Developers are, in effect, the only people in any organization who can fix vulnerabilities hidden in their applications. Nevertheless, in most cases they do not undergo the training to be able to find and fix vulnerabilities, and put applications to production, without even the most common security holes.
Developers are asked a lot
Why is the security training of software developers lagging behind it’s goals? Most common reasons for this are:
- Content of the training is tooo long (and boring)
- The content is not relevant in relation to the organization’s tech stack
- The approach to learning is wrong and does not engage or inspire the learners enough
Infosec standards like it
ISO27001
OWASP SAMM
OWASP SAMM is a community driven maturity model based on self-assessment that seeks to raise awareness and train organizations on how to design, develop, and deploy secure software. SAMM’s Education & Guidance practices address security education on three maturity levels:
On level 1, security training is provided to all personnel groups, in particular to those who are in some way involved with secure software development processes. The goal is to increase awareness of security threats and risks to applications, learn about best practices and the principles of secure software design. OWASP Top 10 vulnerabilities should be covered at a general level.
Level 2 offers more tailored training, according to various roles. The training should be related to the technologies and techniques used in the company, starting from the core of the development team. Content is adapted for product managers, software developers, testers, and security auditors based on the technical needs of each group.
On level 3, the goal is to develop internal training programs.
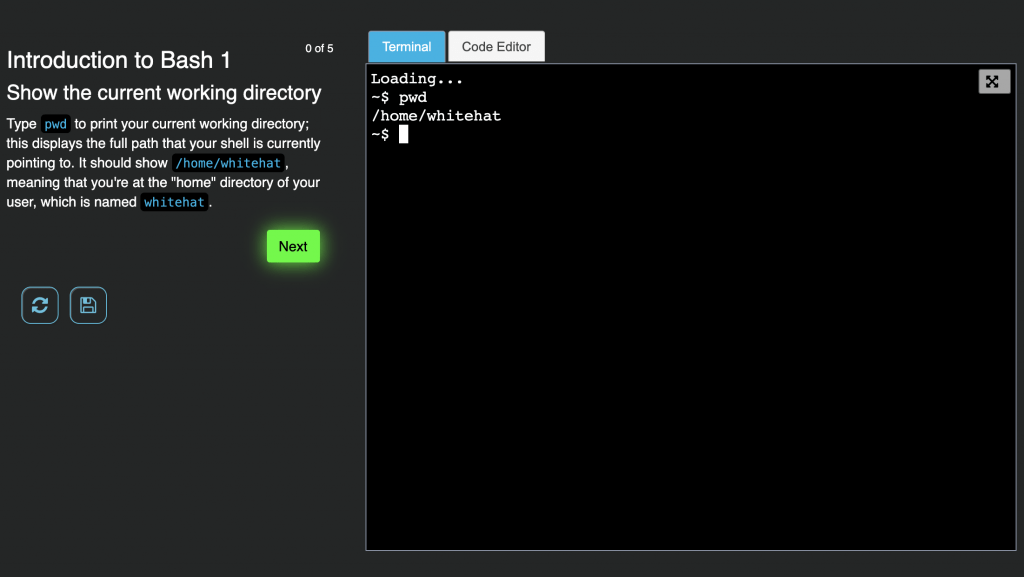
Veracode Labs goes straight to the point
“Interactive” training solutions typically simulate a web application instead of using real code. Disadvantage of this approach is that even if a developer passively looks at code snippets, he or she might never actually touch the keyboard. Without hands-on training, the situation often is that no actual learning has taken place, because participants merely click on different multiple-choice answers until the lesson is over.
Shift left!
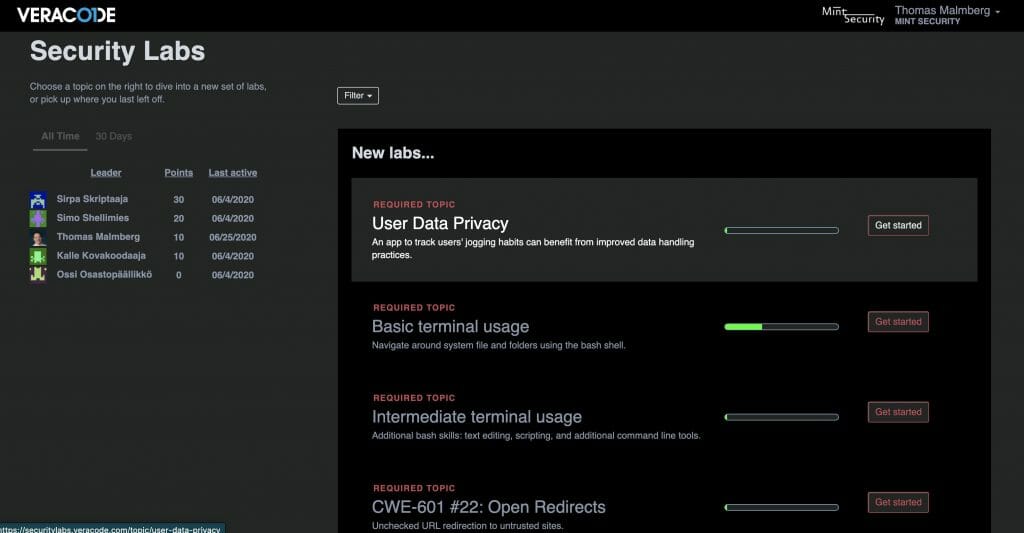
Security Labs shifts application security to the left, preparing and strengthening developers’ capabilities to respond to modern threats by leveraging and fixing real code, and applying DevSecOps principles to deliver protected code in a timely manner.
Through hands-on exercises, developers learn skills and strategies that are directly applicable to the code generated by the organization. Detailed progress reporting and a scoreboard encourage developers to continually hone their coding skills.
Create more secure software
More information
- Watch a demo here: https://share.vidyard.com/watch/eiL5tYWaUQVB55x3debySD?
- Read more from Veracode: https://www.veracode.com/products/security-labs
If you want a hands-on livedemo, contact us. We can share test accounts or setup a demo-environment if needed.
Veracode
SAST – Static Application Security Testing SCA – Software Composition Analysis SDLC Integration Manage Your Entire Application Security Program on a Single Platform Veracode’s unified
3rd party library management – SCA – various frameworks and requirements
Yhä useampi standardi, viitekehys ja asiakasvaatimus edellyttää – peräti huutaa – kirjastonhallinnan perään. Huutaa siksi että modernit sovelluskehitysmenetelmät ovat täysin riippuvaisia ulkoisista kirjastoista eli riippuvuuksista.

Veracode State of Software Security 12
Similar to last year, we looked at the entire history of active applications, not just the activity associated with the application over one year. By doing so, we can view the full life cycle of applications, which results in more accurate metrics and observations.
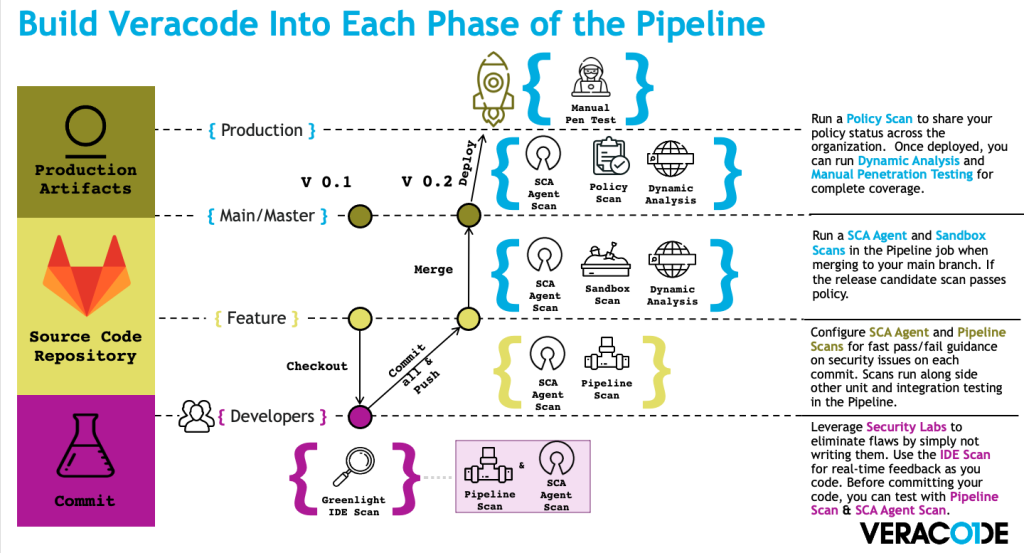
Hands-on Veracode guidelines for Azure, Gitlab and Github CI/CD pipelines
While docs.veracode.com (formerly known as help.veracode.com) is an excellent resource, it is not the most obviously intuitive tool out there. There’s got to be a

Veracode Webinar – Security scanning in pipelines
Julian (Veracode) and Thomas (Mint Security) show demos and presentations about running Veracode in CI/CD pipelines.





