita ja ominaisuuksia, jotka olemme rakentaneet ja joita olemme parantaneet, ovat:
- Volumetrinen ja kvantitatiivinen analyysi (kuvioiden ja huippujen tunnistaminen)
- FQDN-verkkotunnusten ja verkkotunnusten kontekstiselvitys (esim. sinkhole-liikenteen) keräämiseksi
- Kunkin FQDN-tunnisteen jakautuminen ja analysointi (ts. hostname, verkkotunnus, TLD)
- Maine tietojen kerääminen (esim. WHOIS ja sandbox-tulokset)
- Liikenteen luokittelu tunnettuihin malleihin (esim. C2, P2P, VPN)
- Tilatietojen ja liikennemallien seuranta (paljastaen sivuttaisliikehdinnän)
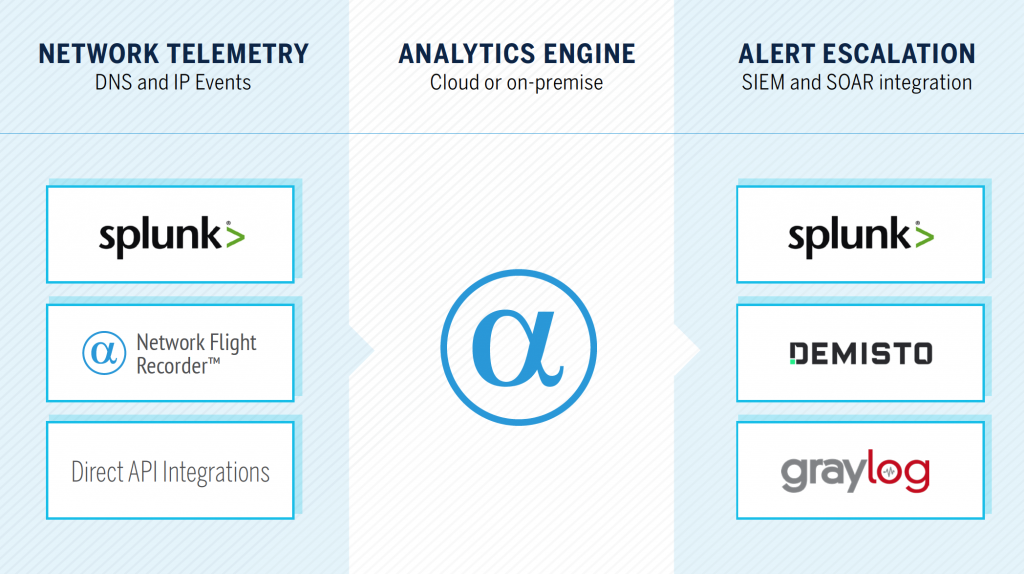
Tietojen syöttö
DNS, IP ja HTTP -tapahtumat voidaan kerätä ja lähettää Analytics Enginelle näillä tavoilla:
- Network Behavior Analytics for Splunk (natiivi integraatio)
- Network Flight Recorder (NFR — meidän kevyt, open source -agentti)
- Suora API-integraatio pilvipalveluamme tai paikallista ratkaisuamme käyttäen
- Telemetriatietojen tallennus Amazon S3:een (esim. Cisco Umbrella, CrowdStrike, VPC flow logs jne.)
- Elastic Packetbeat ja Logstash
Hälytysten eskalointi
Käsittelyn aikana AlphaSOC AE generoi hälytyksiä, jotka kuvaavat poikkeavuuksia (esim. kutsuja tuoreeseen domainiin tai ICMP-liikenteen huippu, joka indikoi tunnelointia) ja tunnettuja uhkia (esim. C2-takaisinsoittoja tai Tor-piirin asennusta). NFR hakee hälytykset JSON-muodossa ja lähettää ne Syslogin kautta mille tahansa SIEM- tai SOAR-alustalle.
Natiivi Splunk-integraatiomme tarjoaa useita dashboardeja tukemaan threat huntingia ja poikkeavuuksien tutkimista. Sääntörikkomukset (esim. P2P-aktiviteetti, kolmannen osapuolen VPN:n käyttö ja mahdolliset ei-toivotut ohjelmat) voidaan nopeasti viedä tiketöintiin (esim. ServiceNow), vapauttamalla SOC-analyytikot keskittymään vaarantuneiden laitteiden löytämiseen ja tilanteen korjaamiseen.
Käyttötapaukset
Moniulotteinen analysointi ratkaisee monia vaativia käyttötapauksia ja käsittelee sokeita pisteitä, joita tietoturvatiimit kohtaavat. Pystymme välittömästi ilmoittamaan seuraavista uhkista Analytics Enginen kautta:
- DNS- ja ICMP-tunnelointi ja tietojen vuotaminen
- Tietojenkalasteluhyökkäykset käyttävät uusia brändi-permutaatioita ja -homoglyfejä
- C2-takaisinsoitot, IRC-liikenne ja anonymizerit (esim. Tor, I2P, Freenet)
- Infektiota indikoivat sivuttaisliikehdinnät ja epäilyttävä lähtevä liikenne
- Cryptomining ja cryptojacking-hyökkäykset
- Liikenne tuntemattomiin/uusiin dynaamisiin DNS-palveluntarjoajien verkkotunnuksiin
- Sääntörikkomukset (esim. ei-toivotut ohjelmat, kolmannen osapuolen VPN:t ja P2P)
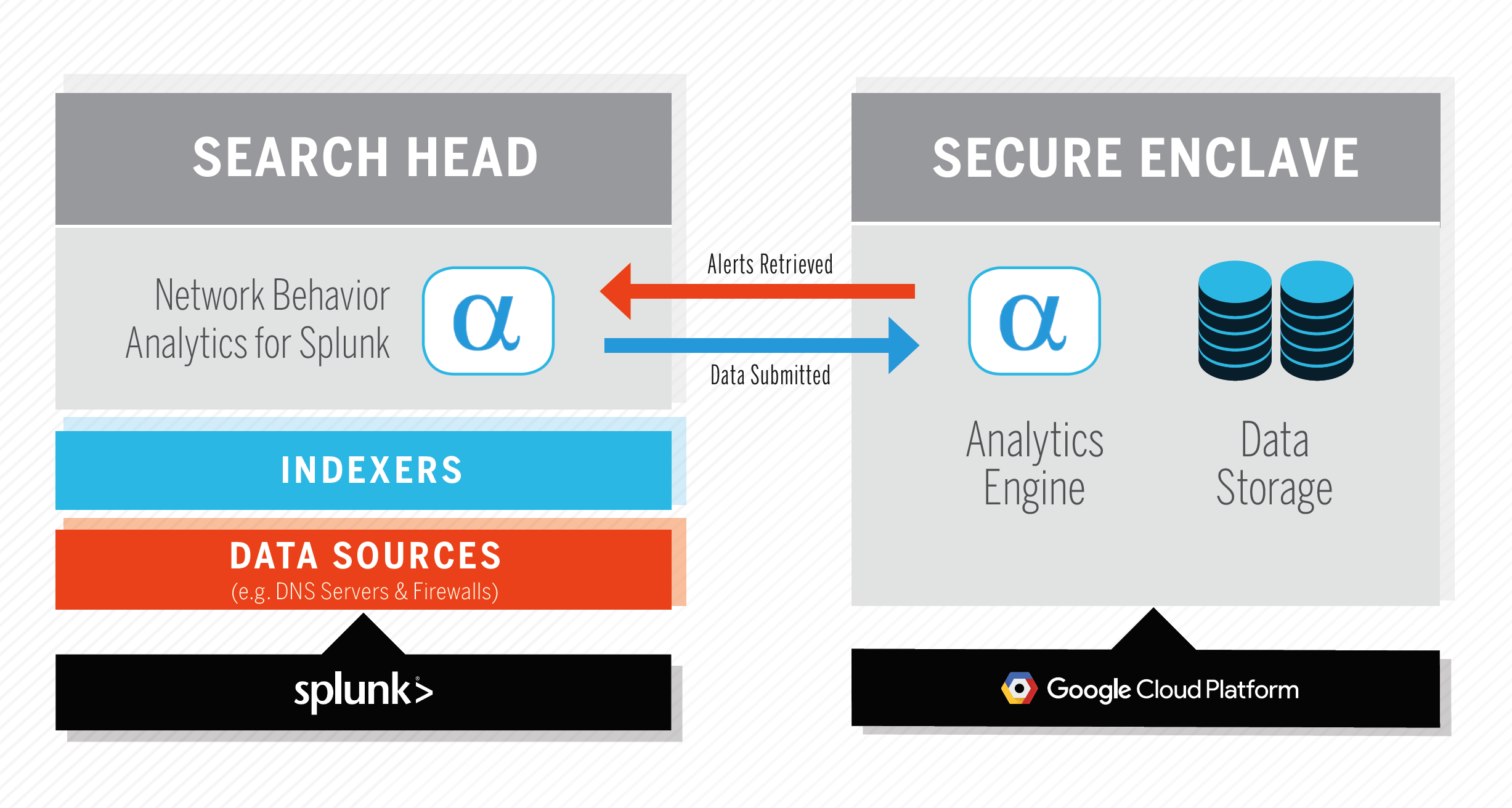
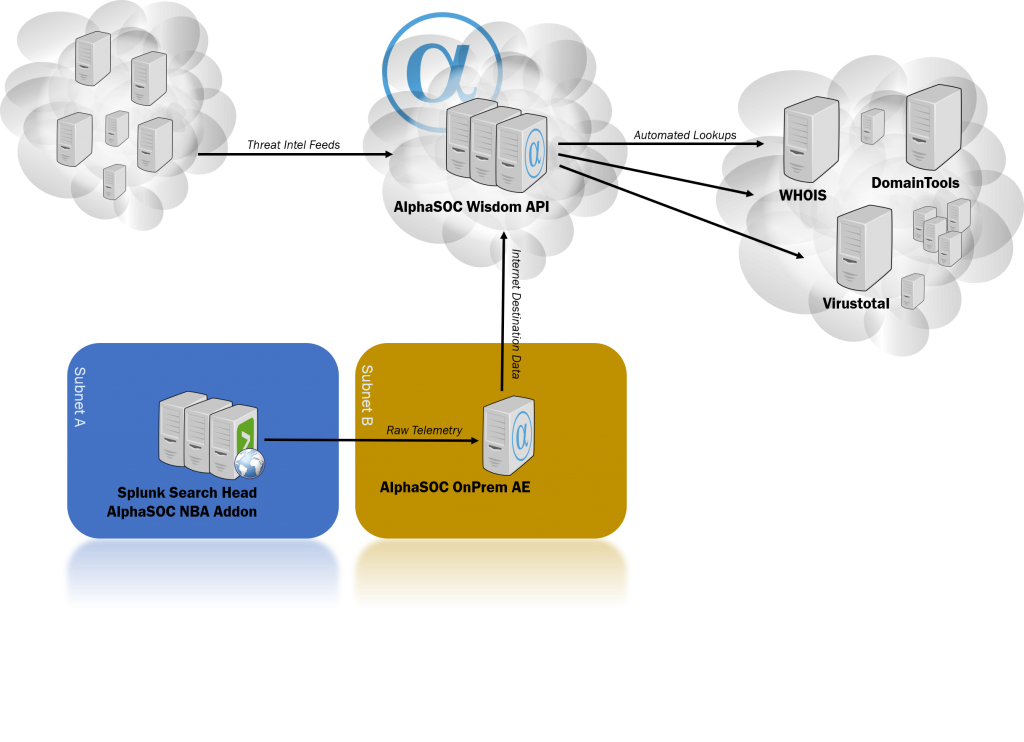
Network Behavior Analytics for Splunk paljastaa nopeasti tartunnan saaneet koneet ja uhkat ympäristöllesi. Splunk-sovellus käsittelee ja lähettää verkon telemetriatietoja (CIM-kompliantit DNS-, IP- ja HTTP-tapahtumat) AlphaSOC Analytics Engine -sovellukselle pisteyttämistä varten ja luo tietoturvahälytyksiä ja -tietoja lisätutkimuksia varten. Järjestelmäarkkitehtuuri on esitetty alla.
Haluatko testata?
Lataa sovellus Splunkbasesta. Aktivoitu AlphaSOC API -avain tarjoaa 30 päivän rajoittamattoman pääsyn hälytyksiin, kun testaat tuotettamme. Pyydä meiltä tarvittaessa apua tai pidempää kokeiluversiota.
Mitä tietoja tarvitsen?
Mitä enemmän tietoja sinulla on, sen parempia ovat myös tulokset. Voimme hyödyntää seuraavia:
- Palomuurilokit
- Netflow-tiedot
- DNS-lokit
- HTTP-välityspalvelimen lähtevät lokit
Jotta AlphaSOC toimii, tarvitset vähintään yhden mainituista tietolähteistä. AlphaSOC hyödyntää CIM-mallia, joten oikein tägättyjä lokeja voidaan hyödyntää automaattisesti.
Kuinka asennus ja konfigurointi tapahtuu?
Lisää ohjeita löydät aina ajan tasalla olevista manuaaleistamme: https://www.alphasoc.com/docs/nba-introduction
Entä minun tietoni, ovatko ne turvassa?
Teemme käsittelymme pilvessä. Mutta älä pelkää, voit tarvittaessa ottaa käyttöön paikallisesti asennetun Analytics Enginen.
Asiantuntijapalvelumme
Mint Security toimittaa sinulle tukea ja seuraavia asiantuntijapalveluita:
- Lokilähteiden liittäminen AlphaSOC:n käyttämisen mahdollistamiseksi
- Räätälöityjen hälytysten ja integraatioiden tuottaminen – JIRA, Alert Manager, Slack jne.
- Paikallisen Analytics Enginen asennus
- Tulosten analysointi ja uhkien arviointi
- Monipuolinen etulinjan tuki suomeksi, englanniksi ja ruotsiksi – valitsemallasi aikavyöhykkeellä
Myynti ja lisensointi
Myymme lisenssejä, euroissa.
AlphaSOC:n asiakkaat lähettävät telemetriatietoja verkon lähteistä kuten palomuurit, välityspalvelimet, DNS-palvelimet ja IDS-järjestelmät.
Analytics Engine (AE) suorittaa moniulotteista verkon telemetriadatan prosessointia, korostaa poikkeuksia ja tuo ne sinun tietoosi.
Tietoturvatiimit käyttävät SIEM- ja SOAR-integraatioitamme eskaloidakseen tarkkoja ja käytännöllisiä hälytystietoja eteenpäin oikeille tahoille.
Reagoi tai hyväksy riski tietoisesti.
Valinta on sinun.
Liittyvät blogit

AlphaSOC Network Flight Simulator paljastaa havainnoinnin sokeat pisteet
AlphaSOC on juuri julkaissut Network Flight Simulator (flightsim) 2.2.1:n, joka on ilmainen avoimen lähdekoodin hyökkäyssimulaatiotyökalu. Tämä uusin julkaisu sisältää joukon uusia moduuleja, joiden avulla tietoturvatiimit voivat välittömästi arvioida Detection & Response -kattavuuden SIEM- ja SOAR-työkaluissa.
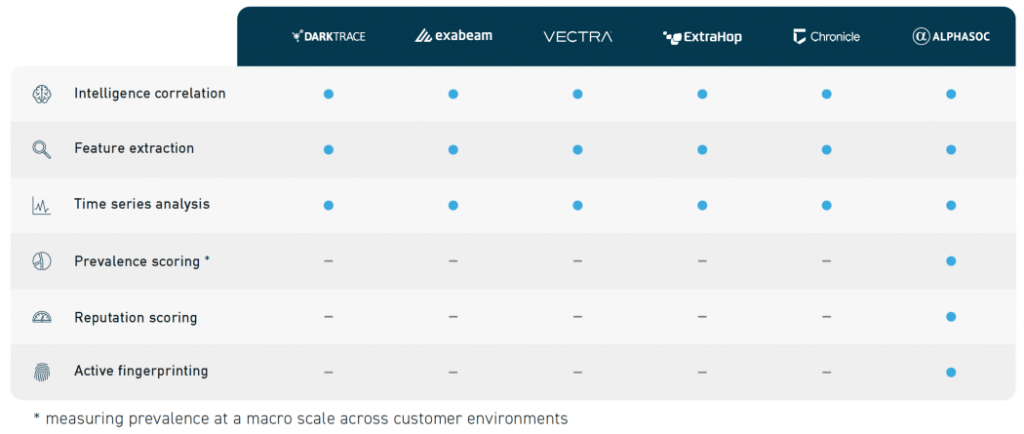
Indikaattorilistojen tuolla puolen
AlphaSOC käsittelee tietoverkkojen telemetriatietoja ja paljastaa sekä tunnettuja että tuntemattomia, uusia uhkia. Monitasoisen analyysimenetelmän avulla tietoturva-asiantuntijat voivat löytää jopa kolme kertaa enemmän haittaohjelmia kuin pelkästään IOC-indikaattoreita käyttämällä.
Mitä AlphaSOC tekee
AlphaSOC on kevyt mutta äärimmäisen tehokas työkalu egress-liikenteen tarkkailuun. AlphaSOCin Analytics Engine ratkaisee monta käyttötapausta, joiden toteuttaminen muulla tavoin olisi erittäin työlästä ja haastavaa.
AlphaSOCin asennusvaihtoehtoja
”Pilvi!” joku huutaa kovaan ääneen. ”Sehän tarkoittaa, että minun tietoni lähetetään pilveen. Minun kullankalliit telemetriatietoni pahantahtoisten muukalaisten käsissä paljastaen minusta aivan liikaa!” Pitää paikkansa. Läpinäkyvyyden nimissä, tarkastellaanpa siis hieman, mitä kulissien takana oikeasti tapahtuu.
Mint Security jälleenmyymään AlphaSOCin ratkaisuja
Mint Security ryhtyy jälleenmyymään ja tukemaan AlphaSOCin tuotteita ja ratkaisuja suomessa ja euroopassa.
Automatisoi uhkien metsästys
Through Network Behavior Analytics for Splunk and our native integrations for Demisto and Graylog, we instantly enrich network indicators (FQDNs, URLs, and IP addresses) to provide security teams with hunting material.
