The need for a cyber resilience exercise often starts from interest to gain verified information what each component is capable of — the capabilities, thresholds and baselines of the packet scrubber and other controls. Also, there is a need for training for crisis situations for organizations, as the threats for cyber resilience are on the rise.
More visibility into reactions and nonreactions of the service providers are needed, specifically into what triggers alerts, and what does not.
Generally, a growing interest exists in understanding of the breadth of impact of DDoS attacks and how they are realized in the applications and infrastructure of the target organization.
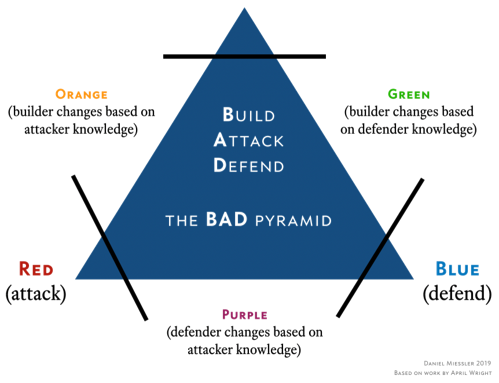
DDoS Purple Teaming in brief
Purple is a cooperative mindset between attackers and defenders working on the same side. Purple should be thought of as a function rather than a dedicated team. Purple Teams exist to ensure and maximize the effectiveness of the Red and Blue teams. They do this by integrating the defensive tactics and controls from the Blue Team with the threats and vulnerabilities found by the Red Team into a single narrative that maximizes both.
DDoS testing is (not) dead, long live DDoS testing!
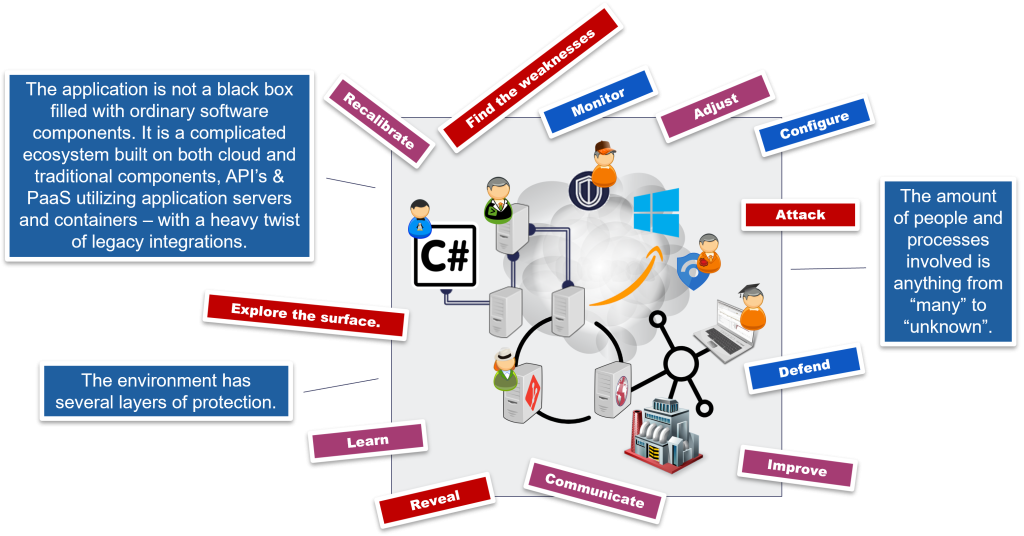
Traditional DDoS-testing mostly focuses on verifying technical capabilities, with focus on the DDoS packet scrubber. Traditional testing is able to find weaknesses in thresholds and detection patterns and improve the way we mitigate large scale bulk attacks like UDP and ICMP floods.
But it often happens, that an application is not just a black box full of conventional software components. It is a complex ecosystem built using both cloud and traditional components, using and providing API interfaces and PaaS platforms with application servers that make use of containers… And also legacy integrations with a heavy twist. Protection of the application is set at several different levels — and a modern distributed denial of service attack can be targeted on any of those levels.
Who should be involved?
Business Owners
Infosec
Cloud Operators
Service Teams
SOC Personnel
Product Owners
Development Teams
Turn-key delivery of DDoS Purple Teaming
We create ideas that fit the target environment perfectly, planning and coordinating the exercise from start to finish. We survey and chart the target environment and model it with sufficient accuracy. We design the test cases and implement them. We also have know-how of how to comprehensively manage exercise’s risks and threats.
If necessary, we produce an executive summary for the top management and assist with selling internally. Our experts are experienced and each of them has been properly trained to use the RedWolf DDoS platform.
After the implementation, we provide technical and actionable reporting, and also offer post-exercise consultation according to the customer’s needs.