Concept
Objectives
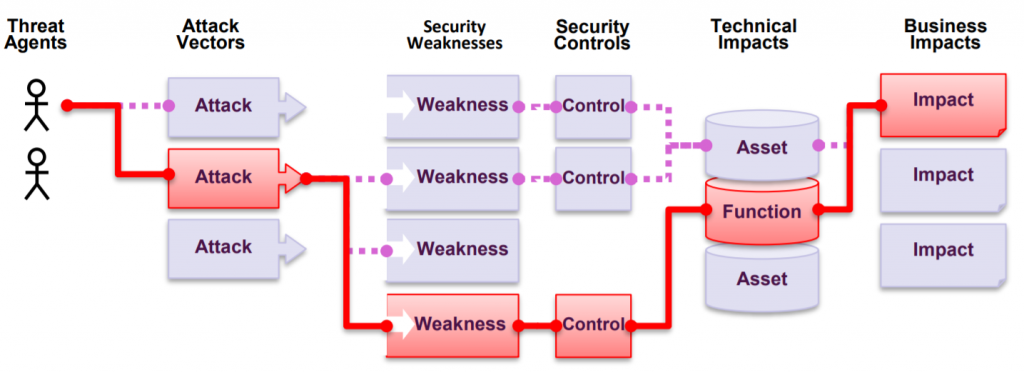
The purpose of the test is to simulate the intentions of a malicious attacker and to verify the operation of the application in an exceptional situation. The goal is usually to find the most common errors in the application. This is a very good approach especially if you are testing an application or system for the first time.
The testing criteria are well-known and generally accepted standards and checklists, especially those created for the security assessment of web applications, The most widely used checklist is the OWASP top-10, which covers the most common vulnerabilities in web applications, and this checklist is maintained and reviewed regularly. Therefore, by default, you can always be confident that by following the OWASP top-10 as the primary testing criterion, you are testing the right things.
Other testing criteria may be, for example, SANS 25 or an industry-specific testing framework such as PCI-DSS.
Source code reviewing may also be used to support penetration testing. Most often, source code reviewing is used to support penetration testing and the source code is not read line by line. If the source code is reviewed in more detail, the OWASP ASVS framework is often used as a support method.
Scanning supports testing
Targets
Specifics
Things to consider
If the system is protected by technical controls that prevent penetration testing (IDS / IPS, WAF web application firewall, ratelimiter, autoban system, blacklists,…), these should be switched off in order to successfully complete penetration testing. These technical controls effectively prevent penetration testing – testing of these technical controls must be performed separately if the situation and scope so require.
Although testing is performed with the utmost care and in accordance with good professional ethics, it is possible that the systems will be damaged or interrupted during testing. It is the customer’s responsibility to take care of the preparation. The auditor always keeps the client up to date in the event of any problem situations.
Testing can always be performed from specific IP addresses, allowing these IP addresses to be whitelisted for the duration of the tests.
Finally
Penetration testing is a basic tool for information security. Testing should be performed with the development teams involved and, in addition to the report, given the opportunity to ask the auditor directly for clarifications and tips to correct problems.
To help the development teams, a security hackathon can also be set up, where the developers themselves can try out the pentesting.

Auditing
Auditing Auditing in short Auditing means many things. For us, it means customized reviews of systems, environments and processes for our customers. In addition to






