
- Extensive datasets
- Flexible integrations
- Competitive advantage
About Spamhaus Technology
With over 20 years experience, Spamhaus is the trusted authority on IP and domain reputation data. A hand-picked team of highly experienced researchers develop real time datasets to safeguard against malware, phishing, botnets, malicious email, and more. This intelligence is used globally to protect and inform many of the world’s biggest brands.
All listings are objective, based on policies carefully defined with the wider industry, meaning this data is dependable with a 0.02% false-positive rate.
Spamhaus’ data is relied on by billions of people every day.

Spamhaus data for integration
Use cases
Here are just a few examples of how the data might be integrated – but the opportunities really are as vast as your creativity:
- enrich cyber-security products or services
- increase visibility of bad domains and/or IPs to enhance data lake quality
- improve internal threat intelligence
Why this data?
- Accuracy – have confidence that listed IPs and domains are legitimately bad. Our data has a 0.02% false positive rate.
- Comprehensive source of threat intel – 80k data points analyzed each second from data shared by trusted, unique partnerships and spam traps.
- Set and forget – well, not literally forget! But once you’re configured, that’s it. Nothing more to do than see improved threat intelligence
- Trusted – with over 20 years’ experience, our data is utilized by some of the biggest brands on the planet
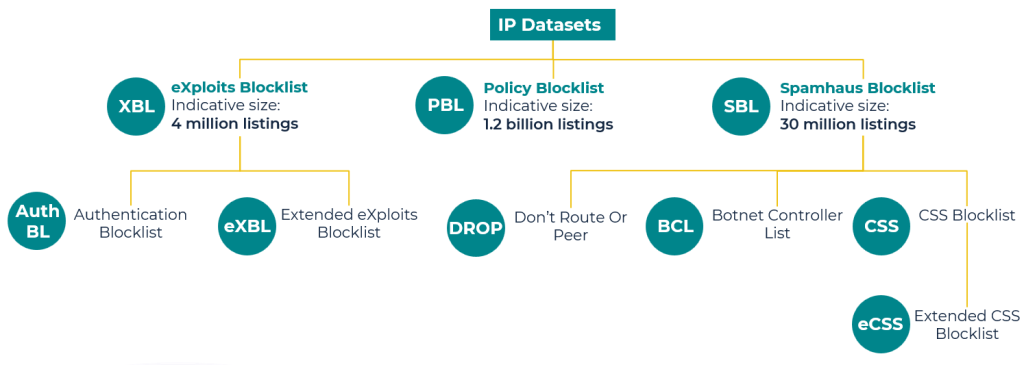
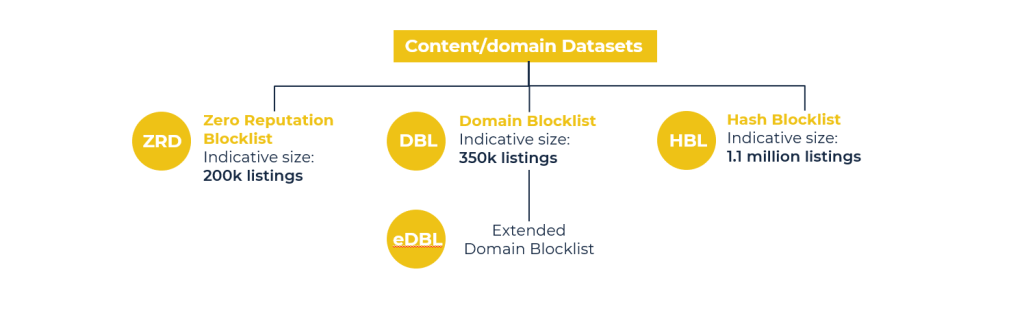
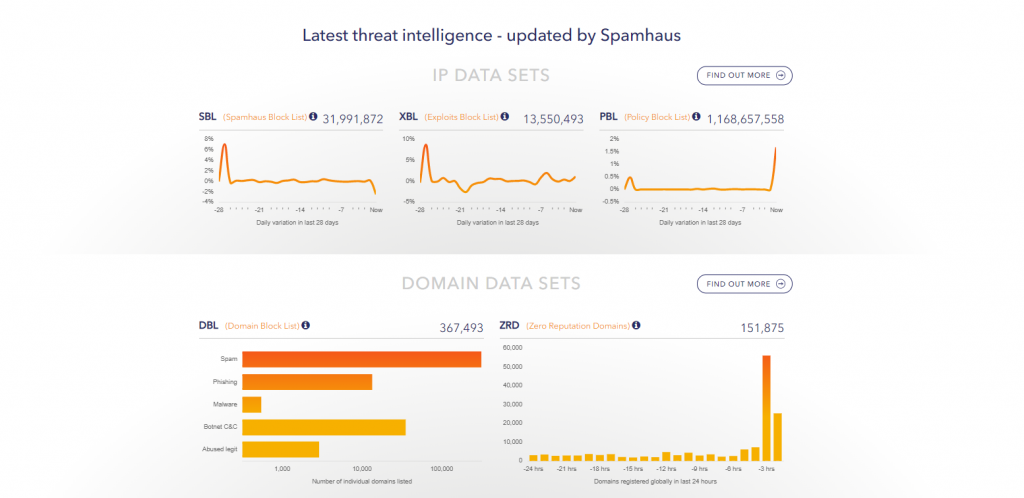
An overview of the datasets
Our data is packaged up into IP and Content datasets. You can subscribe to both, either, or a subset, depending on use case.
Pricing
The pricing of the datasets with an all-inclusive license, global, unlimited access to our data is six figures. The more we can define your usage (number of datasets and specific licensing terms), the better the opportunity to tailor the price.
In any case, you need to contact sales – we are here to help.
Featured blogs

Webinar: Domain hijacking – a prevalent problem
The threat landscape is constantly changing as cybercriminals continually try to avoid detection, and increase the number of legitimate resources they can utilize. Recently domain hijacking has become more prevalent. Every day this year, Spamhaus has observed over a 100 hijacked domains at one single domain registrar.
Mint Security to resell Spamhaus services
Mint Security starts to resell and support Spamhaus’s services in Finland. Block lists provided by Spamhaus protect 3 billion mailboxes every day. Spamhaus also operates in DNS services and BGP routers.
Spamhaus Botnet Threat Report 2019 – A comprehensive overview how criminal botnets work
Researchers at Spamhaus Malware Labs identified and blocked 17,602 botnet C&C servers hosted on 1,210 different networks. That is an enormous 71.5% increase from the number of botnet C&Cs seen in 2018. Since 2017, the number of newly detected botnet C&Cs has almost doubled from 9,500 to 17,602.

Botnet command & control domain registrations go through the roof in 2018
When Spamhaus Malware Labs observe a 100% increase in the number of domains that are being registered by cybercriminals to host a botnet command & control (C&C) it’s time to stop. Cybercriminals prefer to use a domain name registered exclusively to host a botnet C&C
