
ISO 27001 – A practical path for leaders who want more than a certificate
Most ISO 27001 projects stop at “pass the audit.” That’s fine when the only goal is a certificate. However, this approach leaves a lot of

Most ISO 27001 projects stop at “pass the audit.” That’s fine when the only goal is a certificate. However, this approach leaves a lot of

APIs are the backbone of modern businesses, facilitating seamless data exchange between applications, customers, and partners. But just like an airport without security checkpoints, unprotected

In the digital age, businesses rely heavily on their networks to function efficiently. However, managing and maintaining a complex network can be a daunting task. By implementing effective network management best practices, organizations can ensure optimal performance, enhance security, and minimize downtime.

In the ever-evolving landscape of cybersecurity, staying ahead of sophisticated threats demands innovative solutions. One such game-changer is NetFlow, a technology that unlocks a treasure trove of network traffic data. By leveraging NetFlow, organizations gain the upper hand in safeguarding their networks and detecting potential threats.
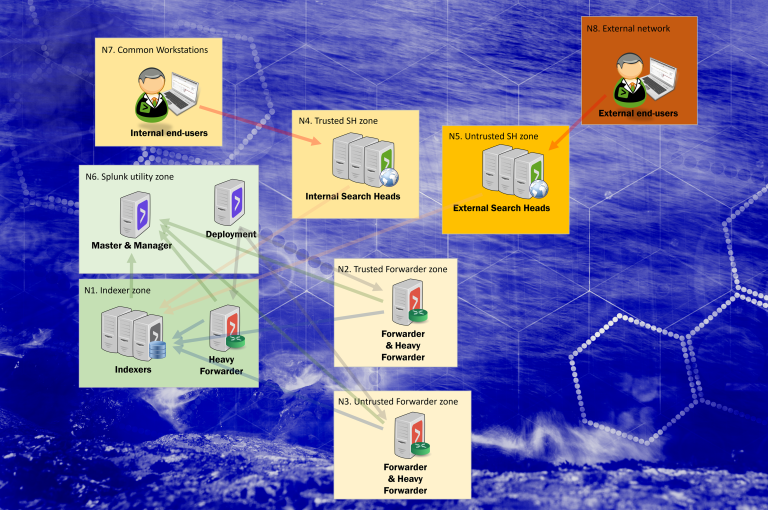
Splunk vulnerability analysis – CVE-2024-29946 & CVE-2024-29945 in relation to a common threat model. DISCLAIMER – The author of this blog shall not be held responsible for any negative outcomes that may occur as a result of following advice given in this blog. Caveat emptor – use advice and ideas presented in this blog at your own risk.

This is a case-study about the certification path of kicker.cloud, a very small startup company, its SaaS product and high ambitions aiming towards a global market. kicker.cloud encountered the same issues so many others have faced before and will in the future – the dreaded procurement Excel-sheets with seemingly endless amounts of security requirements that need to be addressed before any business deals can go ahead.

Splunk Enterprise (on-premises) can be setup in a vast number of ways, including hardening through network segregation. Splunk components chosen in the diagram are there to highlight where and why trust boundaries may or should be implemented.
Yhä useampi standardi, viitekehys ja asiakasvaatimus edellyttää – peräti huutaa – kirjastonhallinnan perään. Huutaa siksi että modernit sovelluskehitysmenetelmät ovat täysin riippuvaisia ulkoisista kirjastoista eli riippuvuuksista.

Within the context of ISO 27001, risk comes up as a topic all over the place. The standard itself, as most of ISO standards nowadays

As part of the ISO/IEC 27001 certification process, organizations must conduct regular internal audits to ensure compliance and identify areas for improvement. One common dilemma faced by businesses is whether to conduct these audits internally or engage an external company to do it.
The need for a cyber resilience exercise often starts from interest to gain verified information what each component is capable of — the capabilities, thresholds and baselines of the packet scrubber and other controls. Also, there is a need for training for crisis situations for organizations, as the threats for cyber resilience are on the rise.

Cloud Scanning -toiminto on Holm Securityn haavoittuvuuksienhallinnan uusi ominaisuus, joka automatisoi riskien tunnistamisen pilvi-infrastruktuureissa. Uusi toiminto kattaa Infrastructure as a Service (IaaS), Software as a Service (SaaS) ja Platform as a Service (PaaS) -palvelumallit.
Having a security.txt in the root (/) folder of your website has long been a good practice. The contents of the file has been very free. What started out as a novel and great idea, is now an RFC. Let’s look a bit closer.

The first tasks of vCISO are usually to map the company’s real security needs, get to know the company and its business. A vision of obvious threats and threat models will emerge very quickly, for which rapid solutions can be found through an analytical approach.

Segregation of duties in ISO 27001 refers to all practices where information and/or privileges required to carry out a certain process are broken into fragments. The fragments are then distributed among multiple persons or roles in such a way that a single person alone cannot perform or fully control that particular process.
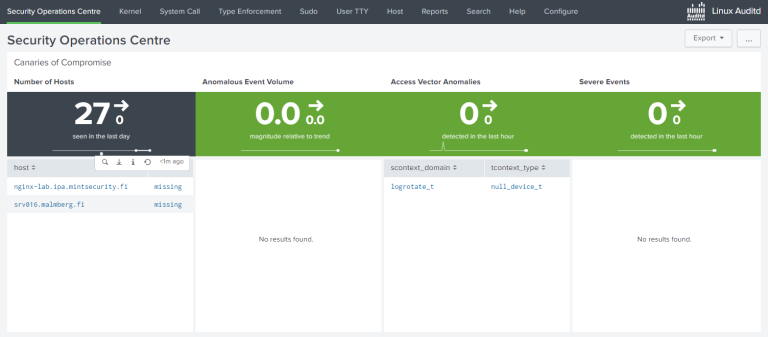
This is a follow-up to my previous blog on Auditd and Splunk. That one was about Defender ATP and Proxmox and license consumption. I did not really touch the subject of a good Auditd baseline configuration.

Similar to last year, we looked at the entire history of active applications, not just the activity associated with the application over one year. By doing so, we can view the full life cycle of applications, which results in more accurate metrics and observations.
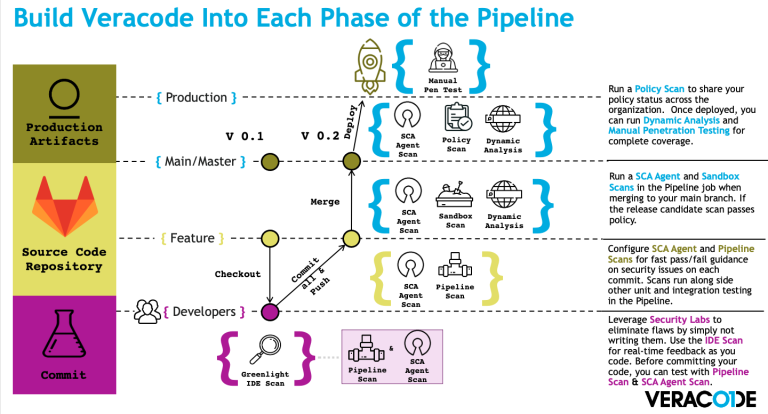
While docs.veracode.com (formerly known as help.veracode.com) is an excellent resource, it is not the most obviously intuitive tool out there. There’s got to be a

The average life expectancy of an ISO standard is about five years, at a time. When the hourglass has run out of sand, a voting will take place to decide whether to maintain the ISO standard as-is, revise it or withdraw the standard altogether.

This blog post offers a few simple tricks and tips that will ensure that your security controls do not interfere with each other. The tricks are not really tricks, just plain old configurations which offers food for thought. As we know, Splunk is the most complex beast of a software out there.
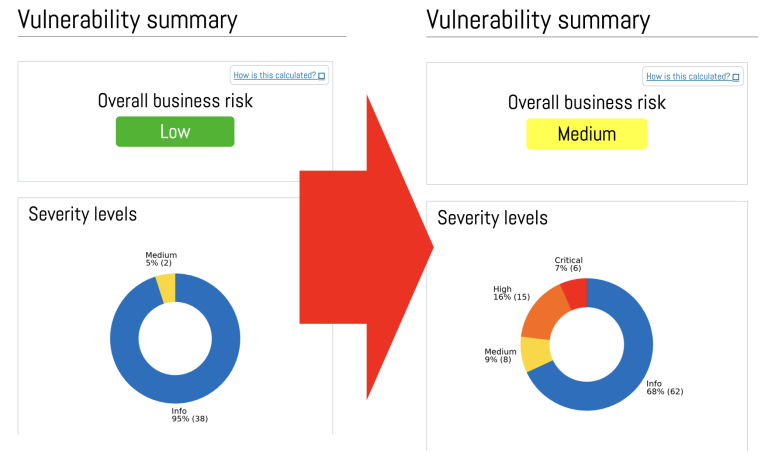
When vulnerabilities are scanned from the perspective of an outside attacker and without actually logging in to the target system(s), only a limited and narrow picture of exposure to threats can be found. For a better picture, it is a good idea to log in with the right kind of credentials.

Today at AlphaSOC we released Network Flight Simulator (flightsim) 2.2.1, which is our free, open source adversary simulation tool. This latest release includes a number of new modules that security teams can use to instantly evaluate detection and response coverage within SIEM and SOAR tools.

To fulfill the training requirements of ISO 27001, the organization must identify what the staff need to learn, train the staff and measure the training’s effectiveness. KnowBe4 is the first and largest next-generation security training and phishing simulation platform. It’s built to be user-friendly and highly intuitive to help busy IT professionals — who have a lot of stuff on their plate already, on an ongoing basis.

All organizations are unique in their security needs and capabilities, and ISO 27001 does not seek to change that fact. The standard guides the adoption of appropriate processes and practices to improve, clarify, and maintain information security as an integral part of day-to-day operations.

Julian (Veracode) and Thomas (Mint Security) show demos and presentations about running Veracode in CI/CD pipelines.

Do you need independent experts’ assessment of the general security aspects of your application or system? How about a comparable benchmark for the level of your application’s overall security practices?

Do you seek ISO 27001 compliance? Thomas has blogged about starting points for ISO 27001 certification project. This blog unwraps the importance of risk management in pursuit of ISO 27001 certification.
