
- Laajat tietojoukot
- Joustavat integraatiot
- Kilpailuetu
Mikä on Spamhaus?
Yli 20 vuoden kokemuksellaan Spamhaus on IP-osoitteiden ja verkkotunnusten mainetietojen luotettu toimittaja. Tarkoin valittu ryhmä erittäin kokeneita tutkijoita kehittää reaaliaikaisia tietojoukkoja suojaksi haittaohjelmilta, tietojenkalastelulta, bottiverkoilta, haitallisilta sähköpostiviesteiltä ja muilta uhkilta. Tätä tietoa käytetään maailmanlaajuisesti suojaamaan monia maailman suurimmista brändeistä.
Kaikki listaukset ovat objektiivisia, ja ne perustuvat useiden toimialojen kanssa huolellisesti määriteltyihin käytäntöihin — joka tarkoittaa, että nämä tiedot ovat luotettavia 0,02 % false positive -osuudella.
Miljardit ihmiset luottavat Spamhausin tietoihin, joka päivä.

Spamhaus-tietojen integrointi
Käyttötapauksia
Tässä on vain muutamia esimerkkejä siitä, kuinka Spamhausin tuottamaa dataa voidaan integroida. Mutta mahdollisuudet ovat todellakin yhtä laajat kuin luovuutesi:
- kyberturvallisuustuotteiden tai -palveluiden parantaminen
- huonomaineisten verkkotunnusten ja/tai IP-osoitteiden näkyvyyden parantaminen data lake -laadun parantamiseksi
- sisäisen uhkatiedustelun rikastaminen
Miksi juuri Spamhaus?
- Tarkkuus – voit luottaa siihen, että listatut IP-osoitteet ja verkkotunnukset ovat oikeasti välttämisen arvoisia. Tietojemme false positive -osuus on vain 0,02 %
- Kattava uhkatiedon lähde – 80,000 datapistettä analysoidaan joka sekunti luotettujen, ainutlaatuisten kumppaneidemme ja roskapostiansojemme jakamista tiedoista.
- Asenna ja unohda – No, älä kuitenkaan kirjaimellisesti unohda. Mutta kun olet määritykset tehnyt, se on sitten siinä. Täällä ei ole parantuneen uhkatiedon lisäksi enää muuta tehtävää.
- Luotettu – yli 20 vuoden kokemuksella tietojamme käyttävät planeetan suurimmat brändit.
Tietojoukkojen esittely
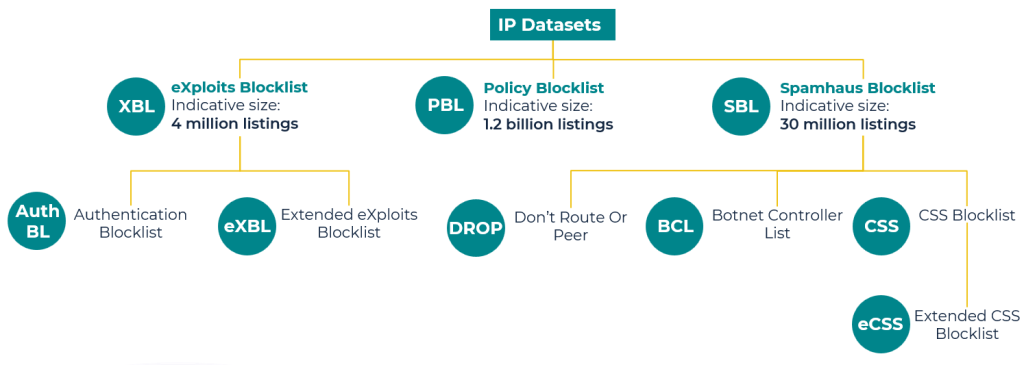
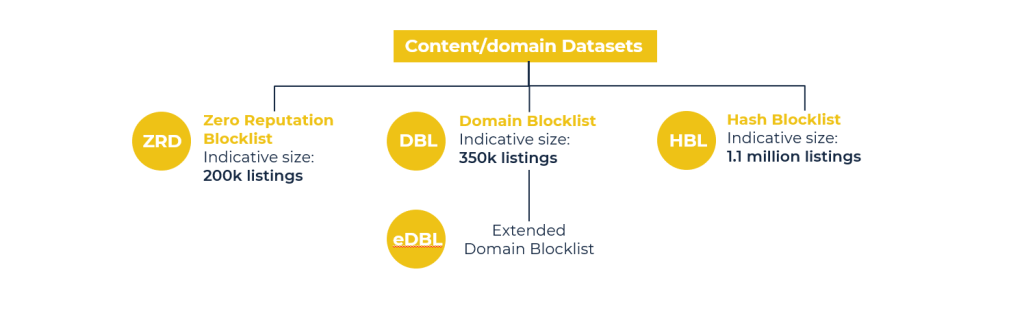
Tietomme on pakattu IP-osoite- ja sisältötietojoukkoihin. Voit tilata molemmat, jomman kumman tai osajoukon — käyttötapauksestasi riippuen.
Hinnoittelu
Tietojoukkojen hinnoittelu all-inclusive -lisenssillä ja globaalilla, rajoittamattomalla pääsyllä tietoihimme on kuusinumeroista. Mitä enemmän voimme määritellä käyttösi (tietojoukkojen lukumäärä ja lisenssiehdot), sitä paremmat mahdollisuudet meillä on räätälöidä hinta juuri sopivaksi.
Joka tapauksessa, sinun on otettava yhteyttä myyntiimme – olemme täällä auttamassa!
Blogikirjoitukset
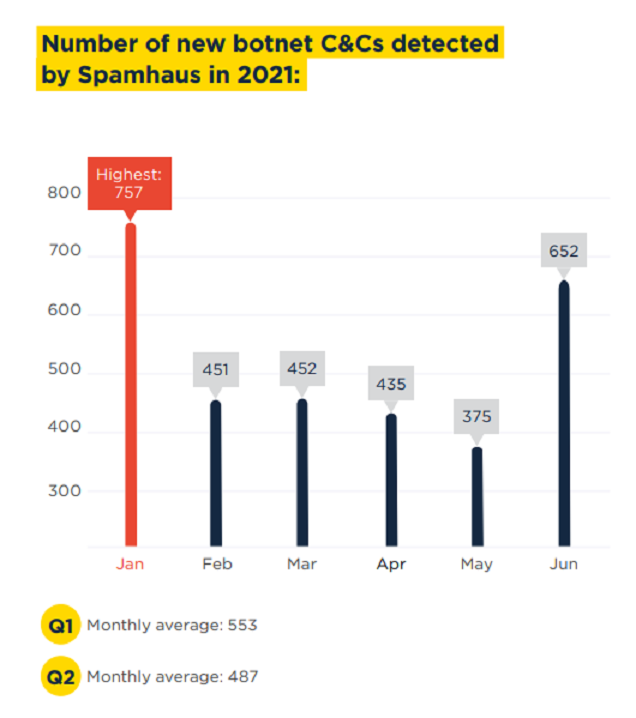
Spamhaus Botnet Threat Update Q2/2021: Emotetin jälkien siivousta
Spamhausin heinäkuussa ilmestyneen raportin hyvä uutinen oli, että havaittujen uusien botnetien komentopalvelimen määrä oli 12 % alhaisempi kuin edellisellä kvartaalilla. Sen sijaan huono uutinen on väärinkäytösten runsas määrä johtavien pilvipalveluiden tarjoajien, kuten Microsoftin ja Googlen, alustoilla.

Spamhaus Botnet Threat Update Q1/2021: Emotet on poissa, mutta muita uhkia on tullut tilalle
Spamhausin raportissa tuodaan heti esille hyvä uutinen. Tammikuussa 2021 eri maiden viranomaiset Euroopassa ja Yhdysvalloissa käynnistivät operaation pahamaineista Emotet-botnetia vastaan. Operaatiossa viranomaisten onnistuivat sulkemaan Emotetin käyttämät palvelimet.

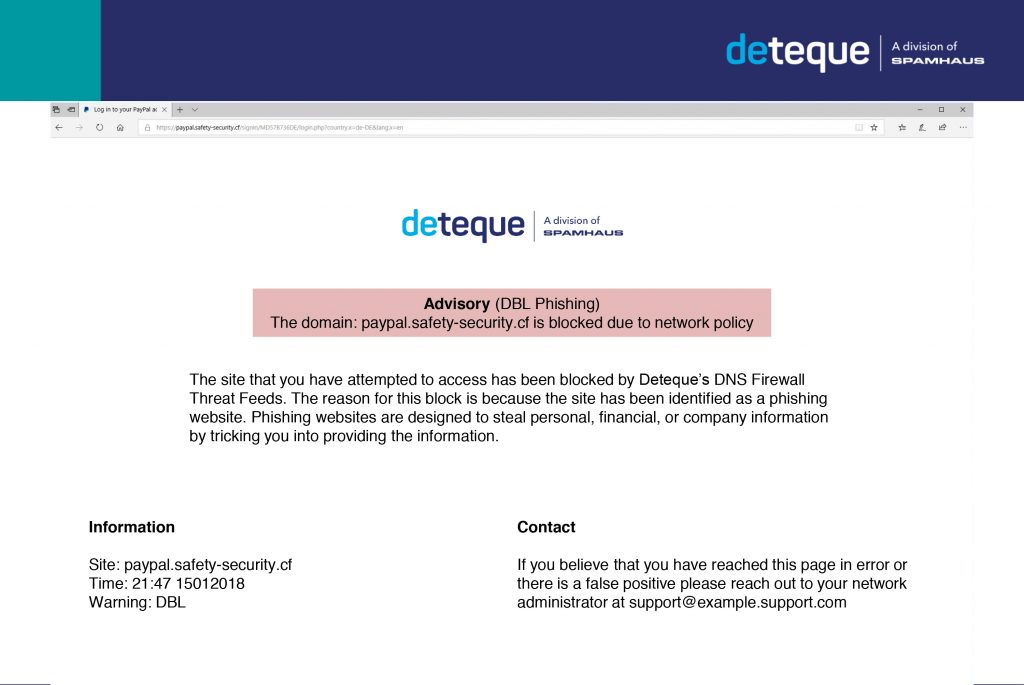
Kymmenen kysymystä potentiaaliselle DNS -palomuuripalvelun toimittajalle
Tässä kirjoituksessa esitellään muutamia keskeisiä kysymyksiä, jotka on hyvä esittää potentiaaliselle DNS -tasolla toimivan palomuurin toimittajalle (ja myös omassa organisaatiossasi, jotta varmistetaan, että yritykseen valitaan oikea palvelu. Aloitetaan perusasioista.
Spamhaus DNS Firewall – Lyhyt johdanto
Yksinkertaisimmillaan DNS Firewall estää ja ohjaa loppukäyttäjiä menemästä haitallisille verkkosivuille, samoin kuten perinteisetkin palomuurit. Keskeinen ero näiden välillä on se, että DNS Firewall -palvelua käytetään eri verkkokerroksessa ja eri vaiheessa.

Paras teho irti Spamhausin estolistoista
Spamhaus tuottaa useita erilaisia estolistoja (DNSBL) domain-listoista IP- ja hash-listoihin. Jokaisella estolistalla on oma erityinen kohteensa sähköpostin eri osissa, joissa voi ilmetä haitallista toimintaa.
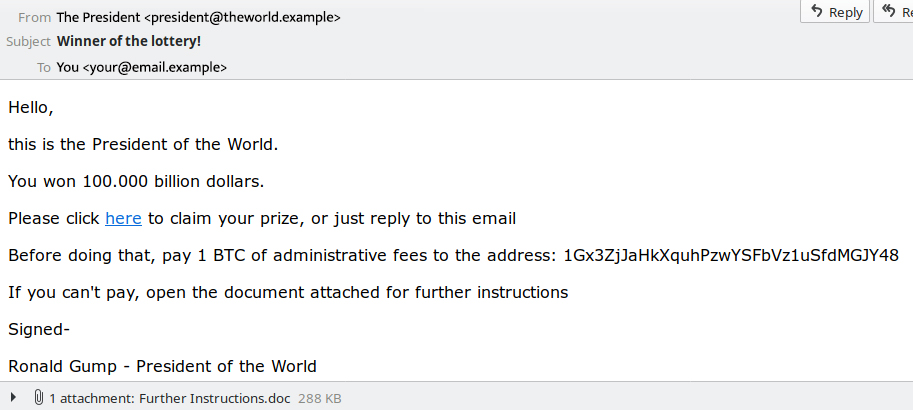
Miten haitallisen sähköpostin lähdekoodi eroaa tavallisesta
Kun käyttäjä lukee saapunutta sähköpostia, ei ole aina ilmiselvää, onko viesti turvallinen vai ei. Sähköpostiviestin lähdekoodi saattaa kuitenkin antaa vihjeitä haitallisuudesta. Spamhausin estolistoja käyttämällä voidaan haitallinen sähköposti saada suodatettua.
