Similar to last year, we looked at the entire history of active applications, not just the activity associated with the application over one year. By doing so, we can view the full life cycle of applications, which results in more accurate metrics and observations.
The highlights
This blog post is a summary review of what we think is most noteworthy. A download link to the full report can be found at the end of this post.
These are the highligts we want to focus on:
- Microservices
- 3rd party libraries
- Top vulnerability categories
1. Microservices
What defines microservices? They are collections of loosely coupled applications, usually with a small codebase, that communicate via APIs. The advantage of microservices is that it’s easier to work on the various parts of an application if changing one part is unlikely to affect the other bits.
So how might we see this reflected among Veracode users? Well, we’d expect applications to increasingly use one language and become smaller in size.
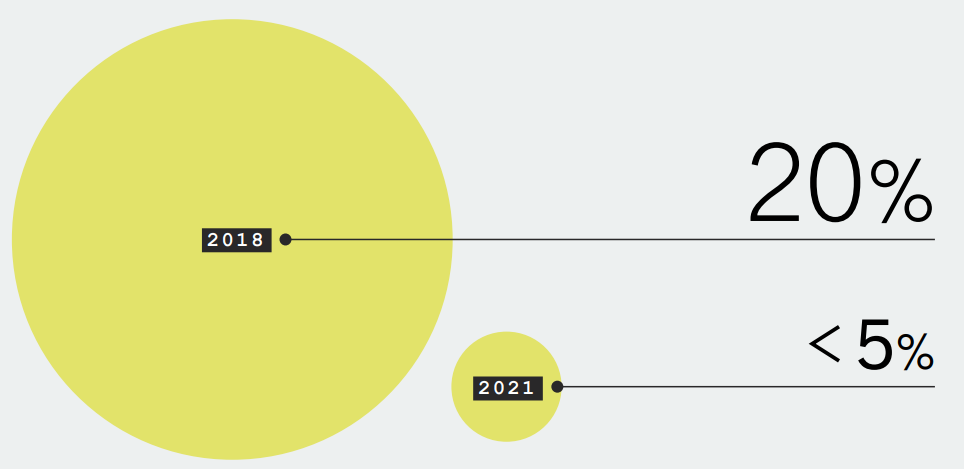
In 2018, roughly 20 percent of applications incorporated multiple languages. This year, less than 5 percent of apps used multiple languages, suggesting a pivot to smaller, one-language applications or microservices.
2. 3rd party libraries
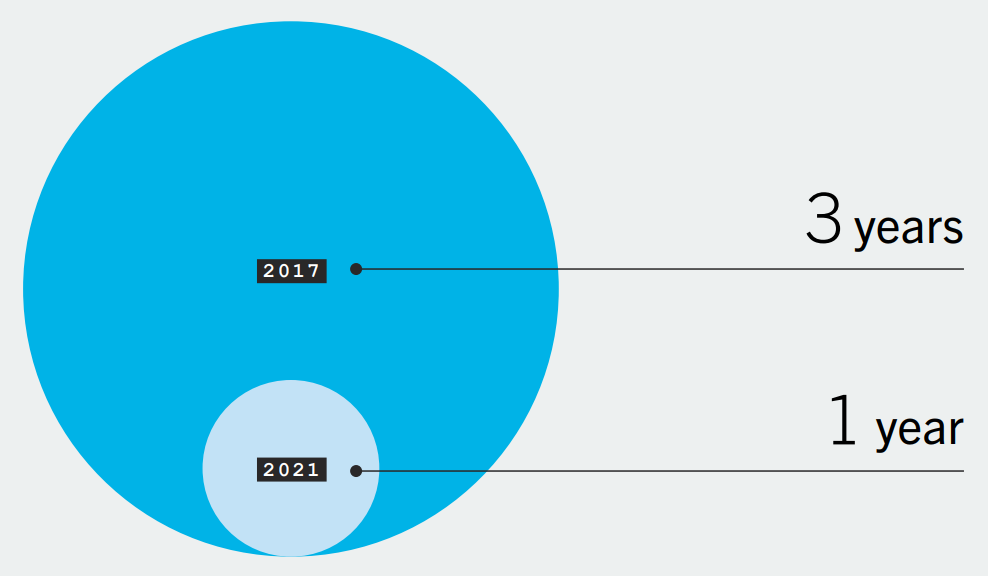
77% of flaws in third-party libraries remain unfixed after three months. On a positive note, there is a noticeable improvement in time to remediation for third-party flaws. Back in 2017, it would take over three years to get to the 50 percent (half-life) closed point, and now it takes just over a year.
There are clear trends for Java, JavaScript, and Python, and that trend is very good, because it goes steeply down. In 2017 nearly 35 percent (on average) of libraries used had a known flaw. In more recent years that has come down to nearly 10 percent. JavaScript has gone from about 10 percent to less than 4 percent, Python from about 25 percent to nearly 10 percent, and Go from 7 percent down to 4 percent.
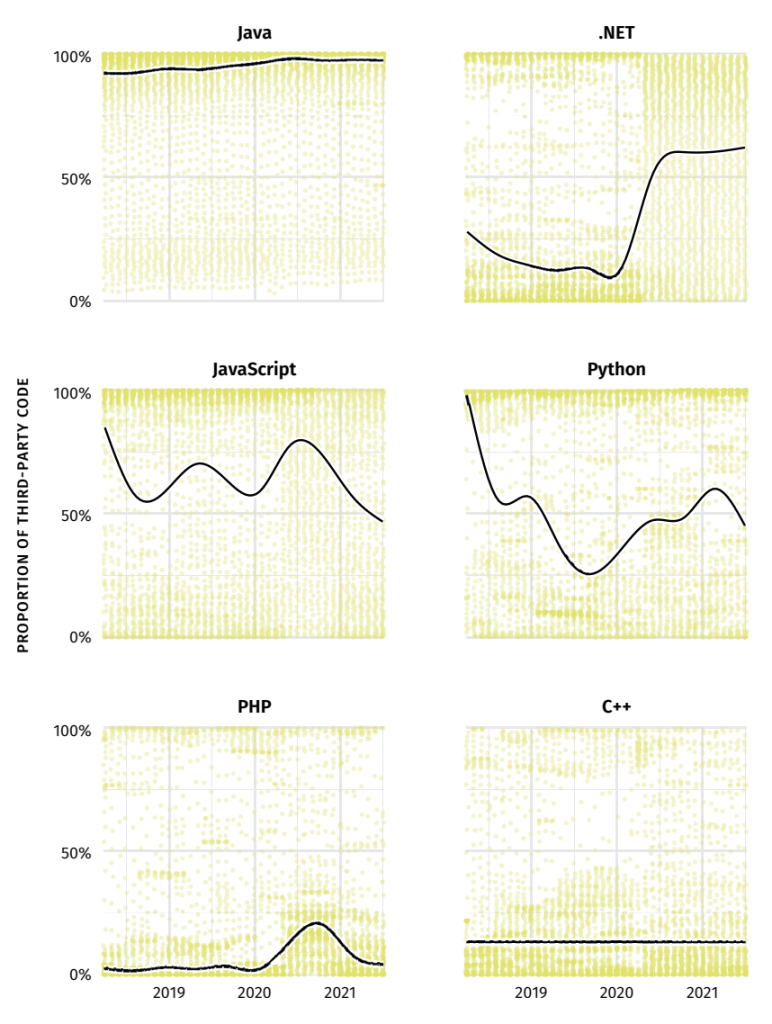
3. Top vulnerability categories
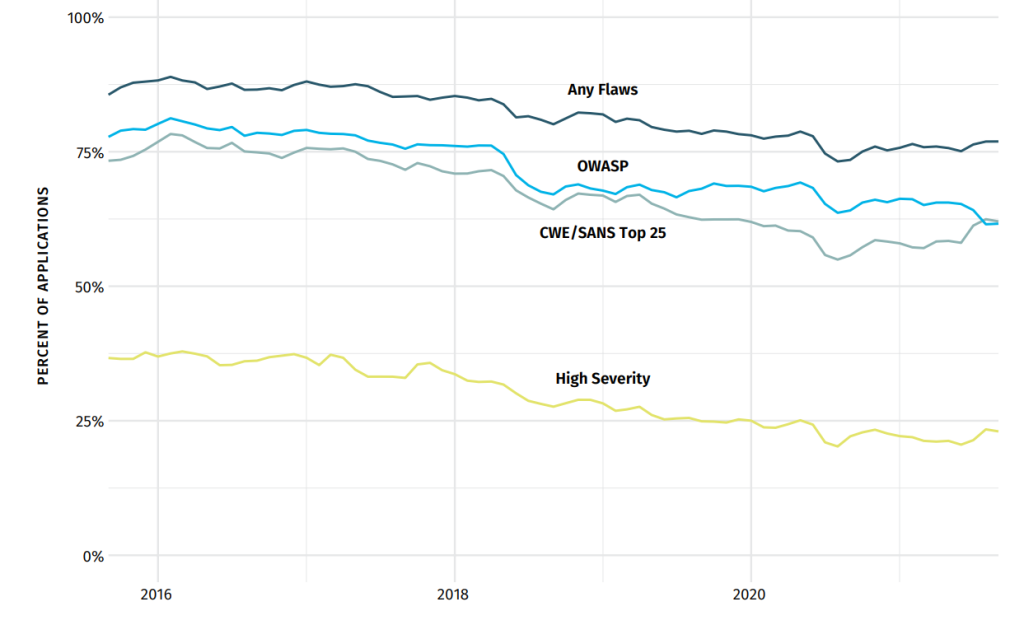
The Flaws of Yesterday Are (Still) the Flaws of Today. Sure, there are variations among languages and things may shift around in prevalence. But by and large, the technical flaws themselves don’t go away, and any changes we do observe tend to evolve slowly. We pulled out the flaws listed in the OWASP Top 10 and CWE/SANS Top 25 and those classified as “High” criticality or above. If you look closely at each of those over time, you’ll notice some peaks and valleys.
But we want you to pull back a bit, and perhaps squint your eyes so that you can see the overall trend in these plots. Notice that, even though the lines may bounce around,they are all slowly decreasing.
Download the full report

Veracode State of Software Security 12
Similar to last year, we looked at the entire history of active applications, not just the activity associated with the application over one year. By doing so, we can view the full life cycle of applications, which results in more accurate metrics and observations.
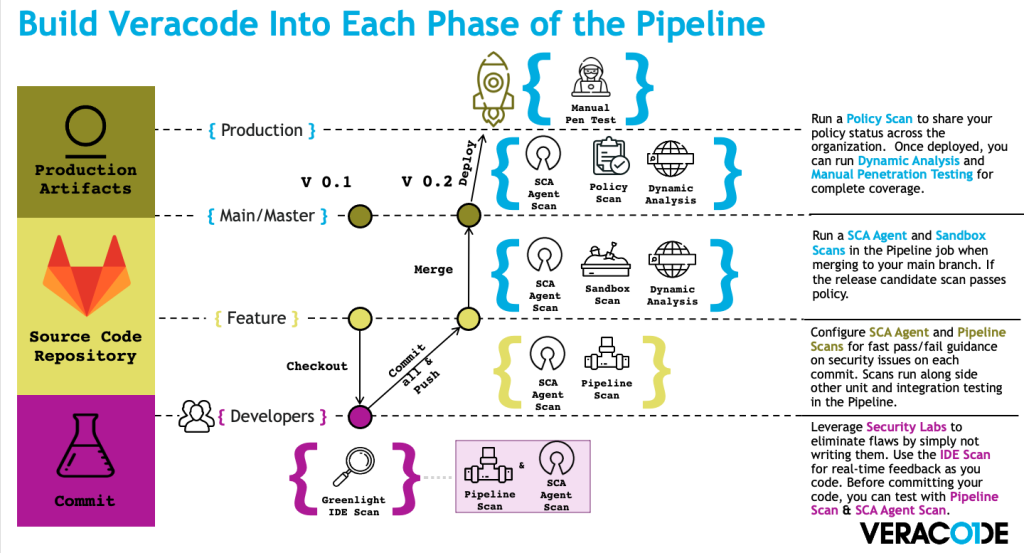
Hands-on Veracode guidelines for Azure, Gitlab and Github CI/CD pipelines
While docs.veracode.com (formerly known as help.veracode.com) is an excellent resource, it is not the most obviously intuitive tool out there. There’s got to be a

Veracode Webinar – Security scanning in pipelines
Julian (Veracode) and Thomas (Mint Security) show demos and presentations about running Veracode in CI/CD pipelines.

Veracode Security Labs Demo
22.09.2020 We at Mint Security wanted to have a look at… We scanned Koronavilkku – these are our findings 30.06.2020 Developers are, in effect, the

We scanned Koronavilkku – these are our findings
We at Mint Security wanted to have a look at the Koronavilkku application and pitch in. The application proved to be of very high quality securitywise. There were no significant security findings.
Veracode Security Labs
Developers are, in effect, the only people in any organization who can fix vulnerabilities hidden in their applications. Veracode Security Labs helps meet the requirements of security standards while providing a meaningful way for the entire development team to learn more.

Integrating Travis CI with Veracode
This blog post will show you how to integrate Travis CI and Veracode. Travis is a cloud based continuous integration (ci) service, that can be used to automate tests and builds for software projects hosted in GitHub.