Through Network Behavior Analytics for Splunk and our native integrations for Demisto and Graylog, we instantly enrich network indicators (FQDNs, URLs, and IP addresses) to provide security teams with hunting material.
In this post, I describe some of the key classifiers within the AlphaSOC Analytics Engine, the public API we operate, and how teams consume our context data to uncover emerging threats that don’t have signatures.
Imposter Detection
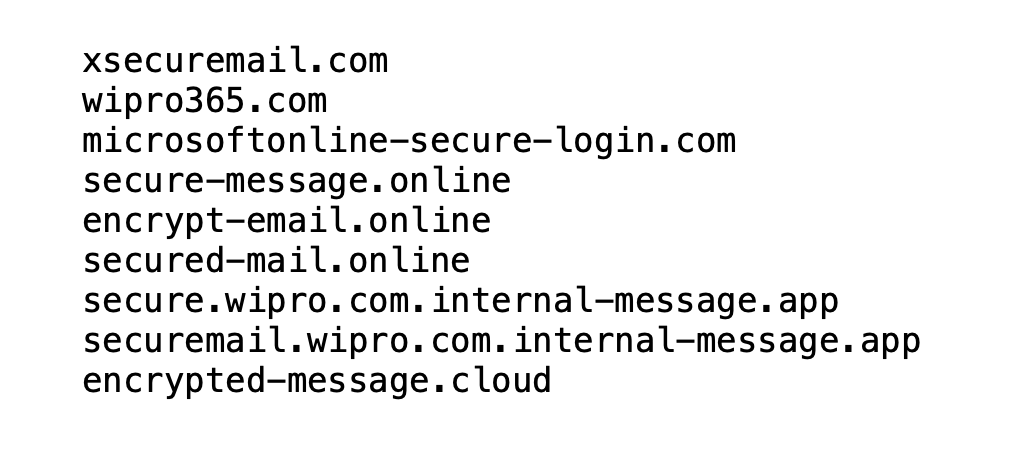

To drop any non-starters (e.g. user typos) the engine verifies that:
- The domain exists via DNS / WHOIS lookup
- The domain isn’t owned by the respective company (e.g. Dropbox)
- The infrastructure isn’t operated by a phishing simulation provider
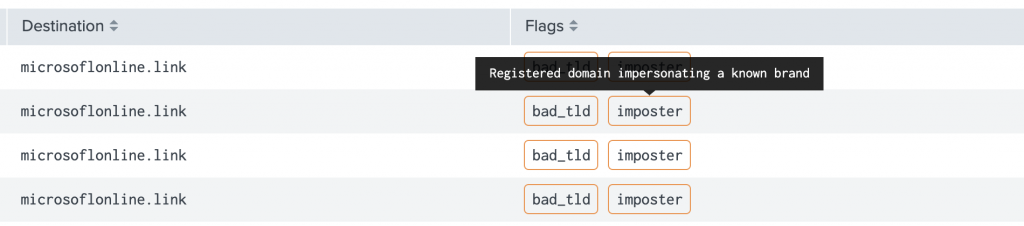
Highlighting Unique and Young Domains
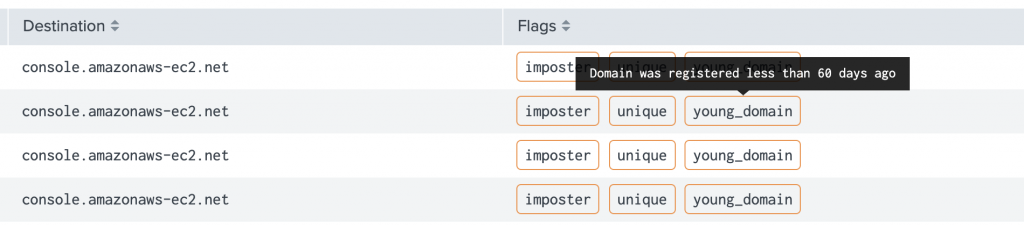
Active Scoring and Fingerprinting
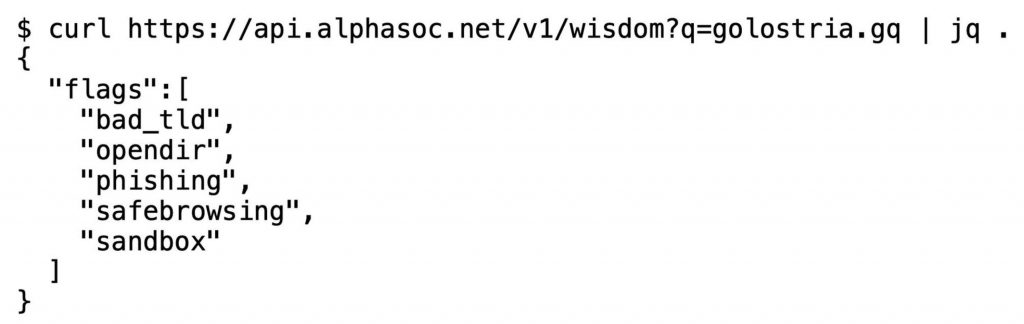
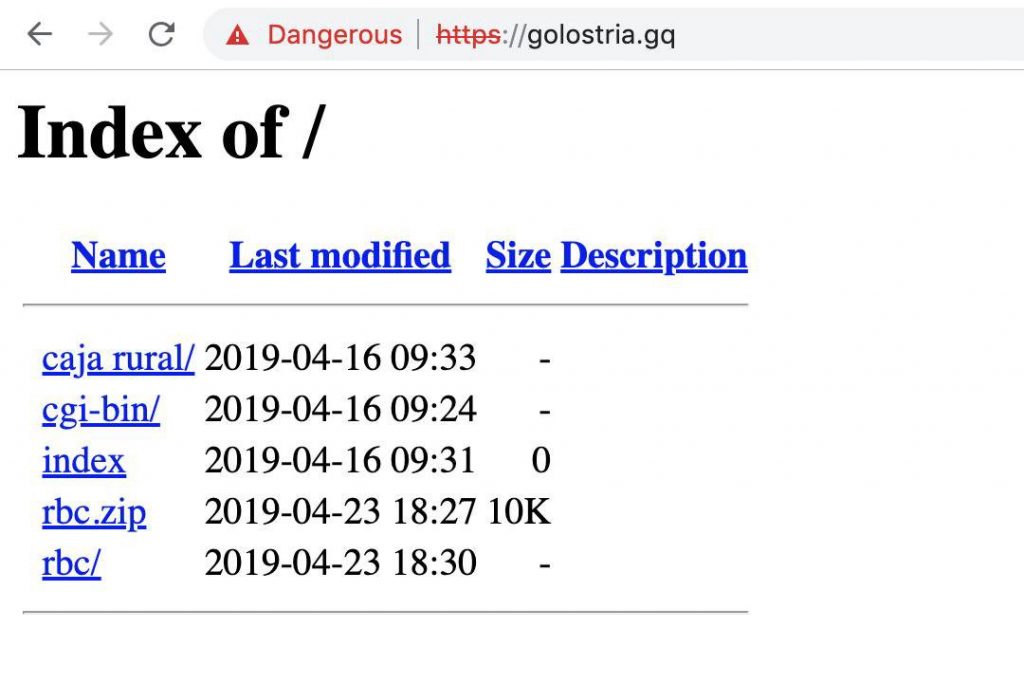
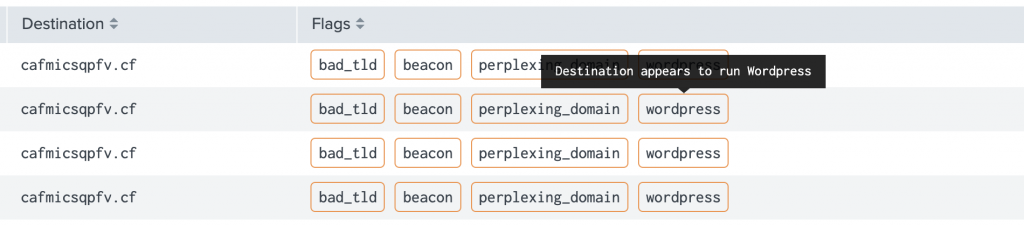
Uncovering Emerging Threats in Practice
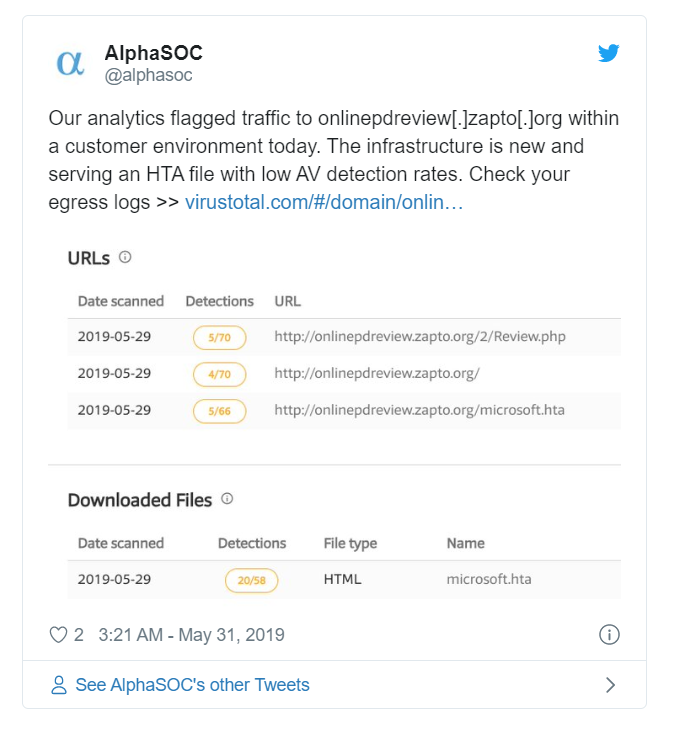
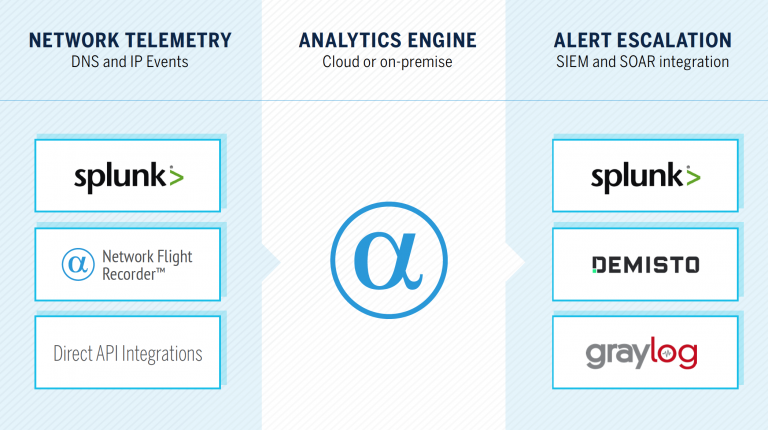
AlphaSOC
Löydä saastuneet työasemat Havaitse vuodot ja muu luvaton käyttö Vastaanota korkealaatuisia uhkahälytyksiä Löydä tietoturvauhkat tarkasti ja täsmällisesti Sadat tietoturvatiimit ympäri maailmaa luottavat AlphaSOC:iin havaitakseen haittaohjelmia,

AlphaSOC Network Flight Simulator paljastaa havainnoinnin sokeat pisteet
AlphaSOC on juuri julkaissut Network Flight Simulator (flightsim) 2.2.1:n, joka on ilmainen avoimen lähdekoodin hyökkäyssimulaatiotyökalu. Tämä uusin julkaisu sisältää joukon uusia moduuleja, joiden avulla tietoturvatiimit voivat välittömästi arvioida Detection & Response -kattavuuden SIEM- ja SOAR-työkaluissa.






