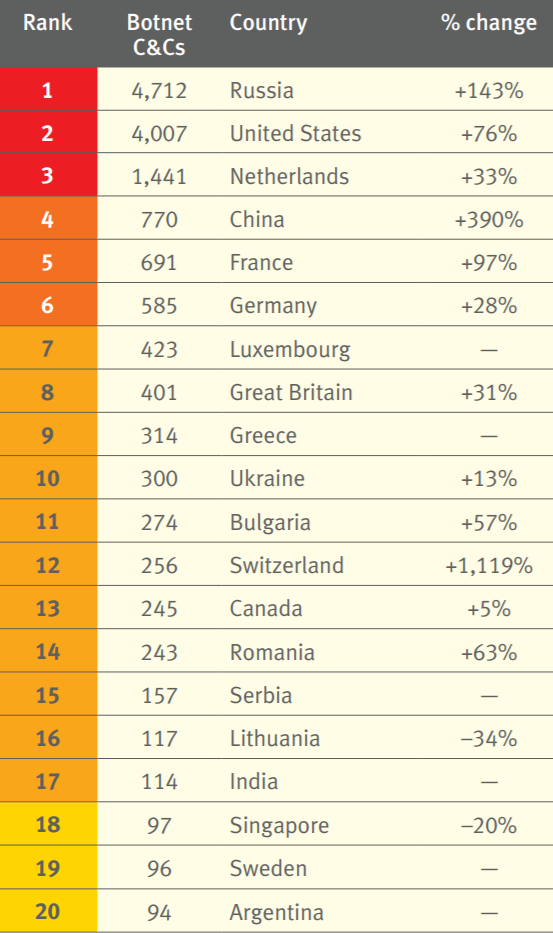
Researchers at Spamhaus Malware Labs identified and blocked 17,602 botnet C&C servers hosted on 1,210 different networks. That is an enormous 71.5% increase from the number of botnet C&Cs seen in 2018. Since 2017, the number of newly detected botnet C&Cs has almost doubled from 9,500 to 17,602.
Botnet growth
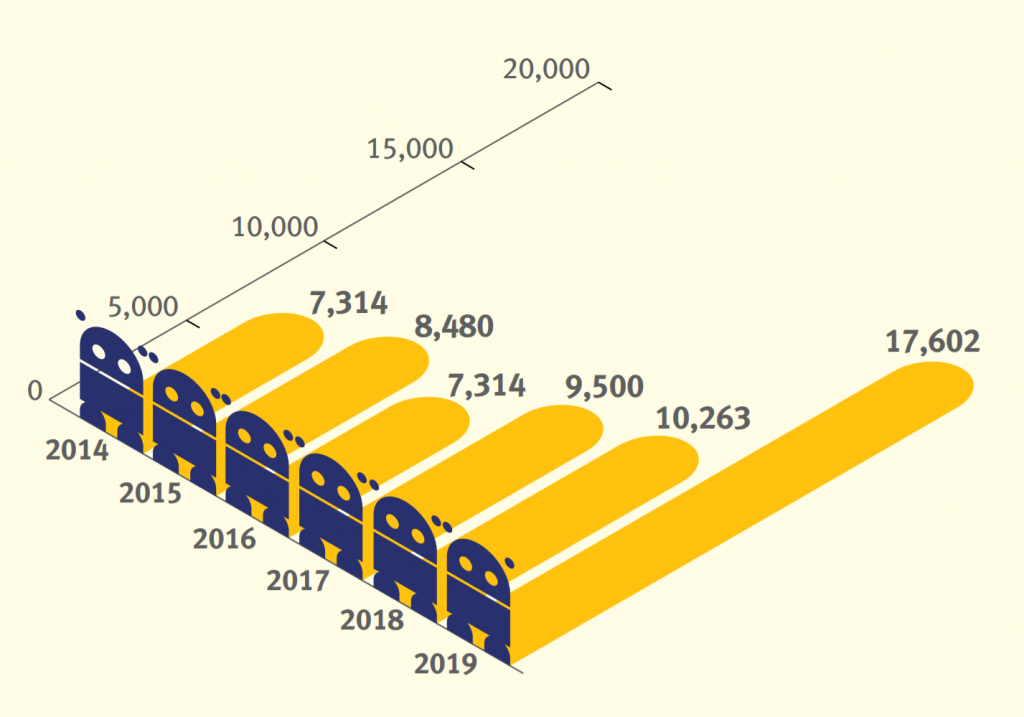
Statistics from SBLs reveal the "popularity" of botnets
To understand how ‘popular’ botnet C&Cs were as a cybercriminal’s vector of choice in 2019, we reviewed the Spamhaus Block List (SBL). We looked at how many listings on this blocklist were issued for botnet C&Cs. In 2019, almost every other SBL listing issued by Spamhaus was for a botnet C&C server, another significant annual increase:
Botnet controllers - a brief explanation
A ‘botnet controller,’ ‘botnet C2’ or ‘botnet command & control’ server, is commonly abbreviated to ‘botnet C&C.’ Fraudsters use these to both control malware infected machines and to extract personal and valuable data from malware-infected victims.
Botnet C&Cs play a vital role in operations conducted by cybercriminals who are using infected machines to send out spam, ransomware, launch DDoS attacks, commit e-banking fraud, click-fraud or to mine cryptocurrencies such as Bitcoin.
Desktop computers and mobile devices, like smartphones, aren’t the only machines which can become infected. There is an increasing number of devices which are connected to the internet, for example, the Internet of Things (IoT) devices, such as webcams, or network attached storage (NAS). These are also at risk of becoming infected..
A legal DDoS without botnets?
Statistics 2019