Properly governing information security involves more than writing down policies and procedures somewhere. The implementation of documented information requires maintaining awareness and provision of security training for all personnel. Timing is also important – a classic mistake is to publish all instructions at once. For example, 25 new security policies and procedures on the same day.
From a historical standpoint, security awareness training has been seen more as a compliance-fulfilling activity instead of a real information security control. Over the course of time, however, as cyber threats evolve and get more complicated, this is no longer the case.
ISO 27001 requirements
According to the ISO 27001 information security standard, all employees of the organization and, where relevant, contractors must receive appropriate awareness education and training and regular updates in organizational policies and procedures, as relevant for their job function.
Promoting awareness is important in order to establish a culture of information security within an organization, and to ensure that information security doesn’t end up as a dotted function for a small group of people — but rather as a source from where everyone can adopt infosec wisdom into their own work and contribute e.g. valuable observations back to the security team.
Additionally, ISO 27001 requires the organization to:
- identify and define the required knowledge and skills for each role or personnel group relevant to the information security management system (ISMS)
- organize and conduct training to achieve defined knowledge and skills
- measure whether each individual has reached the desired level of defined knowledge and skills (e.g. through tests or interviews)
All of the above measures are aimed at keeping organization’s confidential information secure.

Phishing the way into networks and systems
Over the years, malicious attackers have been looking for new ways to gain access to organizations’ networks and access to their confidential information. SQL injections have dominated the top spot for such statistics, as the means to an end. Recently, companies have been plagued by attacks conducted using remote assistance software. But one attack vector has remained tightly known to the forefront of these questionable race statistics, for a long time: phishing.
The purpose of phishing is to trick the victim into believing that a message contains something that the victim wants or needs — a request from the bank or instructions from another person working for the company. “Click the link, open the attachment.”
Attackers’ goal is most often to obtain usernames, passwords, and account or other financial information. The list of consequences to a business following an attack is long and notorious.
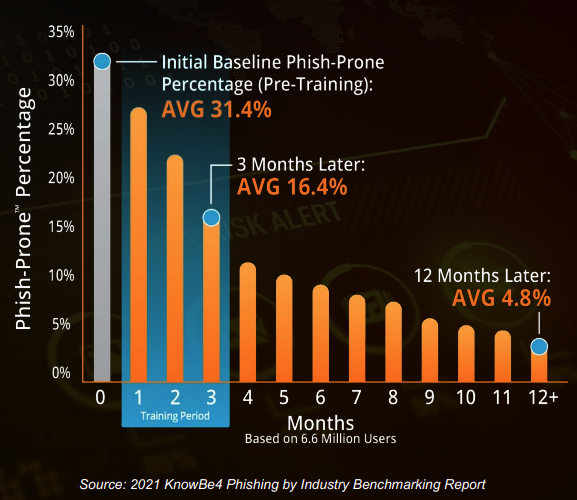
Successful phishing may result in:
- identity theft
- theft of sensitive data
- theft of client information
- loss of intellectual property
- theft of funds from business and client accounts
- reputational damage
- unauthorized transactions
- credit card fraud
- installation of ransomware and malware
- access to systems to launch new attacks
- data being sold to espionage organizations, competitors and criminals
KnowBe4 helps you to protect and meet ISO 27001 requirements
To fulfill the training requirements of ISO 27001, the organization must identify what the staff need to learn, train the staff and measure the training’s effectiveness. Sensitive information will be accessed and used in a variety of ways across the organisation. Each of these ways must be accounted for and take note of the knowledge and skills that are required to stay secure. Phishing a common nominator in many of these ways and cases.
Scanning incoming e-mails, filtering DNS queries and securing endpoints are all good ways to reduce the risk of being hacked. Training adds a layer of protection, which utilizes humans as an additional security mechanism. By giving users information about what phishing attacks look like, they can more easily detect scams without compromising the organization.
KnowBe4 platform
KnowBe4 is the first and largest next-generation security training and phishing simulation platform. It’s built to be user-friendly and highly intuitive to help busy IT professionals — who have a lot of stuff on their plate already, on an ongoing basis.
Users of information systems need to be trained — but the boring, “old schoold security training” no longer helps in responding to modern threats. Employees are increasingly exposed to advanced phishing and ransomware attacks.
KnowBe4 platform combines all of it’s functions into one easy-to-use interface. It allows starting training campaigns and simulated attacks in just a few minutes. Templates, landing pages, and simulated attachments can be freely edited, as well as spoof your own domain for simulated CEO fraud attacks using response tracking.
But we already have our own training videos?


KnowBe4
Human Error. Conquered. Phishing simulations. Security Training. KnowBe4 enables your employees to make smarter security decisions, every day KnowBe4 is the world’s largest integrated Security

KnowBe4 and ISO 27001
To fulfill the training requirements of ISO 27001, the organization must identify what the staff need to learn, train the staff and measure the training’s effectiveness. KnowBe4 is the first and largest next-generation security training and phishing simulation platform. It’s built to be user-friendly and highly intuitive to help busy IT professionals — who have a lot of stuff on their plate already, on an ongoing basis.

Nyt on oikea hetki rakentaa “inhimillinen palomuuri”
Kun tarkastellaan yrityksen tai organisaation kyberturvallisuustrategiaa, on siihen nykyään myös sisällytettävä yrityksen työntekijät, jotka ovat kyberpuolustuksen ns “inhimillinen osatekijä” (human element). Voidaan varmaan olettaa, että