
Mint Security Oy has achieved ISO/IEC 27001:2022 certification
On December 9, 2024, Mint Security Oy achieved ISO/IEC 27001:2022 certification. With this certification, we want to show that we take the trust our customers

On December 9, 2024, Mint Security Oy achieved ISO/IEC 27001:2022 certification. With this certification, we want to show that we take the trust our customers
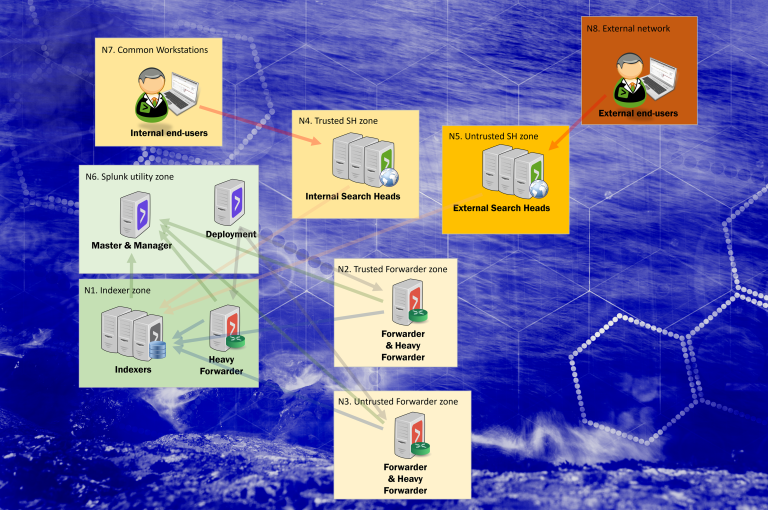
Splunk vulnerability analysis – CVE-2024-29946 & CVE-2024-29945 in relation to a common threat model. DISCLAIMER – The author of this blog shall not be held responsible for any negative outcomes that may occur as a result of following advice given in this blog. Caveat emptor – use advice and ideas presented in this blog at your own risk.

This is a case-study about the certification path of kicker.cloud, a very small startup company, its SaaS product and high ambitions aiming towards a global market. kicker.cloud encountered the same issues so many others have faced before and will in the future – the dreaded procurement Excel-sheets with seemingly endless amounts of security requirements that need to be addressed before any business deals can go ahead.

Splunk Enterprise (on-premises) can be setup in a vast number of ways, including hardening through network segregation. Splunk components chosen in the diagram are there to highlight where and why trust boundaries may or should be implemented.
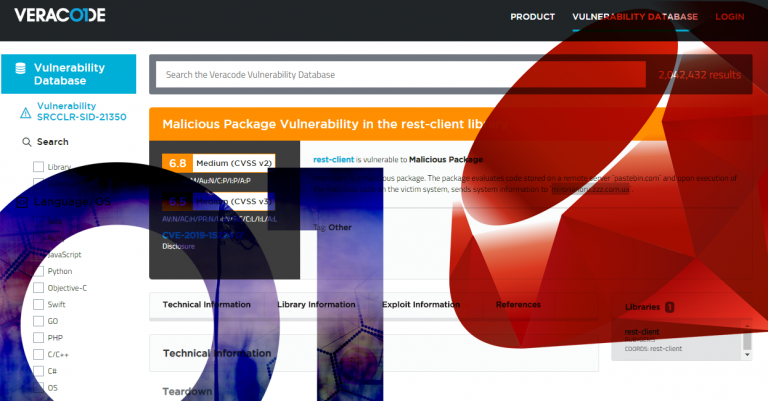
Yhä useampi standardi, viitekehys ja asiakasvaatimus edellyttää – peräti huutaa – kirjastonhallinnan perään. Huutaa siksi että modernit sovelluskehitysmenetelmät ovat täysin riippuvaisia ulkoisista kirjastoista eli riippuvuuksista.

Within the context of ISO 27001, risk comes up as a topic all over the place. The standard itself, as most of ISO standards nowadays
The need for a cyber resilience exercise often starts from interest to gain verified information what each component is capable of — the capabilities, thresholds and baselines of the packet scrubber and other controls. Also, there is a need for training for crisis situations for organizations, as the threats for cyber resilience are on the rise.

Team Mint was founded after a few beers back in 2018. We ride together each year in the Giro d’Espoo event.

Pyöräilykausi 2022 on käynnistynyt ja pari ensimmäistä kotimaista kisaakin on jo käyty. Vähitellen hiipuva koronapandemia ja runsasluminen talvi muokkasivat tiimin talvikauden treenejä hieman aikaisemmasta poikkeavaan muotoon.
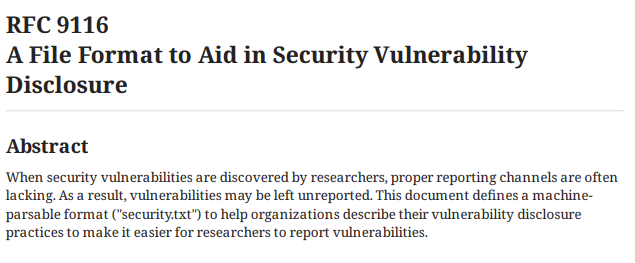
Having a security.txt in the root (/) folder of your website has long been a good practice. The contents of the file has been very free. What started out as a novel and great idea, is now an RFC. Let’s look a bit closer.

The first tasks of vCISO are usually to map the company’s real security needs, get to know the company and its business. A vision of obvious threats and threat models will emerge very quickly, for which rapid solutions can be found through an analytical approach.
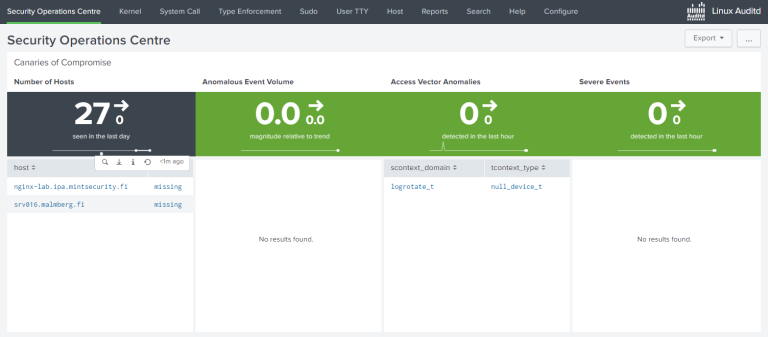
This is a follow-up to my previous blog on Auditd and Splunk. That one was about Defender ATP and Proxmox and license consumption. I did not really touch the subject of a good Auditd baseline configuration.

Similar to last year, we looked at the entire history of active applications, not just the activity associated with the application over one year. By doing so, we can view the full life cycle of applications, which results in more accurate metrics and observations.
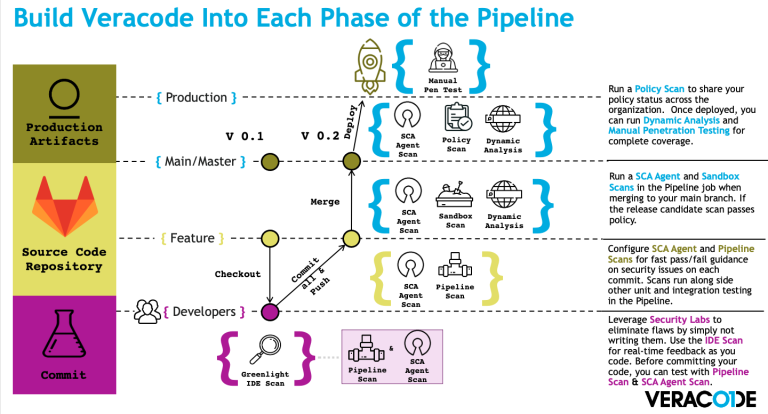
While docs.veracode.com (formerly known as help.veracode.com) is an excellent resource, it is not the most obviously intuitive tool out there. There’s got to be a

This blog post offers a few simple tricks and tips that will ensure that your security controls do not interfere with each other. The tricks are not really tricks, just plain old configurations which offers food for thought. As we know, Splunk is the most complex beast of a software out there.

Julian (Veracode) and Thomas (Mint Security) show demos and presentations about running Veracode in CI/CD pipelines.

22.09.2020 We at Mint Security wanted to have a look at… We scanned Koronavilkku – these are our findings 30.06.2020 Developers are, in effect, the

We at Mint Security wanted to have a look at the Koronavilkku application and pitch in. The application proved to be of very high quality securitywise. There were no significant security findings.
Recon and red teaming can be done separately, but they also work hand in hand. It may be a good idea for a company to do a thorough recon to understand the adversaries view on the organization – and this not only in the technical sense.

The threat landscape is constantly changing as cybercriminals continually try to avoid detection, and increase the number of legitimate resources they can utilize. Recently domain hijacking has become more prevalent. Every day this year, Spamhaus has observed over a 100 hijacked domains at one single domain registrar.

The effects of Corona spares no one. We are all affected, both larger and smaller companies and businesses. As far as the virus goes, we here at Mint are fully operational and workwise the probability of getting sick is smaller than for many others.

Planning for an industry standard compliant information security management system — in brief: carrying out an ISO 27001 project — can break cover from various starting points. Some organizations have already familiarized themselves with the standard, some have even written the first mandatory documents. Yet for many, this article could be the first contact with any form of security work at all.
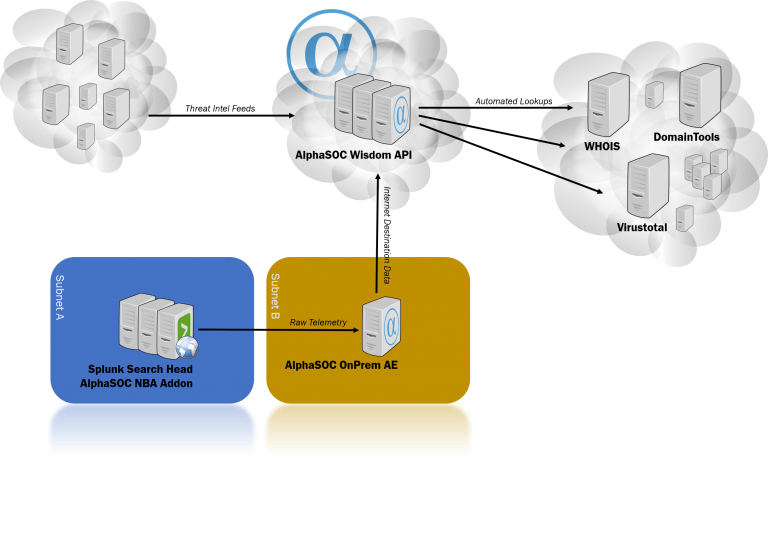
“The cloud!” somebody shouts out loud. “This means my data is sent to the cloud – my precious telemetry data that in the hands of the bad guys could reveal too much about myself!”. This is correct. And for the sake of transparency, let’s have a look at what actually goes on behind the scenes.
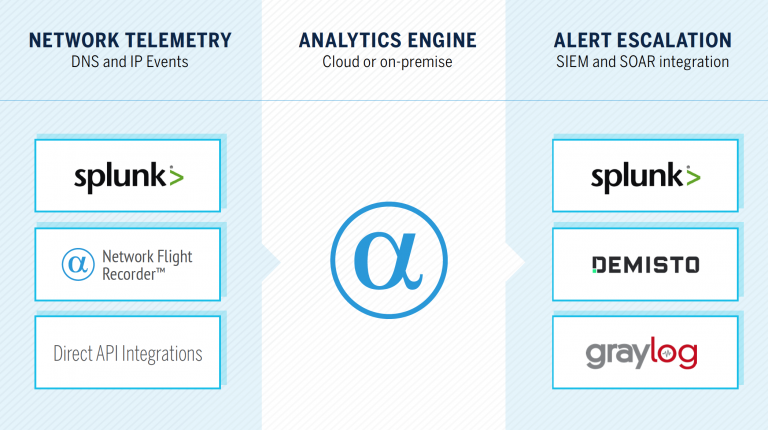
Mint Security will start to resell and support the AlphaSOC product line in Finland and Europe.
Team Mint participated in Helsinki Velotour 2019. As usual Elias and Thomas rode in team colors.

Team Mint participated in Tour de Technopolis 2019. This time Elias and Thomas rode in team colors.
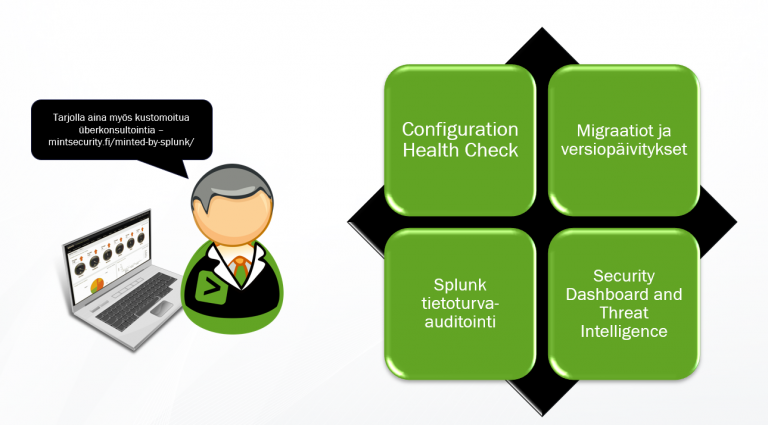
Mint Security tarjoaa Splunkia käyttäville erilaisia lisäarvollisia Splunk konsultointipalveluita jolla saadaan omasta ympäristöstä kaikki irti – turvallisesti.
