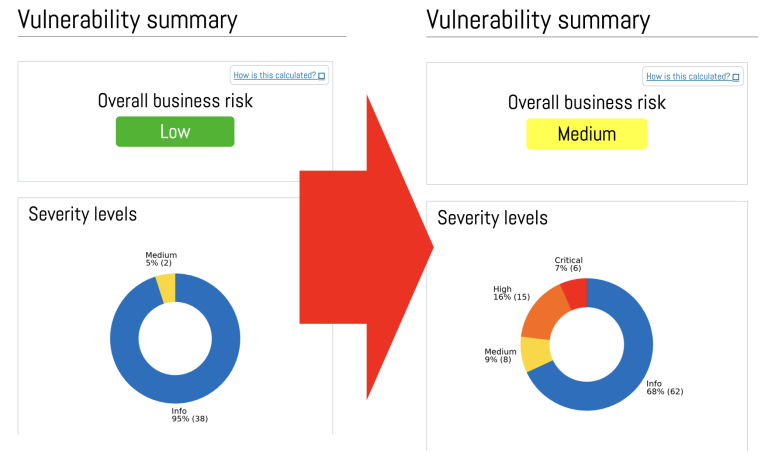
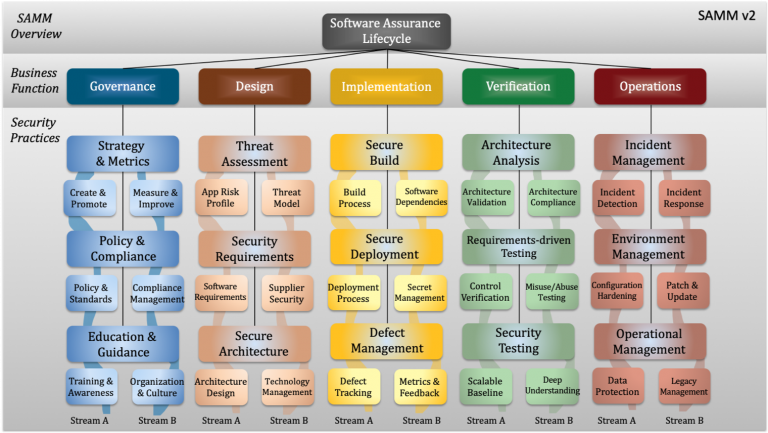
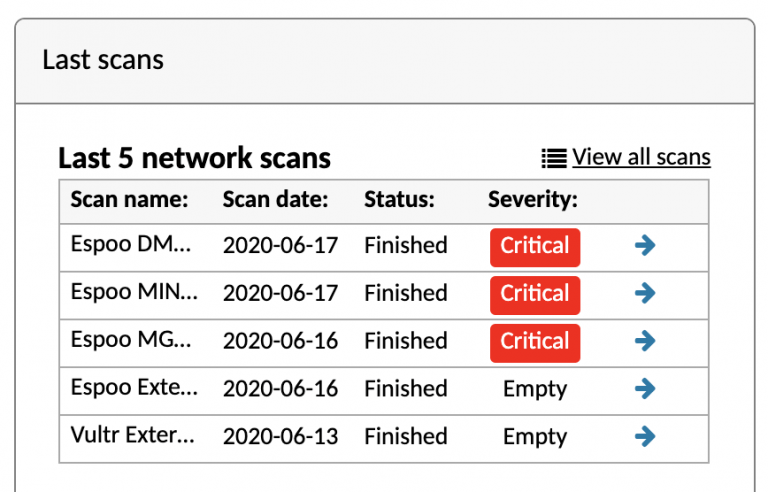
Internal audit – Using internal or external resources?
As part of the ISO/IEC 27001 certification process, organizations must conduct regular internal audits to ensure compliance and identify areas for improvement. One common dilemma faced by businesses is whether to conduct these audits internally or engage an external company to do it.