Dive into the world of the E's
Security
For security in key exchange, ALWAYS prefer the latter E (ephemeral) over the former E (EC). Security over speed. Always. Luckily, you can (and should) have both – ECDHE. So, in order of preference here:
- ECDHE
- DHE
- ECDH
Speed
- Speed in key exchange. DHE is slowest. ECDHE is still slower than RSA. RSA is the speed king.
- Speed overall. If ECC is used in both the certificate (ECDSA) as well as the key exchange (ECDHE), it is almost as fast as RSA on a comparative security level (RSA 2048).
PFS (Perfect Forward Secrecy or just forward secrecy) is NOT a result of any ECC, it is a result of the “latter E” in ECDHE or DHE. It stands for ephemeral.
ECC has benefits in both the certificate signature algorithm as well as the key exchange. Both must (and should) be enabled separately.
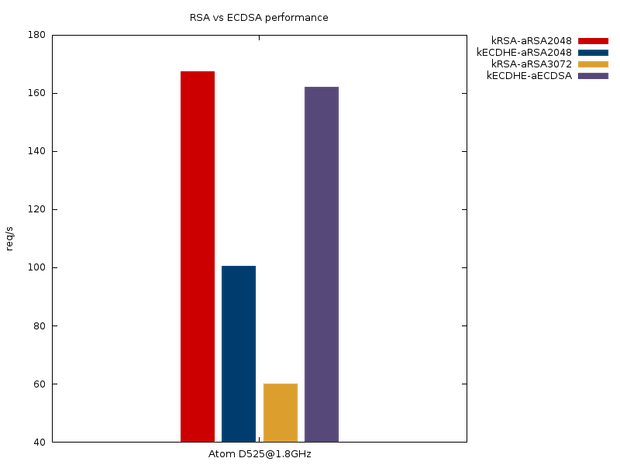
Picture 1. Speed comparison chart from Hubert Kario's blog
Mid-post wrap-up:
- ECDHE-RSA means that ECC is used in the key exchange with EPHEMERAL Diffie-Hellman – using an RSA-certificate
- ECDH-RSA means that ECC is used in the key exchange with NORMAL Diffie-Hellman – using an RSA-certificate
- ECDHE-ECDSA means that ECC is used in the key exchange with EPHEMERAL Diffie-Hellman – using an ECC-certificate
- ECDH-ECDSA means that ECC is used in the key exchange with NORMAL Diffie-Hellman – using an ECC-certificate
Configuration
For compatibility, one has to provide both RSA- end ECDSA-certificates for most end-user services. This means having two different certificates signed by your CA. In addition it also means two different CA-chains to be maintained. These things may or may not be an issue, but should be considered and remembered.
NOTE! An RSA-certificate and a ciphersuite starting with ECDHE-ECDSA will NOT enable
ECC-certificates – because you haven’t generated one (you are not alone – 2048 bit RSA is still at 90.6%
according to this source: https://securitypitfalls.wordpress.com/2015/02/01/january-2015-scan-results/).
Lessons for the reader
- Don’t let yourself become confused by the different E’s (elliptic vs. ephemeral)
- Techniques (algorithms) may be used in certificates, key exchanges, signatures and MAC’s. One technique might be really bad in one context, and totally OK in another (example: SHA-1 as a hash for handshakes in TLS is pretty OK, but SHA-1 as a hash for a certificate is not).
- Using EC key exchange does not automatically mean PFS or ephemeral. They are two different server side configuration options (as can be seen in the list above)
Links and TL/DR
The mozillawikipage is regarded as the de-facto standard (and a true TL/DR!) for configuring SSL/TLS and can be found here:
Other good links on these beasts and the speed of them can be found here:
- Comments on DHE and ECDHE-performance:
- Speed comparisons:
- A bunch of different algorithms, just to be able to compare how they look:
- “Elliptic Curve Cryptography for those who are afraid of maths” by Martijn Grooten (Virus Bulletin):





