
- SAST - Koodin staattinen tarkistus
- SCA - Kirjastoanalyysi ja inventaario
- SDLC sovelluskehitysintegraatio
Yrityksen koko sovellusportfolion tietoturvariskien hallinta samassa palvelussa

Veracoden palvelun avulla voidaan tutkia ja parantaa sovellusten tietoturvaa kehitysprosessin alusta aina tuotantokäyttöön asti. Palvelu sopii kaikenlaisiin sovelluskehitysprosesseihin – manuaalisista täysin automatisoituihin. Veracoden palvelu opettaa tekemään tietoturvallista koodia ja näin auttaa kehitystiimejä kehittämään korkealaatuisia sovelluksia. Johdolle Veracode tuo läpinäkyvyyttä ja mitattavuutta – myös ulkoistetun sovelluskehityksen osalta.
Veracode tarjoaa kattavan näkymän sovellusten tietoturvan tilaan kaikille testausmenetelmillä kuten SAST, DAST ja SCA.
Mint Security täydentää ja laajentaa Veracoden palveluja
Mint Security yhdistää, koordinoi ja innovoi turvallisen ohjelmistokehityksen elinkaarta. Lisäämällä Veracode-työkaluja palveluumme toimitamme kokonaisvaltaisen ja tyylikkään ratkaisun sekä kehitystiimille, business ownereille että johdolle.
Tarjoamme ketteriä demoja ratkaisujen ympärillä, jopa omalla koodillasi – myös Teamsin kautta. Tarkistamme koodisi ilman kustannuksia ja samalla näytämme todellisia tuloksia, joihin on helppo yhtyä. Kun olemme osoittaneet onnistuneesti todellisen hyödyn, toteutamme PoCin, jotta näette miten ratkaisu toimii käytännössä. PoCissa tiimisi pääsee itse käyttämään Veracodea – voimme jopa tehdä integraatioita PoCin aikana.
skannattua koodiriviä
haavoittuvuutta korjattu
Gartnerin AST MQ
asiakasta
Asiantuntijoilta asiantuntijoille

Veracoden perustivat aikanaan johtavien sovellusten turva-alan yritysten asiantuntijat, joiden tavoitteena on auttaa organisaatioita suojaamaan koodinsa tietoturvauhkia vastaan kustannustehokkaasti. Veracode tarjoaa staattista analyysiä palveluna pilvestä, joten yritysten ei tarvitse investoida pääomaa itse alustaan. Koska Veracoden alusta on automatisoitu ja helppokäyttöinen, yritysten ei välttämättä tarvitse palkata turvallisuusarvioinnin asiantuntijoita tai konsultteja avuksi. Veracoden staattinen analyysi arvioi käännettyjä sovelluksia lähdekoodin sijaan. Näin voidaan testata valmiita sovelluksia kirjastoineen ja tarjota kattavan ja laajan sovellusturvallisuuden.
Tehokkaan automaation, prosessin ja nopean alustan ansiosta Veracode yhdistää saumattomasti sovellusten turvallisuuden koko ohjelmiston elinkaareen, jolloin poistetaan kustannustehokkaasti haavoittuvuudet kehitys- / käyttöönottoketjusta ja estetään uhat tuotannon aikana. Tätä kokonaisratkaisua hallitaan yhdellä keskitetyllä alustalla, ja se perustuu tehokkaaseen yhdistelmään huippuluokan teknologiaa ja turvallisuusasiantuntijoita, jotka tarjoavat korjausvalmennusta ja prosessien ohjausta.
Kehittäjille ja dev-osastolle
Veracode tekee turvallisen koodin kirjoittamisesta mahtavaa ja helppoa. Kehittäjät pääsevät suoraan kiinni ongelmiin – kehittyneillä välineillämme, kuten API- ja IDE-integraatioilla, saa vinkit haavoittuvuuksien korjaamiseen suoraan niiden löytämisen yhteydessä. Voit tehdä turvallisuudesta saumattoman osan kehitystyön elinkaarta ilman luopumista kehitystyön nopeudesta tai innovaatioista. Ketterää tietoturvaa, ihan oikeasti.
Tietoturva-ammattilaisille
Veracoden avulla voidaan täyttää sekä kehittäjien tarpeet sovellusten turvallisudelle että yrityksen asettamat raportointi- ja varmennusvaatimukset. Veracoden kyky tarjota oikeat ratkaisu jokaiselle ohjelmiston elinkaaren vaiheelle varmistaa, että yritysten rakentamat ja hankkimat sovellukset sekä kolmansien osapuolten komponentit ovat turvallisia.
Johdolle
Veracode toimittaa sovellusten tietoturvaratkaisuja ja palveluita, joita nykyinen ohjelmistopohjainen maailma edellyttää, jotta innovaatio ja turvallisuus voivat kulkea käsi kädessä. Veracoden asiakkaat aloittavat työstämisen nopeasti, huomaavat arvon jo ensimmäisenä päivänä, osoittavat noudattavansa regulaatioita ja skaalautuvat helposti. Veracodella saat myös lisää mitattavuutta ulkoistetun sovelluskehityksen SLA- tai laatuvaatimuksiin.
Tuotannolla ja ops-osastolle
Veracode tarjoaa ratkaisuja, jotka varmistavat sovelluksen turvallisuuden aina tuotantovaiheeseen saakka. Tuotannosta vastaavat tiimit saavat paremman käsityksen tuotantosovelluksiin mahdollisesti kohdistuvista hyökkäyksistä ja voivat suojautua uhkia vastaan ilman heikennyksiä suorituskykyyn. Kun mahdollisesti käytössä olevissa avoimen lähdekoodin komponenteissa havaitaan uusia haavoittuvuuksia, riskikohteet voidaan löytää ja korjata nopeasti.
Mitä on staattinen analyysi – SAST
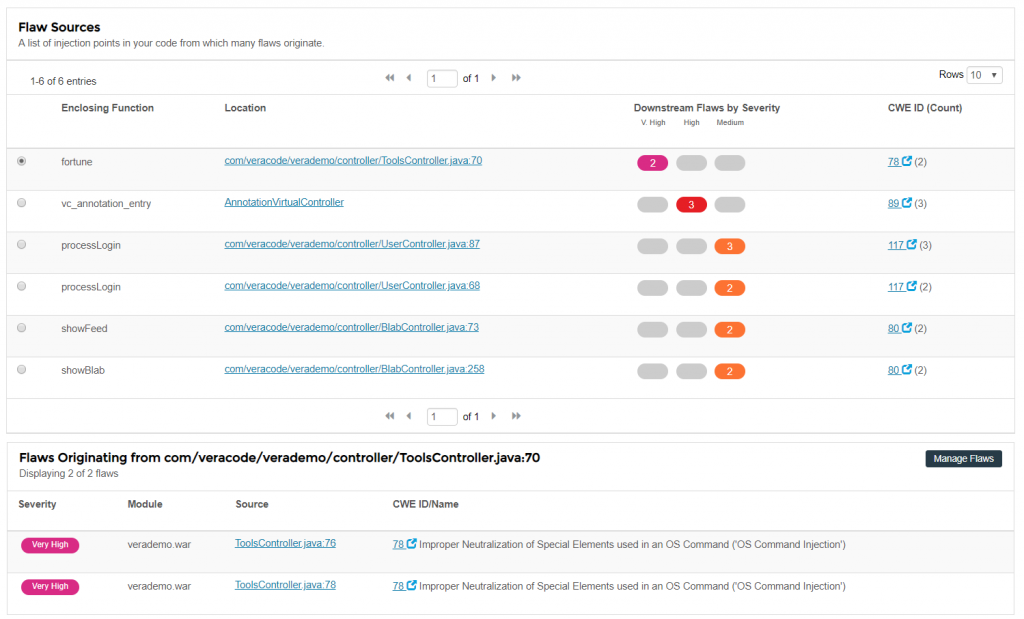 SAST, eli Static Analysis Security Testing ja suomeksi koodin staattinen analyysi on yksi monista koodin tarkistustyökaluista, joita voidaan tehdä ilman ohjelmiston varsinaista suorittamista. Staattisessa analyysissä tarkastellaan ohjelmaa ei-ajoympäristössä. Tämä testausmenetelmän selkeänä etuna on, että siinä voidaan arvioida kaikenlaisia sovelluksia, sekä verkkopalveluja että muita sovelluksia, Kehittyneen mallinnuksen avulla voidaan havaita ohjelmiston syötteiden ja tulosten virheitä, joita ei voi välttämättä nähdä dynaamisen, eli esim. tuotantoympäristön skannauksen kautta. Aiemmin tämä tekniikka vaati lähdekoodia, mikä on epäkäytännöllistä, koska lähdekoodi ei usein ole käytettävissä. Lisäksi lähdekoodin tarkastelu on usein myös riittämätöntä. Veracoden staattisen analyysin palvelu arvioi binäärikoodia tai tavukoodia (käännetty ohjelma) lähdekoodin sijaan, minkä avulla yritykset voivat testata ohjelmistojaan tehokkaammin ja kattavammin. Tämä tietenkin lisää ohjelmiston tai tuotteen kokonaisturvallisuutta.
SAST, eli Static Analysis Security Testing ja suomeksi koodin staattinen analyysi on yksi monista koodin tarkistustyökaluista, joita voidaan tehdä ilman ohjelmiston varsinaista suorittamista. Staattisessa analyysissä tarkastellaan ohjelmaa ei-ajoympäristössä. Tämä testausmenetelmän selkeänä etuna on, että siinä voidaan arvioida kaikenlaisia sovelluksia, sekä verkkopalveluja että muita sovelluksia, Kehittyneen mallinnuksen avulla voidaan havaita ohjelmiston syötteiden ja tulosten virheitä, joita ei voi välttämättä nähdä dynaamisen, eli esim. tuotantoympäristön skannauksen kautta. Aiemmin tämä tekniikka vaati lähdekoodia, mikä on epäkäytännöllistä, koska lähdekoodi ei usein ole käytettävissä. Lisäksi lähdekoodin tarkastelu on usein myös riittämätöntä. Veracoden staattisen analyysin palvelu arvioi binäärikoodia tai tavukoodia (käännetty ohjelma) lähdekoodin sijaan, minkä avulla yritykset voivat testata ohjelmistojaan tehokkaammin ja kattavammin. Tämä tietenkin lisää ohjelmiston tai tuotteen kokonaisturvallisuutta.
Lisää yksityiskohtia
Patentoitu teknologia
 Veracoden patentoitu staattinen, binäärisovelluksen tietoturvatestauksen (SAST) tekniikka, analysoi kaiken koodin, mukaan lukien kolmansien osapuolten komponentit ja ohjelmakirjastot. SAST täydentää kehittäjien tekemiä uhkamallinnuksia ja koodinarviointeja löytäen mahdolliset koodausvirheet ja puutteet nopeammin ja edullisemmin automatisoinnin kautta. Teknologiaa käytetään tyypillisesti ohjelmistokehityksen elinkaaren alkuvaiheessa, koska ongelmien korjaaminen on helpompaa ja halvempaa ennen tuotantokäyttöä. SecDevOps hengessä, Veracode on kokonaisuus, joka alkaa ensimmäisistä koodiriveistä aina CI-ympäristöön ja automatisointiin asti.
Veracoden patentoitu staattinen, binäärisovelluksen tietoturvatestauksen (SAST) tekniikka, analysoi kaiken koodin, mukaan lukien kolmansien osapuolten komponentit ja ohjelmakirjastot. SAST täydentää kehittäjien tekemiä uhkamallinnuksia ja koodinarviointeja löytäen mahdolliset koodausvirheet ja puutteet nopeammin ja edullisemmin automatisoinnin kautta. Teknologiaa käytetään tyypillisesti ohjelmistokehityksen elinkaaren alkuvaiheessa, koska ongelmien korjaaminen on helpompaa ja halvempaa ennen tuotantokäyttöä. SecDevOps hengessä, Veracode on kokonaisuus, joka alkaa ensimmäisistä koodiriveistä aina CI-ympäristöön ja automatisointiin asti.
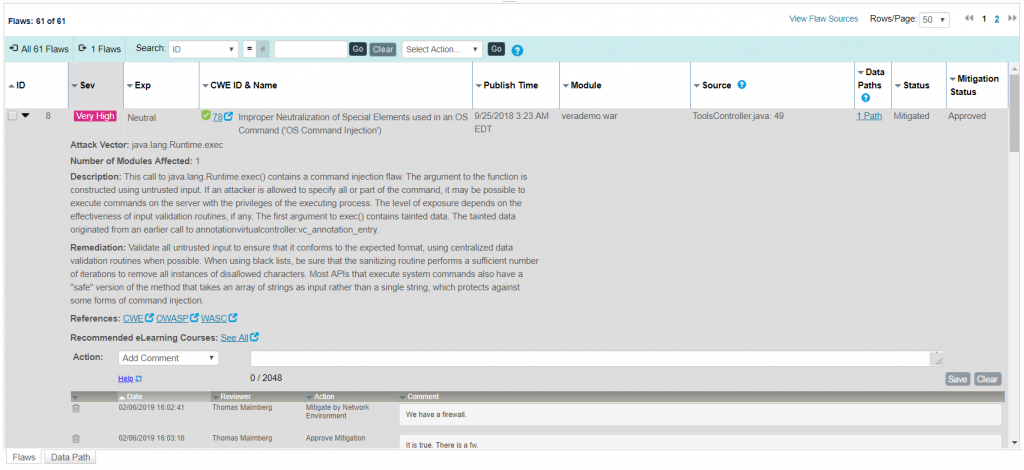
Haavoittuvuuksien metsästystä
Veracoden SAST-teknologia tunnistaa kriittiset haavoittuvuudet, kuten esim. SQL-injektiot, sivustojen väliset komentosarjat (XSS), puskurin ylivuodot, käsittelemättömät virhetilat, kovakoodatut salasanan ja mahdolliset takaovet. Se luokittelee ja priorisoi haavoittuvuudet käyttäen NIST-vakavuusasteiden mukaista standardia. Kehittäjien avuksi toimitetaan yksityiskohtaiset tiedot ja korjausehdotukset, joiden perusteella he pystyvät aloittamaan nopeasti tarvittavat toimenpiteet. Ehdotuksia tukemassa on linkit CWE-tietokantoihin, seikkaperäiset kuvaukset haavoittuvuudesta, arvio korjauksen monimutkaisuudesta sekä linkitys Veracoden eLearning-portaaliin. Jos tämäkään ei riitä, voi painaa nappia ja kutsua paikalle sovellustietoturva-asiantuntijan, joka katsoo yhdessä kehittäjän kanssa juuri sitä ongelmallista tilannetta, jota ollaan ratkomassa.
Miten SAST toimii
SAST analysoi binäärikoodin luodakseen yksityiskohtaisen mallin sovelluksen data- ja ohjauspoluista. Tämän jälkeen mallia käytetään sovelluksen läpi kaikista poluista, jotka edustavat mahdollisia heikkouksia. Jos esimerkiksi sovelluksen tieto on peräisin HTTP-pyynnöstä ja etenee sovelluksen läpi ilman validointia tai puhdistusta tietokantakyselyyn saakka, tämä edustaisi SQL-injektiota. Jokainen tällainen teoreettinen polku sovelluksen sisällä analysoidaan tarkasti.
Binääripohjainen SAST antaa syvemmän näkymän
Binääripohjaisen SAST-tekniikan avulla haavoittuvuusien etsintä ja korjaaminen on entistä nopeampaa ja tarjoaa yksityiskohtaisia tietoja. Se on tarkka: staattinen analyysi tutkii sovellukset samalla tavalla kuin hyökkääjät katsovat niitä luomalla yksityiskohtaisen mallin sovelluksen tieto- ja ohjausvirroista. Toisin kuin perinteiset lähdekoodia tarkastavat ohjelmat, tämä lähestymistapa havaitsee tarkasti piilotetut uhat, kuten takaportit, joita on vaikea havaita, koska ne eivät välttämättä ole näkyvissä lähdekoodissa.
Vielä syvemmälle
Työkalu on hyvin käytännönläheinen: priorisoidut tulokset voidaan viedä tiketöintijärjestelmään, kuten esim JIRA, tai niitä voidaan tarkastella selainkäyttöliittymän kautta – tai suoraan sovelluskehittimestä. Vikojen yksityiskohdat ja korjausneuvot annetaan automaattisesti nopean korjaamisen tai ongelman kiertämisen tueksi. SAST minimoi vääriä positiivisia tuloksia. False positiviit ovat hyvin harvinaisia. Tämä lisää tuottavuutta väärien positiivisten tunnistamiseen käytettävän ajan vuoksi. Huippuluokan tietoturva-asiantuntijat tukevat Veracoden keskitettyä alustaa ja analysoivat käsin esim. mainitut false positive -tulokset. Siksi alusta oppii ja paranee jatkuvasti jokaisesta uudesta sovelluksesta, jonka se tarkistaa. Käyttäjälle se tarkoittaa, että voi aloittaa korjaustoimenpiteet nopeammin.
Mikä on SCA?
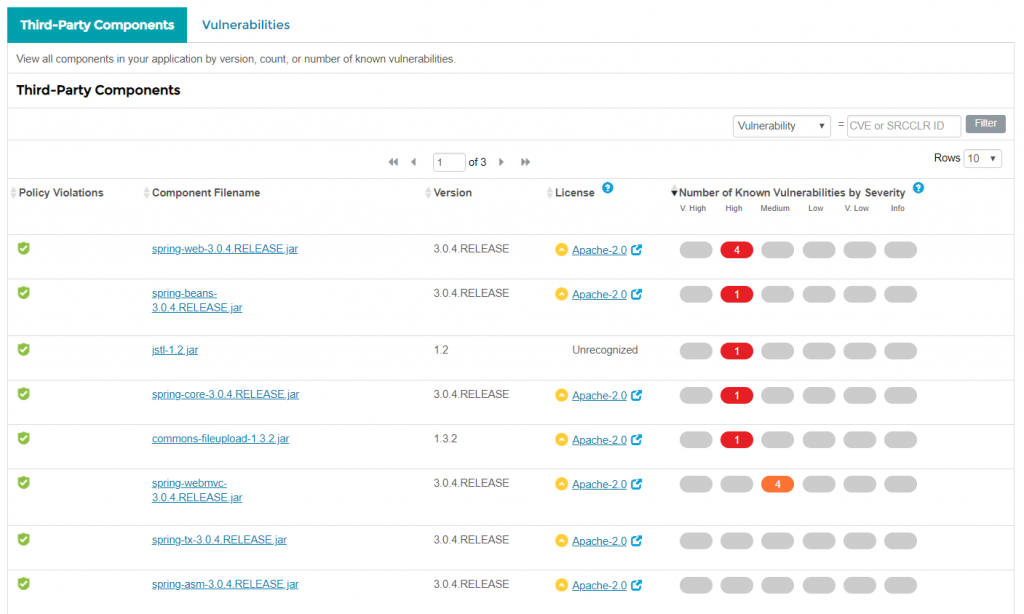 Veracode SCA (Software Composition Analysis/sovelluskirjastojen skannaus) suojaa Java-, Javascript- ja .NET-sovelluksia avoimen lähdekoodin riskiltä tunnistamalla sovellusten käyttämien avoimen lähdekoodin kirjastojen tunnetut haavoittuvuudet. Sen lisäksi, että Veracode SCA tekee haavoittuvuuksista listan skannauksen yhteydessä, se myös hälyttää, kun uusia haavoittuvuuksia havaitaan tai tunnettujen haavoittuvuuksien riskitasoja päivitetään. Veracoden alustan yhtenä toimintona SCA tarjoaa näkymän, jossa esitetään kaikki testausten tulokset yhdessä paikassa. Lisäksi samalla alustalla voidaan tehdä käyttäjien sekä testauskäytäntöjen, lievennysten ja integraatioiden hallinta.
Veracode SCA (Software Composition Analysis/sovelluskirjastojen skannaus) suojaa Java-, Javascript- ja .NET-sovelluksia avoimen lähdekoodin riskiltä tunnistamalla sovellusten käyttämien avoimen lähdekoodin kirjastojen tunnetut haavoittuvuudet. Sen lisäksi, että Veracode SCA tekee haavoittuvuuksista listan skannauksen yhteydessä, se myös hälyttää, kun uusia haavoittuvuuksia havaitaan tai tunnettujen haavoittuvuuksien riskitasoja päivitetään. Veracoden alustan yhtenä toimintona SCA tarjoaa näkymän, jossa esitetään kaikki testausten tulokset yhdessä paikassa. Lisäksi samalla alustalla voidaan tehdä käyttäjien sekä testauskäytäntöjen, lievennysten ja integraatioiden hallinta.
SCA
SCAn keskeisiä etuja:
- SCA käyttää tietokantaa, jossa on 3 miljoonaan koneoppimisen avulla kerättyä haavoittuvuutta. Tämä tarkoittaa, että testi löytää ongelmat ennen kuin niille on ehditty antaa CWE-numerot, Tiedätte aina ensimmäisenä uusista ongelmista,
- SCA:lla voi tehdä riippuvuusanalyysin, joka näyttää haavoittuvuudet ohjelmiston käyttämissä komponenteissa sekä näiden komponenttien riippuvuuksissa.
- Korjaukseen käytettävää aikaa nopeuttaakseen SCA näyttää vain ne komponenttikirjastojen haavoittuvuudet, joita sovelluksessa hyödynnetään. Se ei luettele kaikkea, mitä kirjasto sisältää.
Alhaisempi lisenssiriski
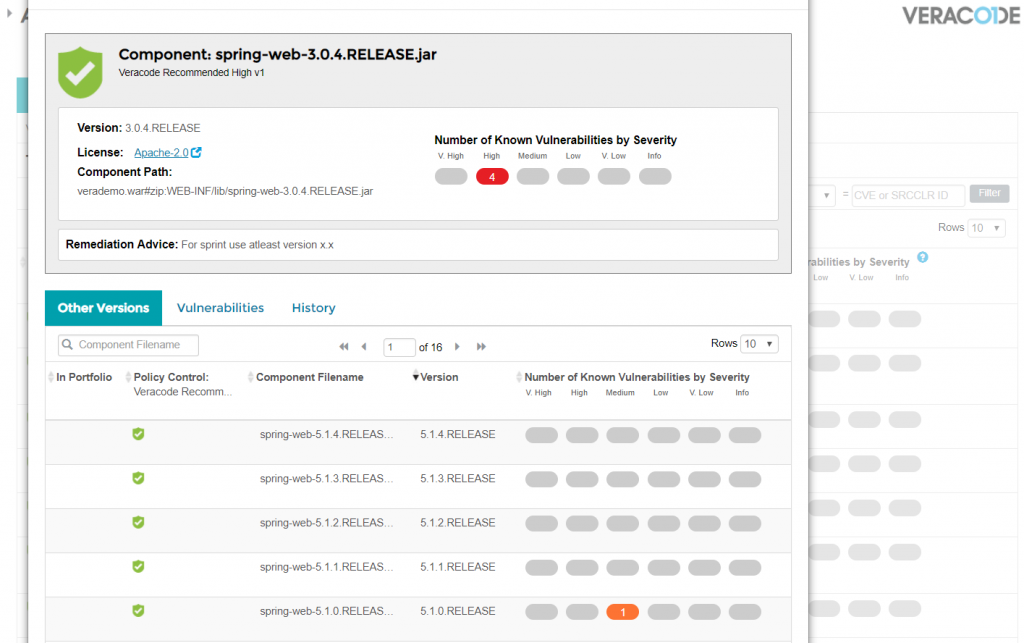 Monissa avoimen lähdekoodin kirjastoissa on lisenssejä, jolloin sovelluksen käyttäminen kaupallisiin tarkoituksiin voi tulla todella kalliiksi. Veracode huomauttaa tilanteista, joissa yritys ottaa lisenssiriskin. SCA-ratkaisu kertoo, mitkä lisenssit koskevat sovellusta, joten yritys voi tehdä tarvittavat toimenpiteet riskien ratkaisemiseksi ennen tuotantokäyttöä.
Monissa avoimen lähdekoodin kirjastoissa on lisenssejä, jolloin sovelluksen käyttäminen kaupallisiin tarkoituksiin voi tulla todella kalliiksi. Veracode huomauttaa tilanteista, joissa yritys ottaa lisenssiriskin. SCA-ratkaisu kertoo, mitkä lisenssit koskevat sovellusta, joten yritys voi tehdä tarvittavat toimenpiteet riskien ratkaisemiseksi ennen tuotantokäyttöä.
Standardit ja regulaatio
Seuraavassa on ei-kattava lista standardeista ja regulaatiosta, jotka vaativat SCA:n käyttöä.
- DORA (RTS)
- ISO 27001:2022
- IEC 81001-5-1
- ISA / IEC 62443-4-1
Tarkempia tietoa tästä blogista https://www.mintsecurity.fi/kirjastojenhallinta-sca-ja-moninaiset-viitekehykset-ja-vaatimukset/
Parhaat käytännöt käyttöön
Useat eri toimialojen säädökset, regulaatiot ja turvallisuuspolitiikat edellyttävät, että yritykset tunnistavat ja korjaavat tunnetut haavoittuvuudet sovelluksissa. Tällaisia vaatimuksia ovat esim. PCI DSS, OWASP Top 10, FS-ISAC, NIST ja HITRUST.
Kooditurvallisuuden varmistaminen vie paljon aikaa hyötyihin nähden. Tuloksena: backlogi täynnä uhkia. Ratkaisemattomat turvallisuushavainnot edustavat liiketoimintariskiä ja hidastavat ohjelmiston kehitysnopeutta. Vähennä keskimääräistä korjausaikaa (MTTR) kuukausista minuutteihin tai sekunteihin. Veracode Fix antaa kehittäjillesi arvokasta aikaa takaisin ja korjaa puutteet nopeammin. Keskimäärin Veracode Fix voi käsitellä 74 % Java-haavoittuvuuksista, jotka Veracode SAST on löytänyt, ilman, että kehittäjiesi tarvitsee kirjoittaa yhtään uutta koodiriviä.
Lue lisää Fixistä täältä – https://www.veracode.com/fix
Vastuullista tekoälyä
Vaikka avoimen lähdekoodin tarjoama ympäristö tarjoaa hyvän harjoitteludatan haavoittuvuuksien korjaamiseen, mallien myrkyttämisen potentiaali on todellinen riski. Veracode Fix on vastuullista tekoälyä käytännössä. Veracode Fix EI ole koulutettu avoimen lähdekoodin tai asiakasdatan avulla.
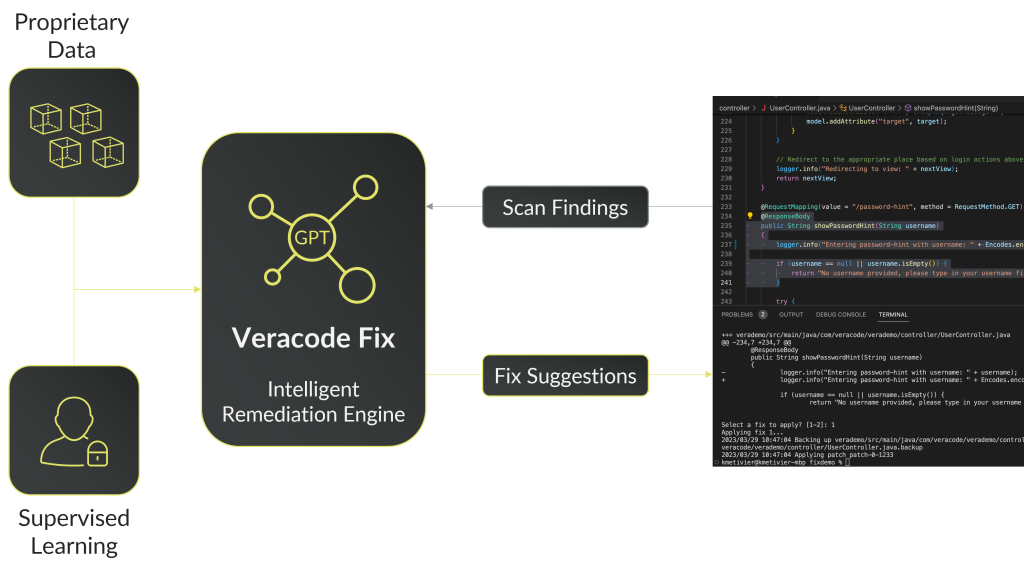
Veracode gives you the ability to scan your code, right in your favorite IDE, while you are coding. You’ll receive positive feedback when you are correctly using secure coding practices, as well as instant insight into any security flaws that are discovered.
The majority of the scans done with Veracode IDE Scan complete in seconds (mileage may vary by programming language). This means you are getting feedback before you get too far, that’s the speed of DevSecOps. Veracode IDE Scan scans files, classes, or small packages and delivers those results back to your IDE in seconds. It’s a personal security coach while you code, pointing out security flaws right away so you can fix them immediately.
This isn’t just about your code, this is about you! Our aim with Veracode IDE Scan is to help developers around the world, such as yourself, build better and more secure code. Every day you are building the applications that are powering our entire world, and we want to make sure we are giving you the tools to be successful today and tomorrow.
- No “Scan & Scold” – fix your flaw before you even commit your code
- Better remediation advice with code examples
- Positive feedback when best practices are followed
- In line education, learning as you code
- Become a better developer – build your career around it
Tuetut sovelluskehittimet
Lista tuetuista kehitimistä löytyy täältä – https://docs.veracode.com/r/IDEs
Me integroimme kaiken
Integroimisella on kaksinkertainen merkitys – integroidumme prosessiisi ja työkaluihisi.
Täydellisen ja ajantasaisen luettelon Veracode-alustaan integroimisen kaikista eri näkökohdista löydät aina osoitteesta https://docs.veracode.com/r/Veracode_Integrations
Ongelmia?
Ota yhteyttä support@mintsecurity.fi.
Olethan yhteydessä myös Veracode-edustajaasi. Lisenssisi sisältää tuen, käytä sitä hyödyksesi.
Kielituki
https://docs.veracode.com/r/r_supported_table
Paketointi
https://docs.veracode.com/r/compilation_packaging
Ajankohtaista
Kirjastojenhallinta – SCA – ja moninaiset viitekehykset ja vaatimukset
Yhä useampi standardi, viitekehys ja asiakasvaatimus edellyttää – peräti huutaa – kirjastonhallinnan perään. Huutaa siksi että modernit sovelluskehitysmenetelmät ovat täysin riippuvaisia ulkoisista kirjastoista eli riippuvuuksista.
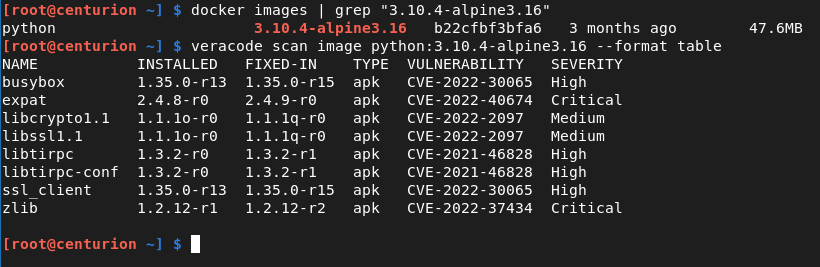
Veracode Container Securityn hyödyntäminen pilvisovellusten ohjelmistokehityksen turvaamisessa
Pilvipohjainen ohjelmistokehitys on kantava voima, koska se antaa mahdollisuuden rakentaa ja ottaa käyttöön sovelluksia vauhdilla ja skaalautuvasti. Mikropalveluiden, pilvi-infrastruktuurin ja API-rajapintojen ohella kontit (containers) ovat tärkeä osa tätä kehitysprosessia. Tutkitaanpa hieman konttien turvallisuusvaikutuksia pilvipohjaisten sovellusten kehittämisessä ja niiden aiheuttamien tietoturvahaasteiden hallintaa.

Veracode State of Software Security 12
Viime vuoden tapaan tarkastelimme aktiivisten sovellusten koko historiaa, emme vain sovellukseen liittyvää aktiviteettia yhden vuoden aikana. Näin saamme näkymän sovellusten koko elinkaareen, mikä taas johtaa tarkempiin mittareihin ja havaintoihin.

Veracode SoSS 11: Open Source Edition
Veracode julkisti äskettäin uuden version avoimen lähdekoodin kirjastojen skannausten tuloksista. Raportti antaa näkymän sovelluskirjastojen tietoturvan nykytilasta ja hieman viitteitä tulevaisuudesta. Raporttiin on koottu tulokset n. 13 miljoonasta skanauksesta yli 86 000 repositoryyn n. vuoden mittaisen ajanjakson aikana.

Veracode Webinar – Security scanning in pipelines
Tämä on webinaaritallenne 12.5.2021, jossa Julian (Veracode) ja Thomas (Mint Security) näyttävät demoja ja esittelevät ajatuksia Veracoden käyttämisestä CI/CD-putkissa.
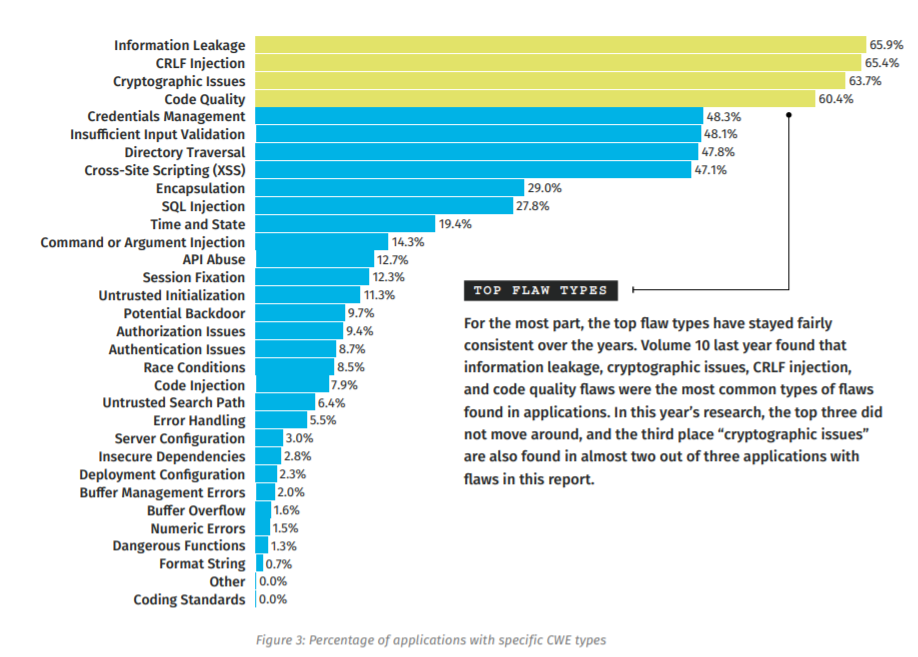
Veracode SOSS 11 – sovellusten yleisimmät tietoturvapuutteet
Veracoden vuosittaisessa tietoturvaskannausten tilastoraportissa, State of the Software Security (SOSS), listataan ja analysoidaan sovellusten yleisimpiä tietoturvapuutteita. Tarkastelun tavoitteena on ensisijaisesti auttaa tiimejä löytämään virheet ja puutteet; ja korjaamaan ne.

Veracode Security Labs Demo
Saku talks about Veracode Security Labs and gives a hands-on demo on three excercises.

Veracode – State of Software Security 11
Veracode julkaisi äskettäin vuosittaisen raporttinsa sovellusten tietoturvan tilasta. State of Software Security 11 antaa kattavan näkkymän millaisia haavoittuvuuksia sovellukset sisältävät, millaisia ne ovat, mikä niitä

Valtaosa sovelluskehittäjistä käyttää sovelluskirjastoja – alle puolet selvillä kirjastoissa piilevistä haavoittuvuuksista
Suurin osa nykyaikaisesta sovelluskehityksestä perustuu avoimen lähdekooodin kirjastoihin. Veracoden ESG-tutkimusyhtiöllä teettämän tutkimuksen mukaan yli 96 prosenttia yrityksistä ja organisaatioista käyttää avoimen lähdekoodin kirjastoja sovelluskehityksessään.

Skannasimme Koronavilkun – tässä havaintomme
Me Mint Securityssä halusimme tutustua Koronavilkku-sovellukseen ja kantaa kortemme kekoon. Koronavilkku osoittautui tietoturvaltaan hyvin korkeatasoiseksi. Merkittäviä turvallisuuteen liittyviä havaintoja emme todenneet.
Veracode Security Labs – Community Edition
Veracode Security Labs Community Edition on paikka, jossa kehittäjät voivat hakkeroida ja korjata aitoja sovelluksia, oppia uusimpia taktiikoita ja parhaita tietoturvakäytäntöjä — opastuksen kera, oikeaa koodia tutkien. Tämän yhteisöversion avulla kuka tahansa saa käyttöönsä tarvittavat työkalut sovellusten tietoturva-aukkojen tilkitsemiseen.
Veracode Security Labs
Koodarit ovat käytännössä ne ainoat henkilöt organisaatiossa, jotka voivat korjata sovelluksissaan piileskelevät haavoittuvuudet. Veracode Security Labs auttaa täyttämään tietoturvastandardien vaatimukset ja tarjoamaan samalla koko kehitystiimille mielekkään tavan oppia lisää.
