- Multi-dimensional views of network traffic
- Log and data volume reduction
- Flow data enrichment
NetFlow Optimizer enhances capabilities of existing SIEM systems
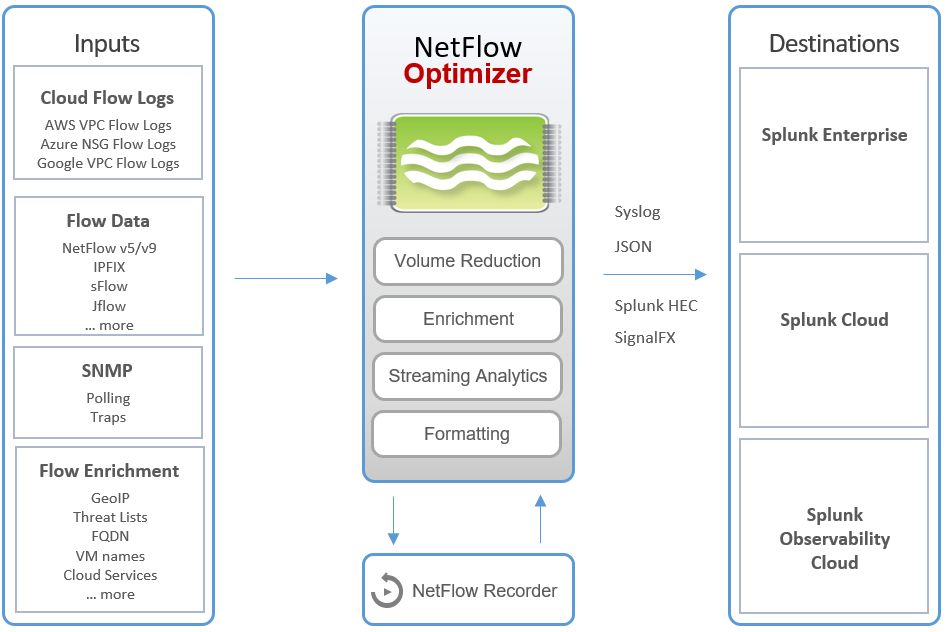
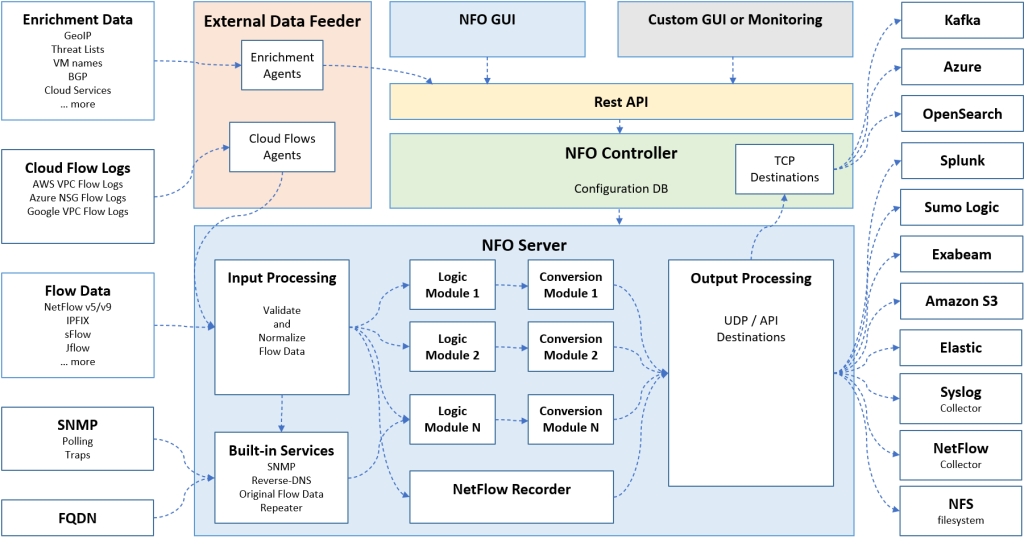
NetFlow data offers a comprehensive view of network traffic, enabling organizations to proactively detect security threats, monitor user activity, and gain valuable insights for effective network management and optimization. NetFlow Optimizer enables you to efficiently process large volumes of diverse NetFlow data, including IPFIX, JFlow, sFlow, and Cloud Flow Logs from Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP). It ensures real-time optimization and enrichment, delivering data exactly where you need it, in the right formats. NetFlow Optimizer is offering support for SNMP Polling and SNMP Traps, further enhancing its capabilities for comprehensive network monitoring.
Reduce amount of data – save money
Data Volume Reduction (DVR) is a process of reducing the amount of data that needs to be stored and processed. This can be done by consolidating, deduplicating, or filtering data.
Enrich data – add context
Netflow Optimizer enriches flow data with DNS names, VM names, application names, user identity, cloud instance names & services & regions, SNMP polling data, GeoIP and reputation based on threat lists.
NetFlow Optimizer, a high performance flow processing engine, receives flow data from network devices and virtual public clouds, consumes and enriches flow information with other data, translates it to syslog, JSON, or other formats, and sends it to other systems where it is then correlated with other machine data and visualized.
NetFlow data is notoriously voluminous
Traditionally, all NetFlow records generated by network devices are captured and stored for further interpretation. This exact process of capturing all NetFlow records, without understanding the significance of information contained in the records’ data, creates tremendous storage and data analysis problems. A mid-range 20 Gb device in a large office can process tens of thousands of network exchanges per second, which results in a hundred thousand NetFlow records per second. Assuming that each NetFlow record is 100 bytes long, storing data at this rate it would take 8.6TB of disk space every day. Even a smaller switch, router or firewall that processes 10 times less network connections produces 860GB of flow data every day.
Modular approach
Netflow Optimizer is modularized. By enabling appropriate Modules, you turn on specific functionality within NetFlow Optimizer.
For example, you can monitor:
- your network conversations and hosts’ behavior
- your network devices
- malicious host (e.g. botnets, scanning hosts)
- communications to your data center
… and many other use cases are expressed via the Modules.
Deployment
Depending on the hardware specification a single NFO instance (virtual machine) is capable of processing up to 1,000,000 flows per second without a single drop.
SIEM – and beyond
You can output the data into several destinations at once, for example to plain syslog, S3 buckets, Azure Blog Storage, directly to disk, Splunk or Azure Log Analytics.
Splunk Architecture
NetFlow and SNMP Analytics for Splunk App relies on *flow data processed by NetFlow Optimizer™ (NFO) and enables you to analyze it using Splunk® Enterprise or Splunk® Cloud.
NetFlow data is sent to Splunk from NFO in syslog or JSON formats. Weather you use Splunk Enterprise or Splunk Cloud, configure your Splunk Data inputs accordingly per your accepted best practices.
For a complete overview of the Splunk integration, see the documentation https://docs.netflowlogic.com/integrations-and-apps/integrations-with-splunk/
Splunk App
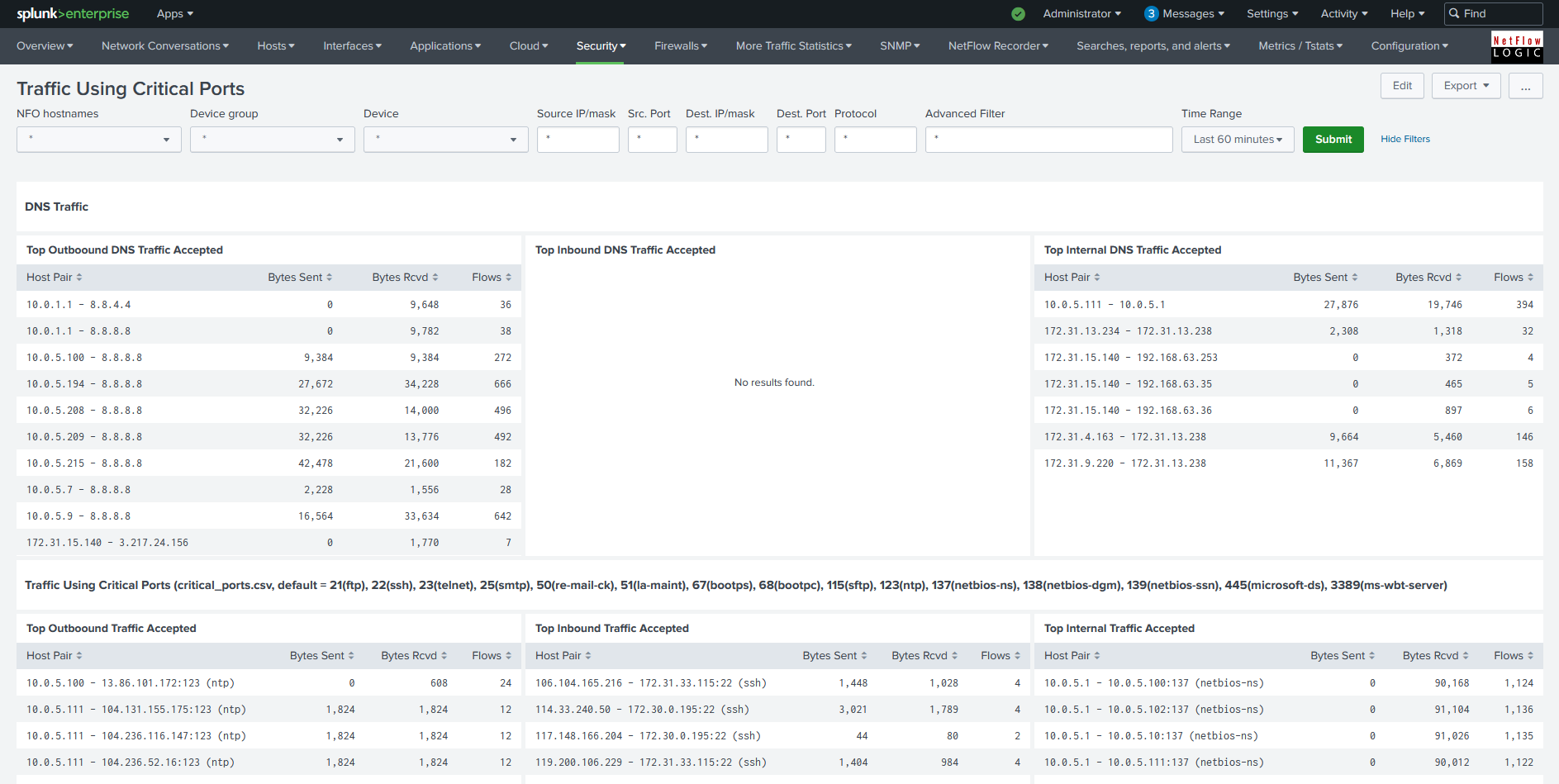
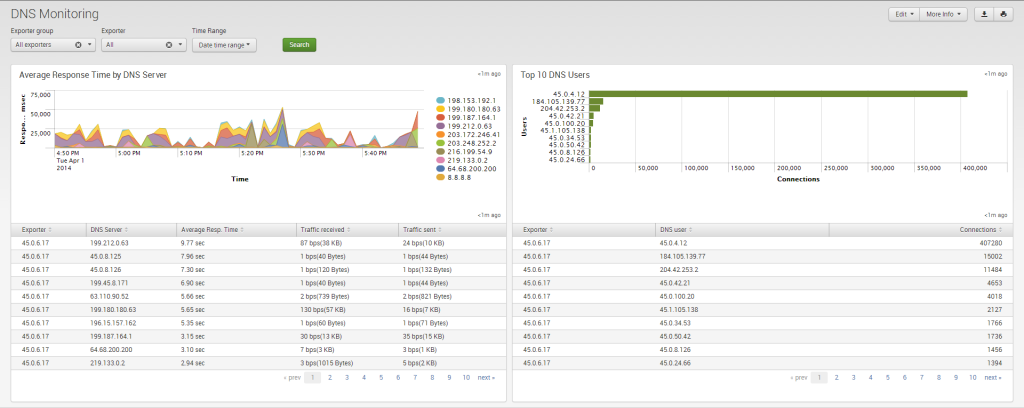
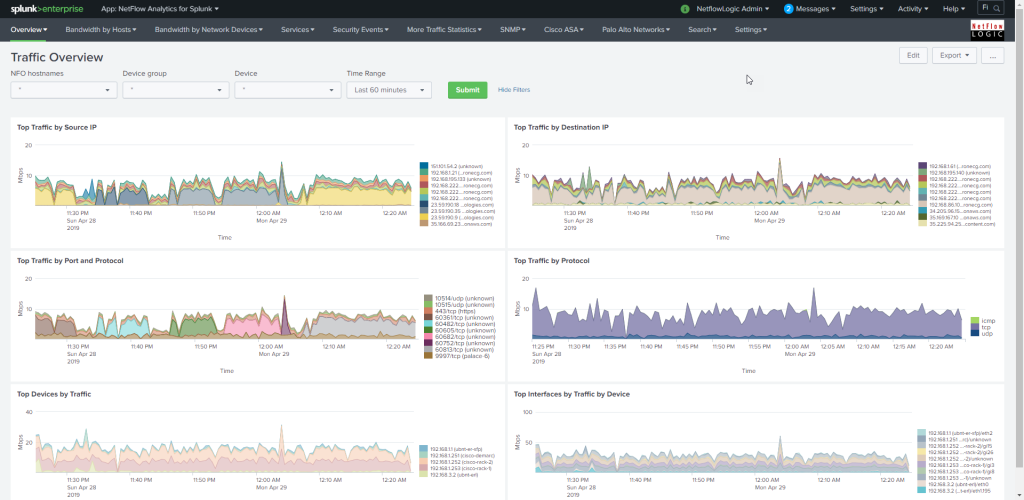
For a complete listing of the various views into the data using Splunk, please review https://docs.netflowlogic.com/integrations-and-apps/integrations-with-splunk/netflow-analytics-splunk-app/dashboards/
Sentinel Architecture
You can integrate NetFlow Optimizer with Microsoft Azure Sentinel by sending NFO data directly to Azure Analytics Workspace.
For a complete overview of the Sentinel integration, see the documentation https://docs.netflowlogic.com/integrations-and-apps/integration-with-azure-sentinel/
Dashboards
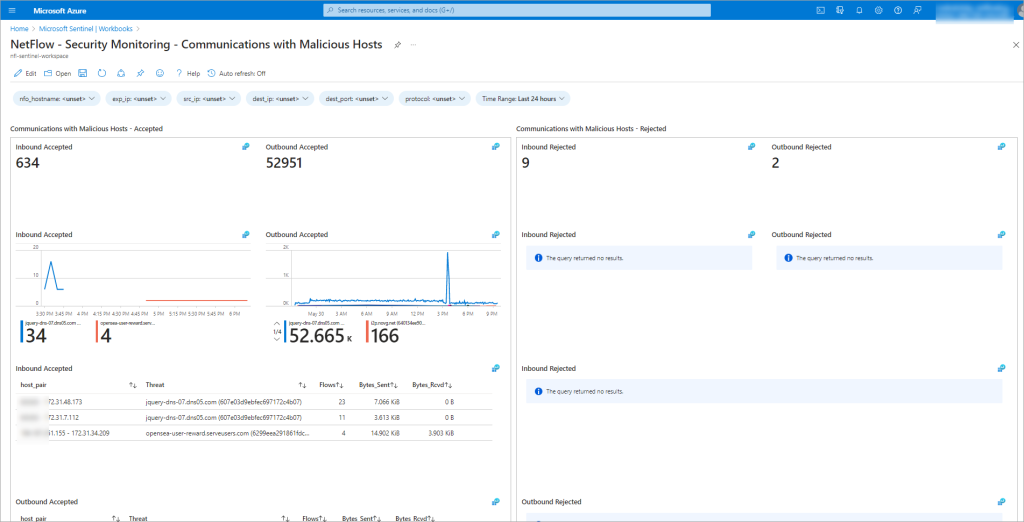
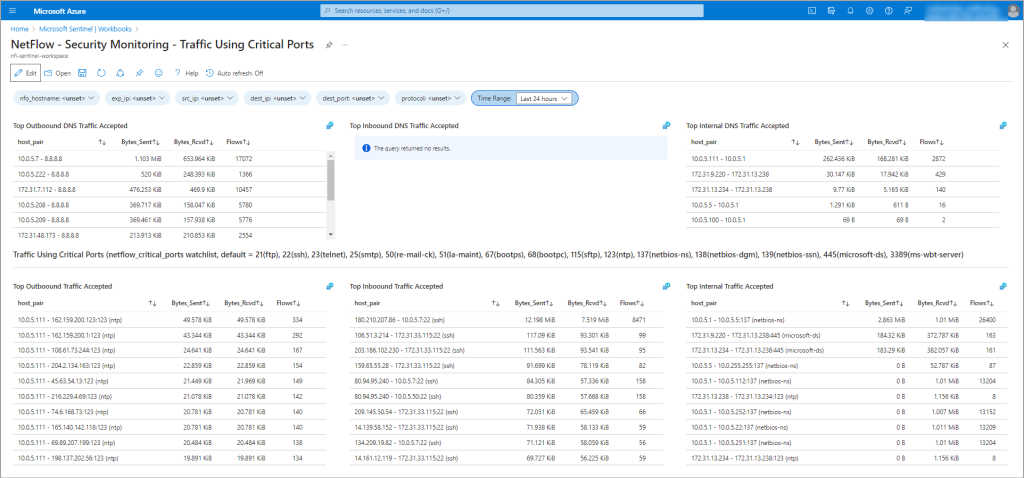
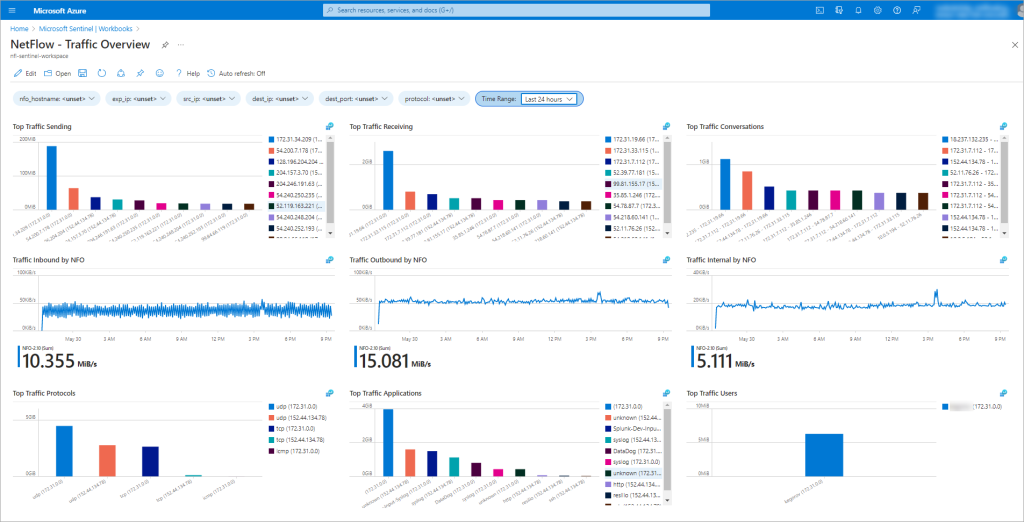
DDoS traffic detection capabilities
This solution brings new anomalous traffic detection capabilities to businesses by providing early detection of DDoS attack before network devices and servers targeted by DDoS are incapacitated.
For a complete overview of the capabilities, please refer to the documentation https://docs.netflowlogic.com/solutions/netflow-based-ddos-detection/introduction
DDoS attacks are notoriously difficult to detect timely and defend against. Traditional perimeter based technologies such as firewalls and intrusion detection systems (IDSs) do not provide comprehensive DDoS protection. Solutions positioned inline must be deployed at each endpoint, and are vulnerable in case of a volumetric attack. Even if using BGP-based DDoS-scrubbers, visibility into the traffic is very limited, usually defaulting to whether or not the scrubber is currently active (“on”/”off”).
Baselining out of the box
Typically, solutions require systems to run in “learning” mode, passively monitoring traffic patterns to understand normal behavior and establish a baseline profile. The baseline is later used to detect anomalous network activity, which could be a DDoS attack. These takes a long time to implement and any change in the infrastructure makes baseline obsolete, and results in lots of false positives.
In contrast to the inline solutions, NetFlow Logic’s DDoS Detector solution is based on the flow information analysis, thus it is not susceptible to volumetric flood attacks. Also, it does not rely on baseline data collection, which may take days or weeks. Instead, NetFlow Logic’s anomalous traffic detection solution uses an innovative approach which makes it operational in 15-20 minutes after deployment.
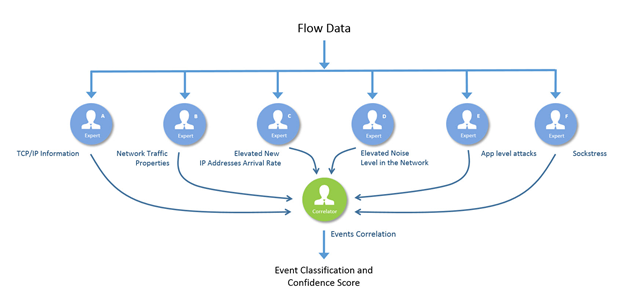
NFO detector module
This Module consists of six independent components, which we call experts, each specializing in its own domain of knowledge. All experts process all the flow records received by NetFlow Optimizer, apply their own analytics, and, if an attack is detected, send messages to the events correlator, indicating the type of detected attack, confidence level, and a trend of the event characteristics dynamics (increasing, steady, or abating). The event correlator combines the information received from the experts, assigns weight to each reported event, and makes a final determination on reporting and its confidence in event validity.
A list of detected attack types can be found here – https://docs.netflowlogic.com/solutions/netflow-based-ddos-detection/ddos-detector-module/types-of-ddos-attacks-detected-experts
Current Hot Topics

Network Management Best Practices: Optimizing Performance And Security
In the digital age, businesses rely heavily on their networks to function efficiently. However, managing and maintaining a complex network can be a daunting task. By implementing effective network management best practices, organizations can ensure optimal performance, enhance security, and minimize downtime.

Leveraging NetFlow For Network Security And Threat Detection
In the ever-evolving landscape of cybersecurity, staying ahead of sophisticated threats demands innovative solutions. One such game-changer is NetFlow, a technology that unlocks a treasure trove of network traffic data. By leveraging NetFlow, organizations gain the upper hand in safeguarding their networks and detecting potential threats.