
Our approach

Examples of questions and claims in a Security Review:
- Is the need for elevated privileges (including administrator/root accounts and other special privileges) listed by each system, and the necessary individuals identified?
- On what grounds are special access rights granted?
- Can a user perform their normal duties using their username, with elevated privileges?
Security Review — from start to finish
We prepare for Security Review by identifying — together with the client — the most relevant target areas (e.g. cloud infrastructure, logging and monitoring, information security for personal data processing), selecting appropriate frameworks, and formulating the interview questions.
We will determine the preliminary material and documents of the interview that the client may need to provide and get acquainted with the material. The selected questions and claims are provided to the client before the actual interview session, so that the session would be as smooth as possible and the both parties have been given a good chance to prepare.
When we’re ready for the interview, it’s go time! Using Teams or a real conference room. We ask our questions, ask for evidence and talk the necessary, clarificationary discussions.
At the end of the project, we submit our report and then review it together with the customer. In the interviews we use the language best suited to the client and produce the final report in English.
The report includes, for example:
- recommendations for found flaws and topics
- alignment of recommendations to appropriate frameworks
- most important processes that are missing or in need of improvement
- documents that are missing or in need of improvement
- used and proposed security indicators
- next steps to compliance, from a technical and administrative point-of-view


Auditing
Auditing Auditing in short Auditing means many things. For us, it means customized reviews of systems, environments and processes for our customers. In addition to
Red Teaming and Recon
Recon and red teaming can be done separately, but they also work hand in hand. It may be a good idea for a company to do a thorough recon to understand the adversaries view on the organization – and this not only in the technical sense.
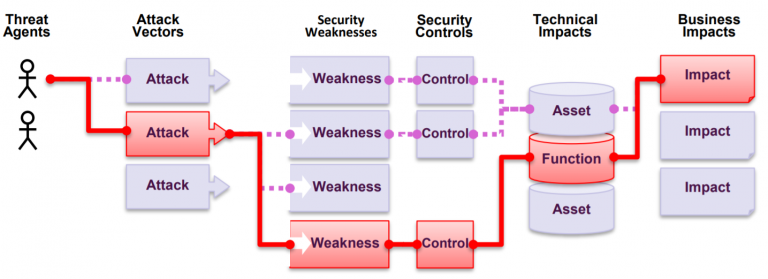
What is pentesting?
A common tool used to assess the security of a web application is penetration testing. Known also as pentest. Pentest is a “legal” simulated attack that seeks to use an application in a way that could be harmful to either the system, the data in the system, or the people who use the system.





